01
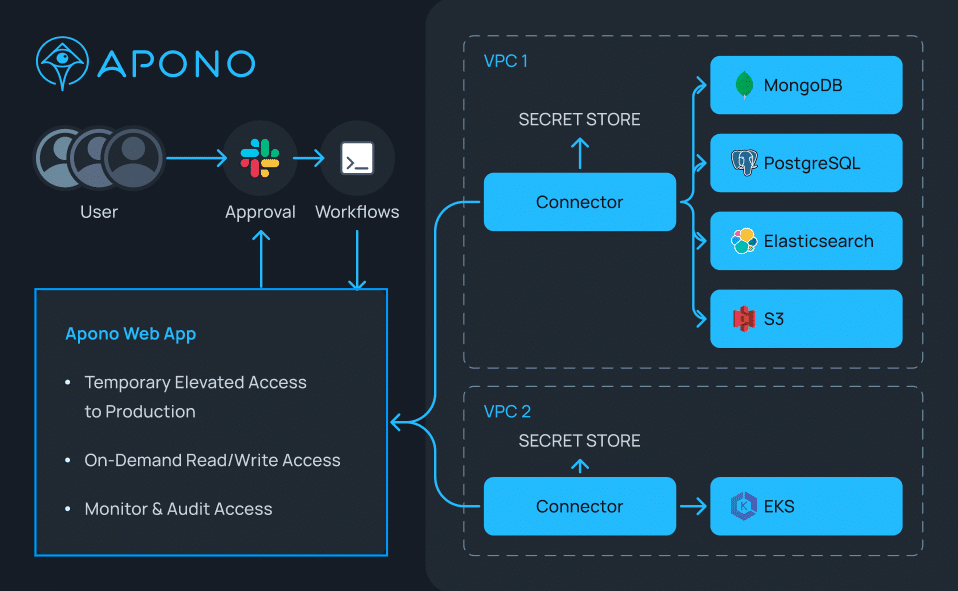
Just-in-Time Access
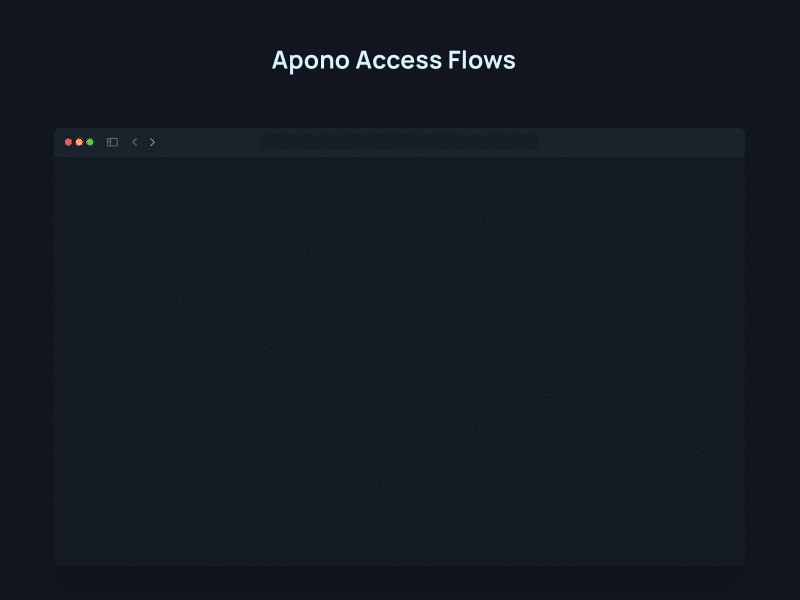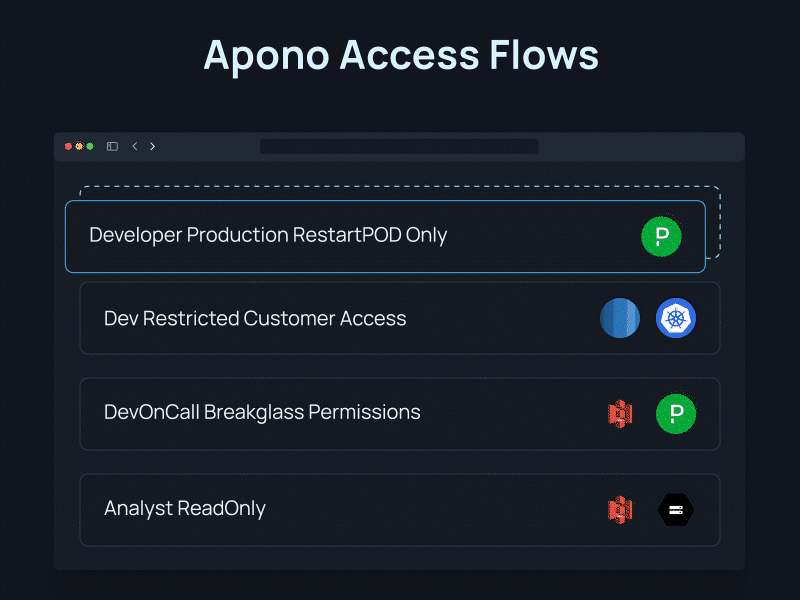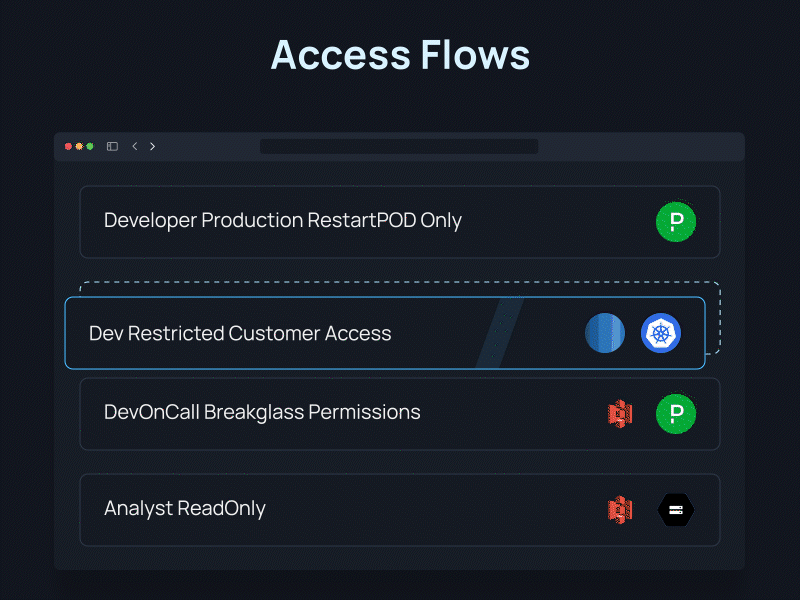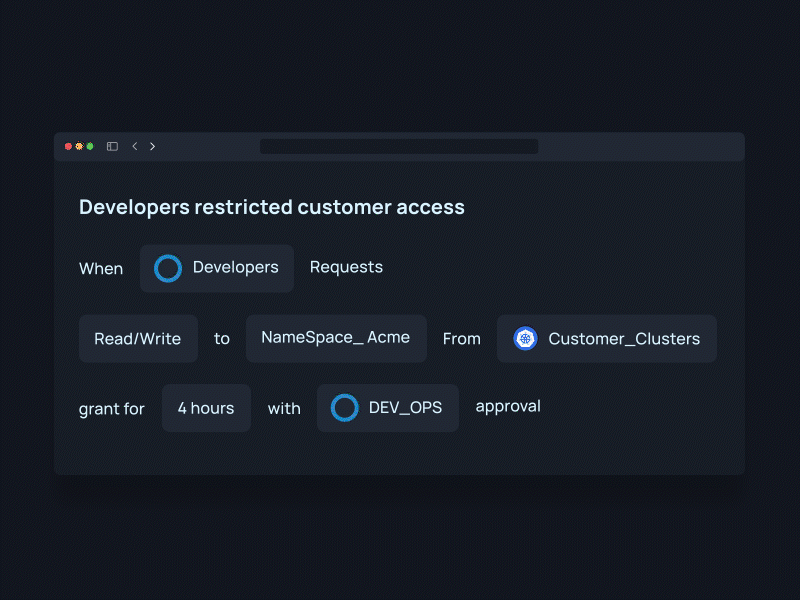
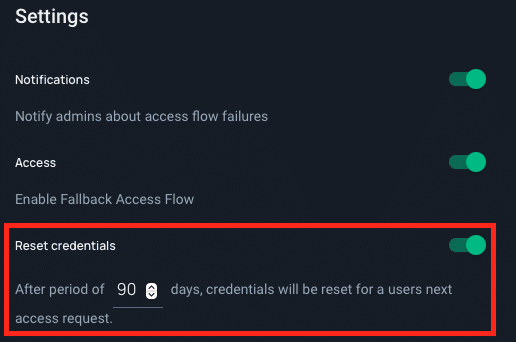
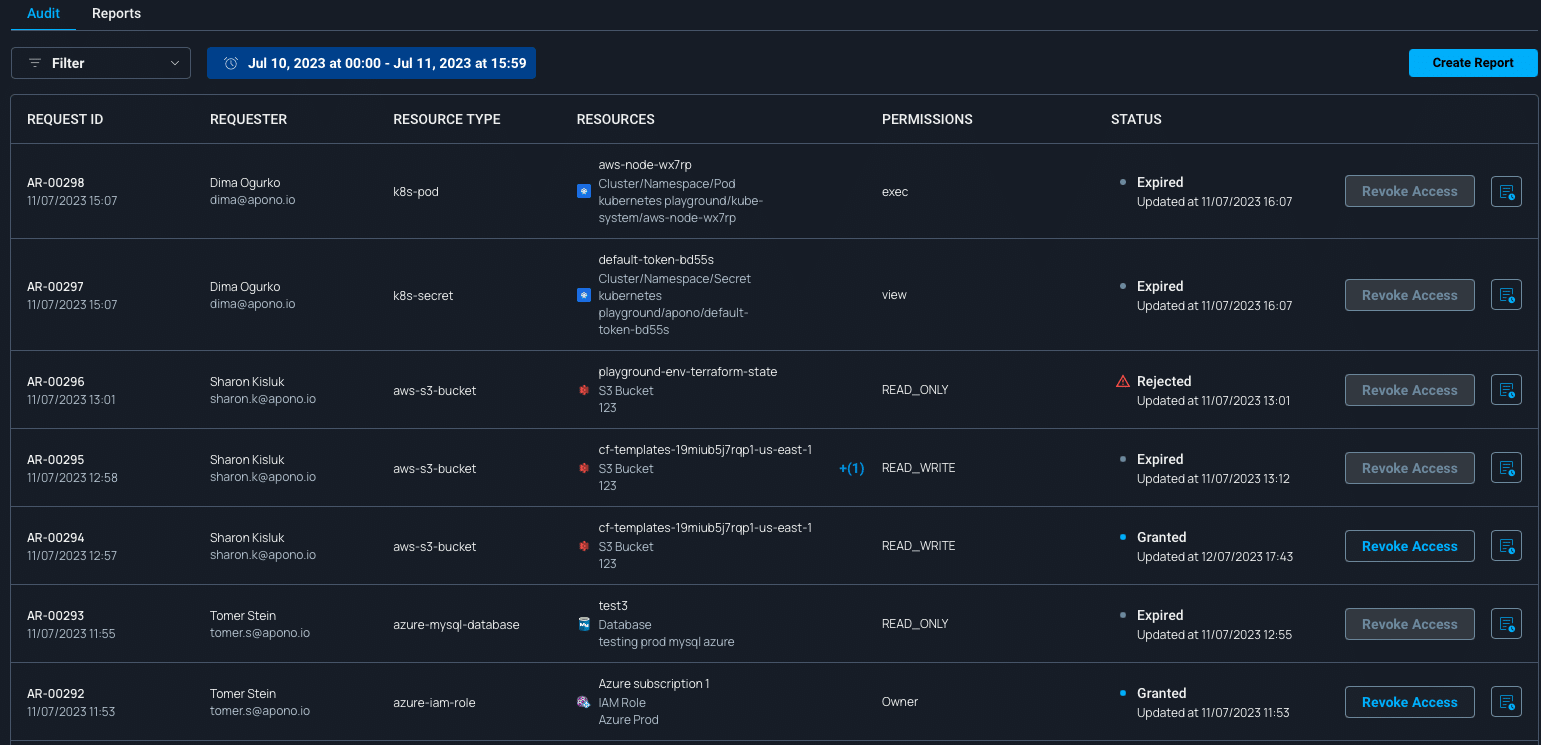
- Limit access to the minimum required permissions and implementing strict controls on when those permissions are granted, JIT access helps enhance overall security. This proactive approach reduces the risk of unauthorized access and potential security breaches.
- Integrate JIT access with your incident response plan. In the event of a security incident, having the ability to quickly adjust access permissions can be crucial for containing and mitigating the impact.
- Utilize JIT access with your identity management systems. This integration streamlines the process of aligning access permissions with changes in user roles, making it more efficient and less prone to errors.






 Dev_On_Duty
Dev_On_Duty  MongoDB
MongoDB