Just-in-Time Access to MongoDB
Apono works with MongoDB to make your infrastructure easy to access, manage, and audit. Apono empowers you to craft dynamic Access Flows, providing on-demand permissions with meticulous granularity and comprehensive audit capabilities.

MongoDB is a popular open-source NoSQL database management system that falls under the category of a document-oriented database. It is designed to store, query, and process large amounts of data in a flexible, schema-less format. MongoDB is known for its scalability, high performance, and ease of use, making it a popular choice for developers and organizations working with diverse and evolving data.
Just-in-time (JIT) access involves assigning permissions to users or systems in real-time as needed, rather than maintaining continuous access. This strategy is frequently employed in cybersecurity to reduce the risk of security breaches by restricting unnecessary access. It aligns with the principle of least privilege (polp), emphasizing that users should only have the minimum access levels required to fulfill their tasks
MongoDB Use Cases
Developer JIT Access
- Limit access to the minimum required permissions and implementing strict controls on when those permissions are granted, JIT access helps enhance overall security. This proactive approach reduces the risk of unauthorized access and potential security breaches.
- Integrate JIT access with your incident response plan. In the event of a security incident, having the ability to quickly adjust access permissions can be crucial for containing and mitigating the impact.
- Utilize JIT access with your identity management systems. This integration streamlines the process of aligning access permissions with changes in user roles, making it more efficient and less prone to errors.
 MongoDB_Prod
MongoDB_Prod  MongoDB
MongoDB Secure Break-glass Access
- Manage break-glass access, balancing the need for emergency access with the imperative of maintaining robust security measures.
- Implement robust logging and monitoring systems to track and record break-glass access events.
- Dynamically grant only the permissions needed for the task at hand to prevent costly mistakes in production and downtime.
 Developer_on_Duty
Developer_on_Duty  MONGODB_Prod
MONGODB_Prod Automated Access
- Escape the frustration of ticket fatigue and the time-consuming nature of manual provisioning through the implementation of automated access flows.
- Embrace innovation to revolutionize your workflow, saving time and resources, enhancing efficiency, and ensuring a secure access management system.
- Automate your access control and witness a transformative shift in permission allocation within your organization.
 MongoDB_Prod
MongoDB_Prod  MongoDB
MongoDB Apono automates access management to MongoDB. Apono empowers you to craft dynamic Access Flows, providing on-demand permissions with meticulous granularity and comprehensive audit capabilities.
Automated Database Permissions Approval Workflows
Align the access approval workflow with meticulously defined organizational permission guardrails to enhance precision and efficiency, fortifying overall security posture. This methodical approach ensures a seamless and compliant framework, maintaining heightened control over critical resources.
Granular MongoDB Database Access
Define MongoDB database and collection permissions as fine-grained as necessary.
Tailored Production Engineer Access
Implement a tailored approach to permissions management by ensuring that access to sensitive resources is precisely calibrated to the specific needs and responsibilities of each user or system. This involves meticulously providing right-size permissions, aligning with the principle of least privilege. By adopting this meticulous strategy, you not only enhance the overall security posture of your system but also minimize the potential risks associated with excessive or insufficient access.
Decreased Insider Threats
The implementation of just-in-time privilege escalation serves to mitigate internal threats by ensuring that personnel are granted access to sensitive information or specific operational capabilities only when essential. This precautionary measure helps prevent unauthorized or unintentional data access.
Human-Error Prevention
Proactively address incorrect read/write permissions to prevent disruptions and data corruption in your production environment. Regular audits help identify and rectify misconfigurations, ensuring the security and stability of critical data.
Request & Approve via ChatOps
Leverage the power of ChatOps workflows, seamlessly integrating platforms such as Slack and Teams, to both grant and request access in a collaborative and streamlined manner. This innovative approach enhances the accessibility and efficiency of access management within your organizational framework. By incorporating ChatOps, you create an environment where access permissions can be granted or requested through intuitive and user-friendly interfaces, such as chat interfaces in Slack or Teams.
Single Source of Truth
Centralize and streamline the management of privileges across your entire technology stack by consolidating them within a unified platform. This approach not only enhances efficiency but also facilitates a more comprehensive and cohesive oversight of the various permissions and access levels throughout your system, contributing to a more robust and integrated security framework.
Comprehensive Audit Log
Enhance MongoDB access and permissions transparency, facilitating comprehensive auditing for incident investigation and the implementation of scheduled reporting mechanisms to meet compliance requirements effectively.
Integrate with Apono
in 3 easy steps
Three easy steps are what it takes to create Just-In-Time and Just Enough
permissions for everyone with access to your cloud assets and resources
Automatically discover all resources managed by MongoDB.
Define dynamic permission workflows and approval processes.
