Optimize your stack for cloud-first access flows that enable SOC 2 Compliance
Apono provides continuous visibility to cloud access, uncovers over-privileges, and suggests on-demand access flows to remove standing privileges.
Public cloud permissions have emerged as the first line of defense. Managing privileged access effectively can deliver on regulatory compliance and prevent compromised account access.
Apono ensures machine identities and human accounts receive just the right permissions they need just in time to get the job done without compromising on regulatory compliance requirements.
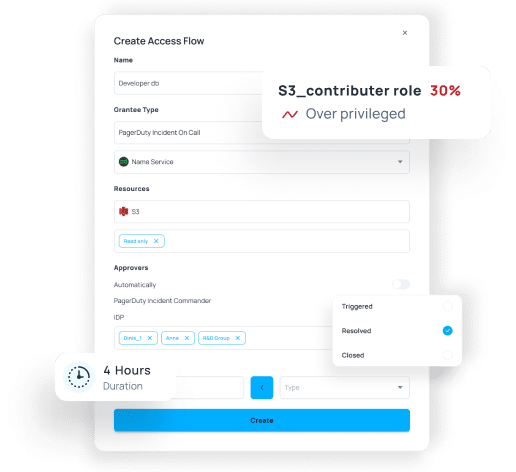
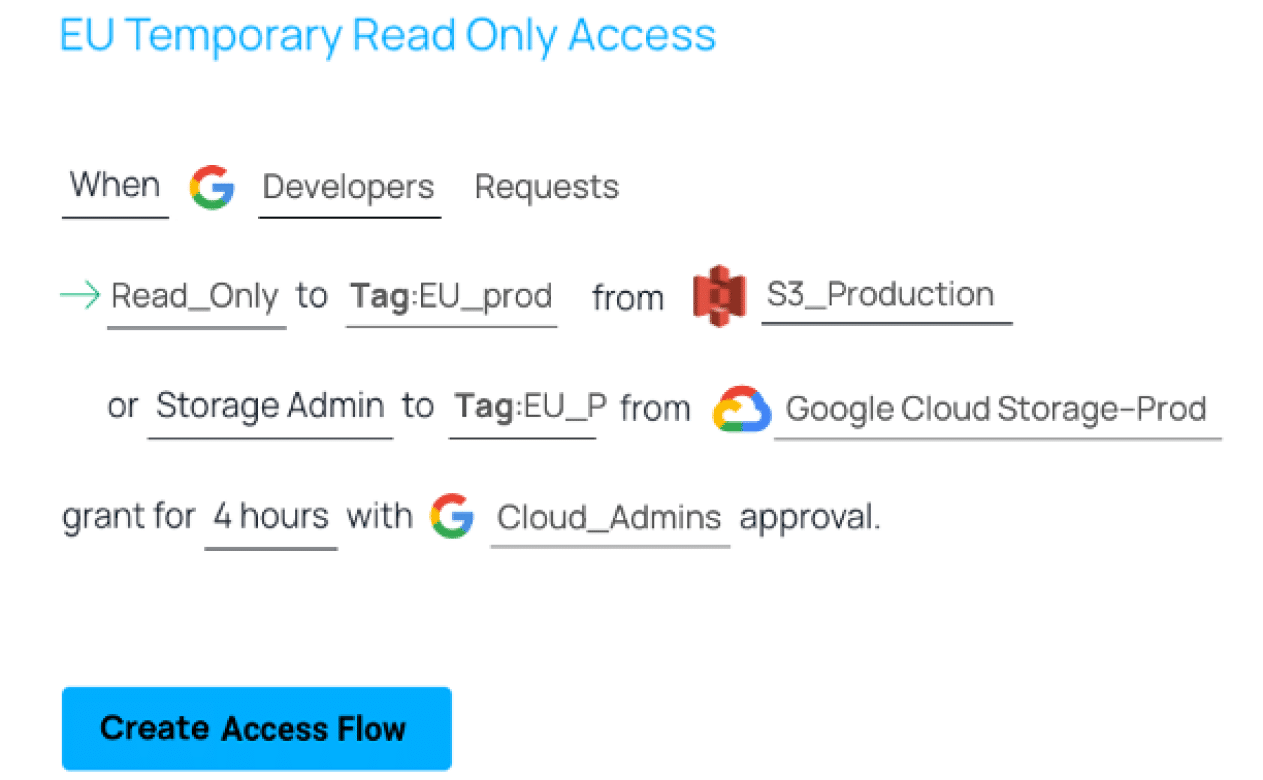
Optimizing for cloud access flows delivers on “Just-In-Time” and “Just Enough” granularity, enabling DevOps teams to keep working with the existing tech stack.
