Redefining Privileged Access
The Apono Privileged Access Platform eliminates standing permissions to secure humans, machines, and agents, providing seamless secure access to cloud, data, and infrastructure.
Work in the cloud is dynamic and so is access
Continuously
-
JITP
-
Modern PAM
-
Cloud IGA
-
Break-Glass
-
Ensure Compliance
-
Secure DB Access
-
ATDR
-
ZSP
Just-in-Time and Just-Enough Privileges
Reduce your access risk by 95%. Remove standing access and prevent lateral movement in your cloud environment.
Learn more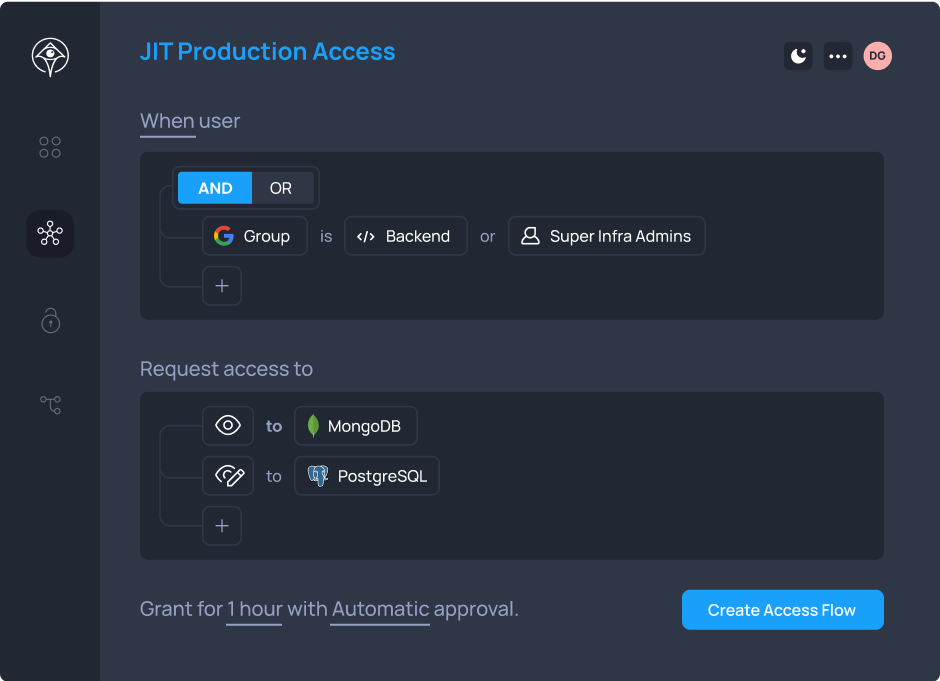
Cloud Privileged Access
By implementing Modern PAM, organizations can enforce strict authentication, authorization, and audit controls for these high-level accounts, reducing the risk of insider threats, data breaches, and unauthorized access.
Learn moreCloud Identity Governance
Cloud Identity Governance offers a robust solution, seamlessly managing access across your entire ecosystem. Effortlessly control who sees what, when, and how – all while staying compliant.
Learn more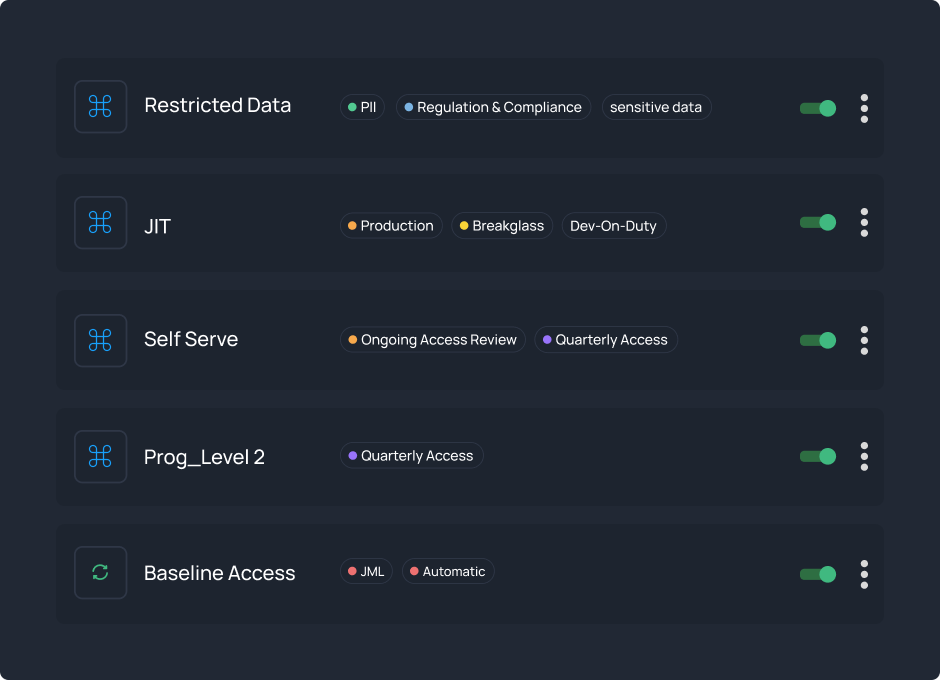
Break-Glass
Instead of having always-on access, developers request access to the production environment on a need-to-use basis, which is then approved for a limited duration. This minimizes the exposure of critical infrastructure by reducing the attack surface, lowering the risk of insider threats, and ensuring tighter control over who can access key resources.