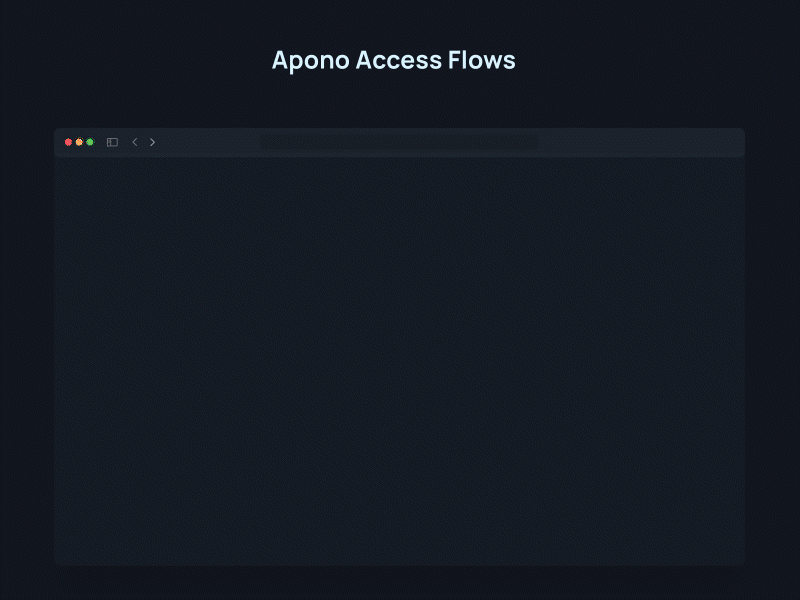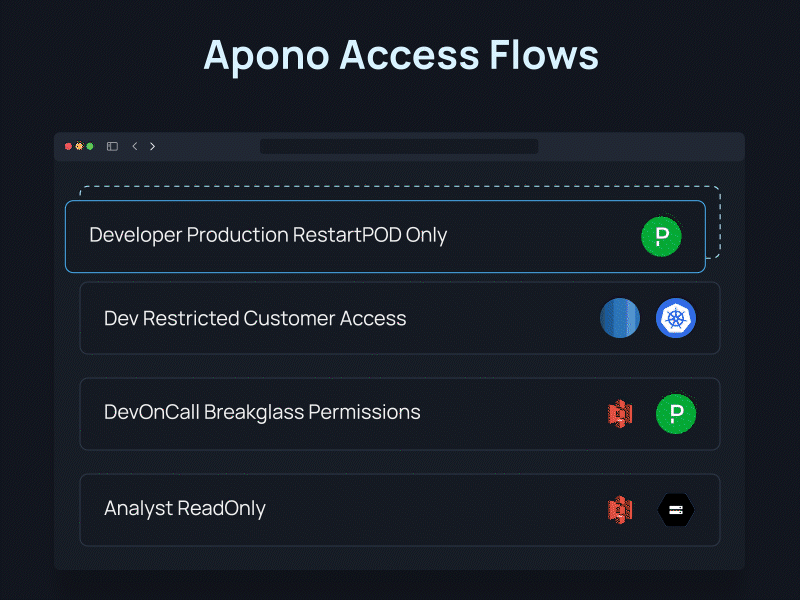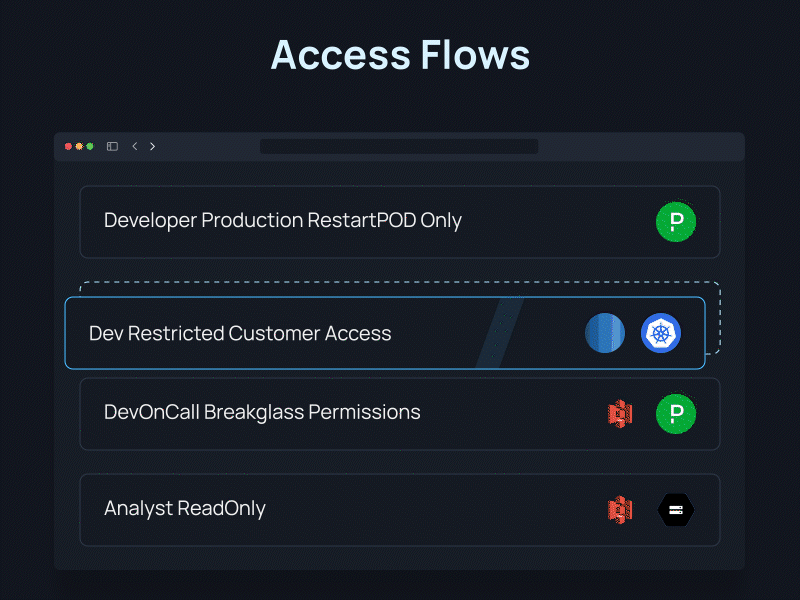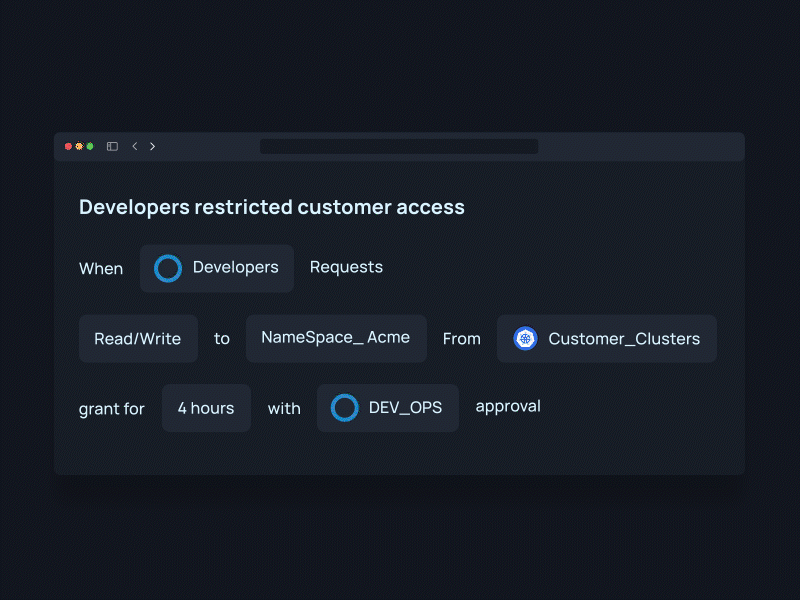
And that’s it! Now your team can directly request access to granular resources in a single click, automatically provisioned when you need it or shipped for approval – no more waiting for permissions or leaving them behind.