When using Apono to manage permissions for shared credentials among your users. Solving the root cause of credential sharing by simplifying access flows that grant users short-lived credentials.
Providing 1:1 identity to credential mapping in every resource and data repositories automatically.
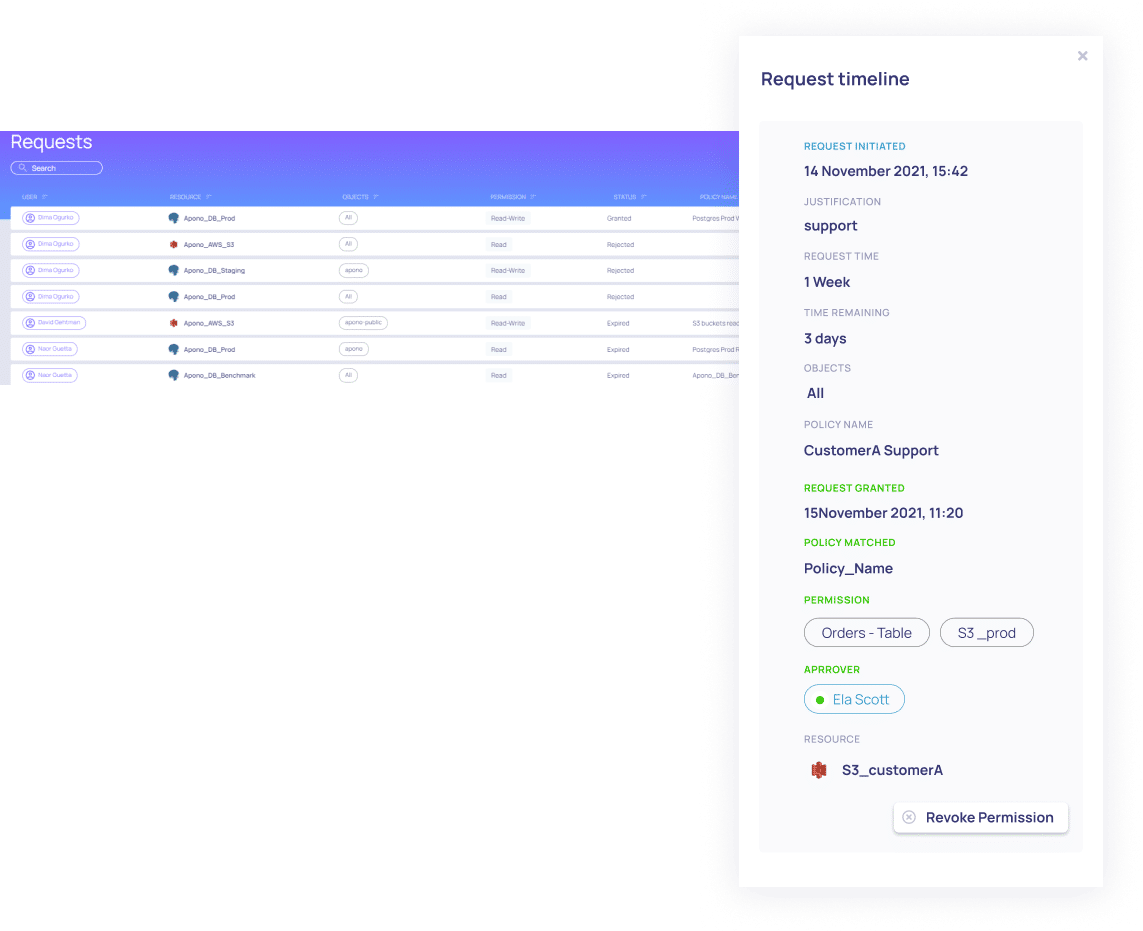
Permissions are your last line of defense, Apono assures standing privileges are never risking your organization.
Integrates with your existing stack, so you don’t need to make any changes when you start using Apono.
Utilize ChatOps with automated approval
workflows.
Choose to use the Apono CLI or any other client application that you prefer.
