Learn more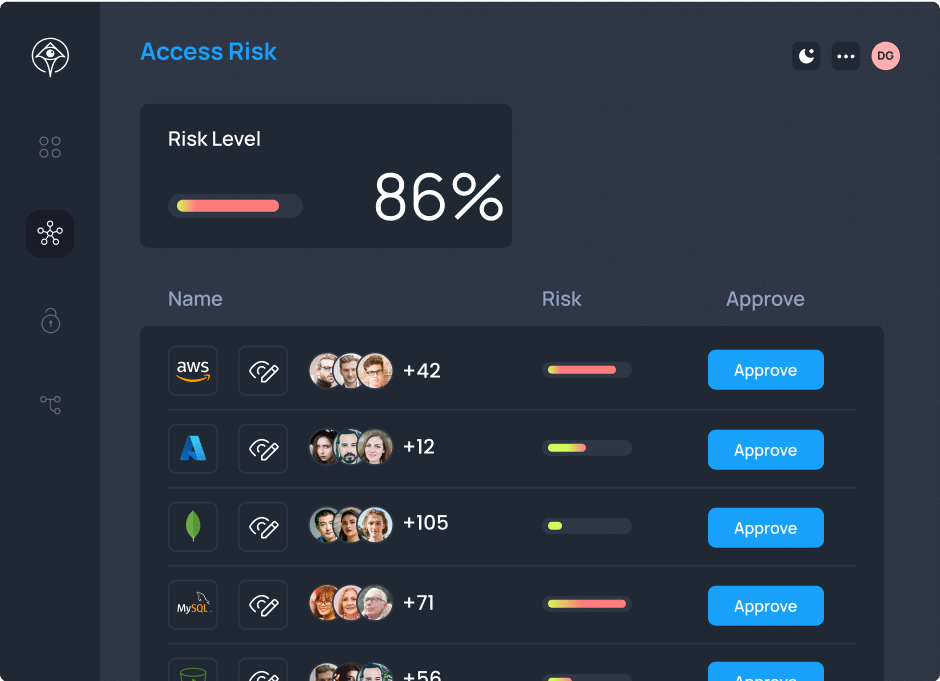
Ensure Compliance
Apono automates access control processes, enforcing role-based access, and ensuring the principle of least privilege. It maintains detailed audit logs, simplifying compliance audits for standards like SOC 2, ISO 27001, and HIPAA. The platform supports segregation of duties (SoD) and enables efficient access reviews and certifications, ensuring that permissions align with regulatory requirements such as GDPR and CCPA.
Learn moreSecure Database Access
By streamlining and automating the process of managing user permissions and access controls, Apono helps secure your database access. This ensures that users have the right level of access to databases by enforcing the principle of least privilege, granting access only when necessary and for a limited time.