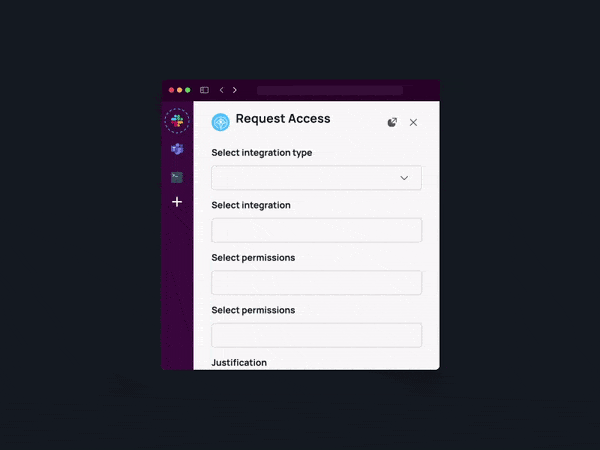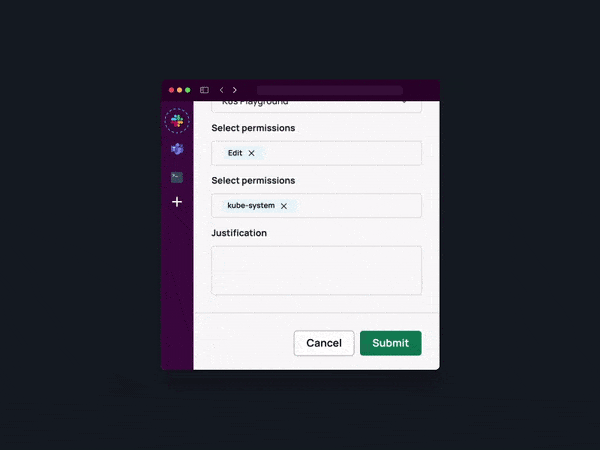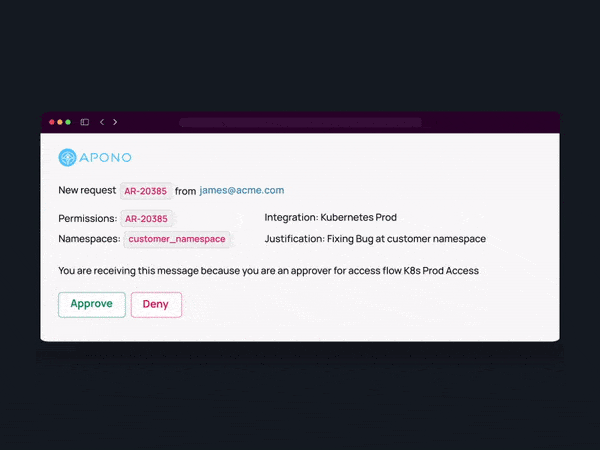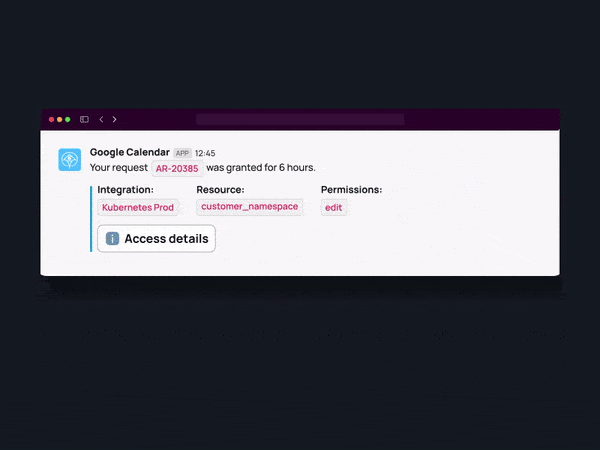
Review Access
View a detailed access audit of who was granted access to which instances with what permission level and why.
15-Minute Deployment
No Secrets Stored
Full Access Visibility