Learn more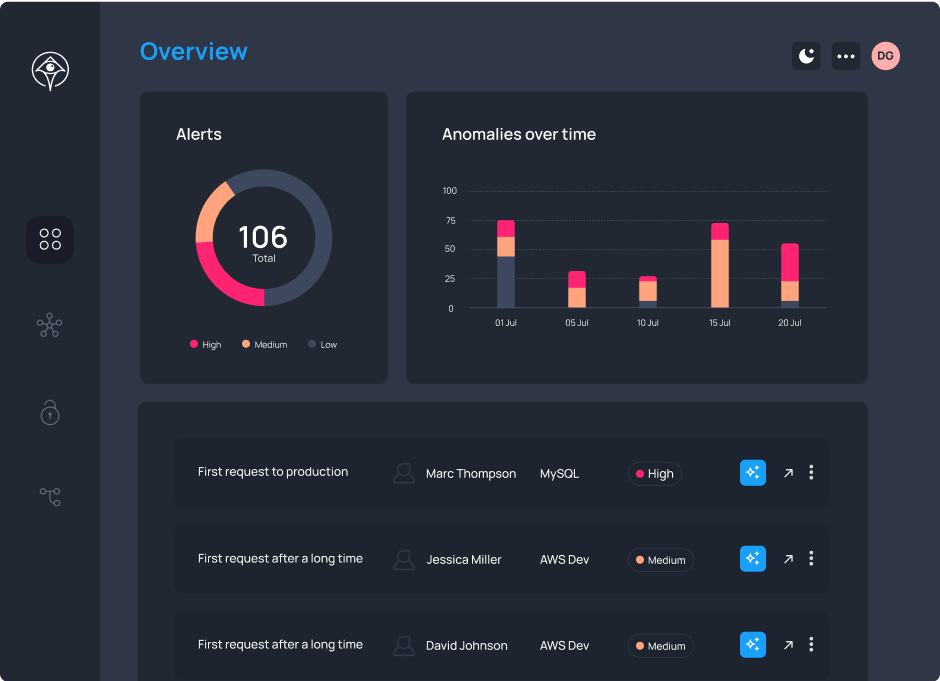
Access Threat Detection & Response
Effective detection and response systems are crucial for reducing data breach risks, safeguarding sensitive data, and ensuring compliance. Granular access controls limit unauthorized access, giving users only necessary privileges. Integration with SIEM and monitoring tools enables quick detection and response to suspicious activities.
Learn more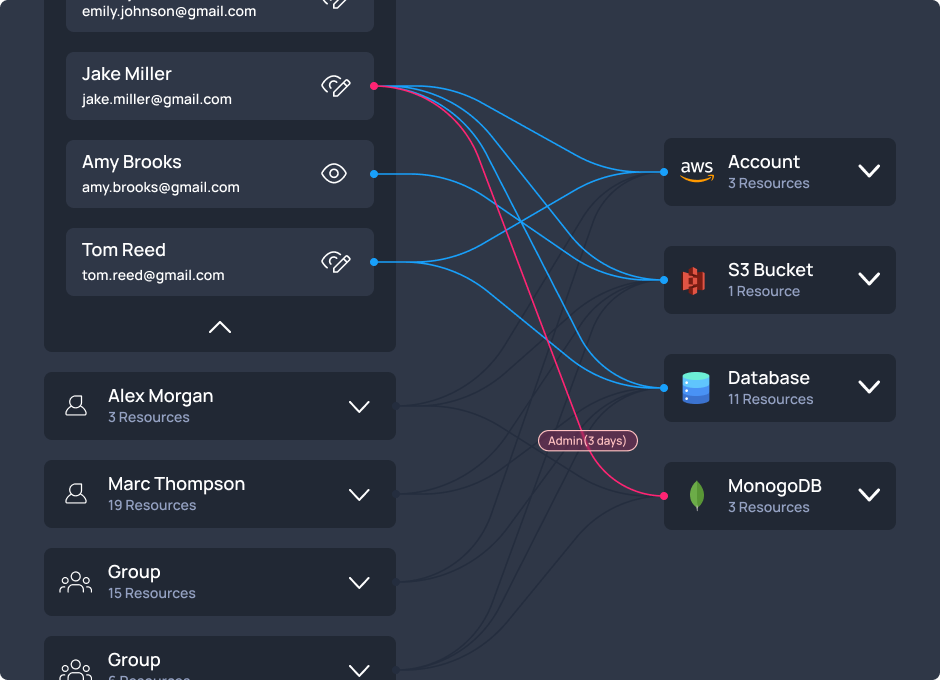
Achieve Zero Standing Privilege
In traditional environments, users often have static access permissions, which increases the risk of misuse or compromise over time. Zero standing privileges shift this paradigm by ensuring that no user or service has continuous access; instead, access is granted on a just-in-time basis when needed.
Learn more
