Top 10 Automated Access Control Systems
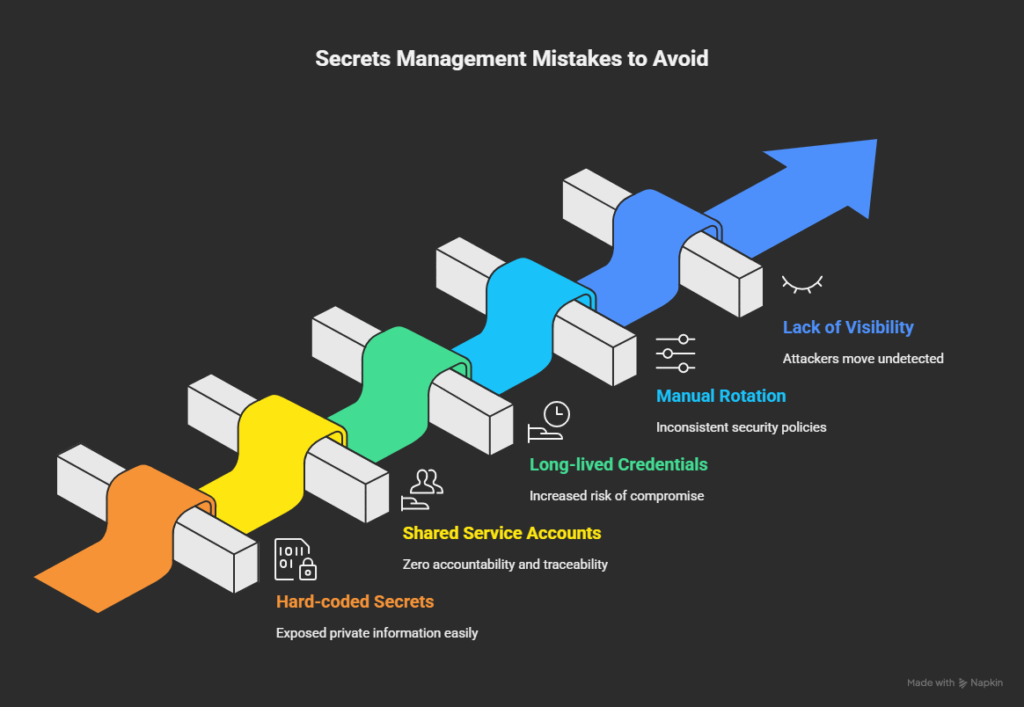
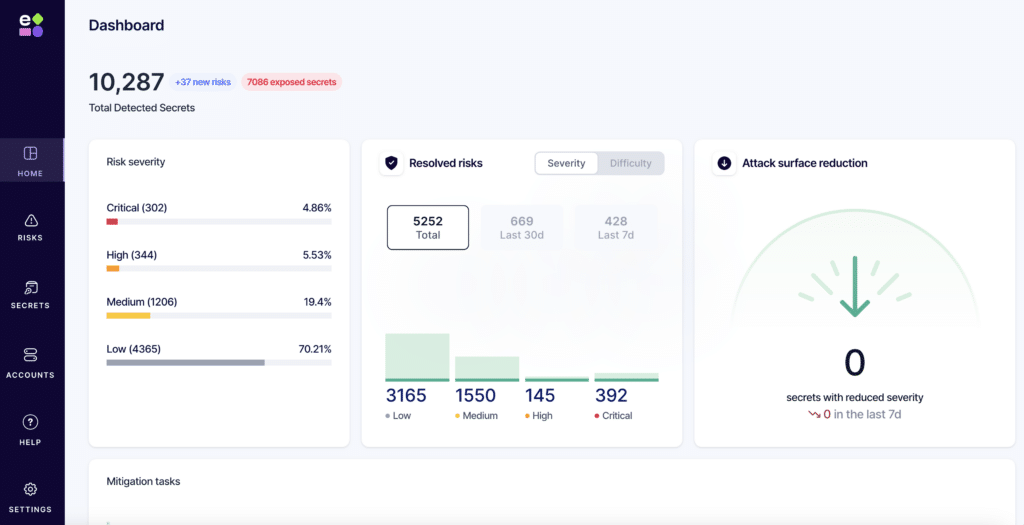
Manual access requests and long-lived credentials pose a significant scaling challenge for engineering teams, even as they automate pipelines, testing, delivery, and monitoring. As the volume of machine identities grows, the sheer volume of permissions makes manual review and revocation unmanageable, increasing risks of stale tokens and silent privilege exposure.
Nearly 47% of cloud intrusions stem from weak or mismanaged credentials, according to a Google Cloud report. Identity is still a major attack path rather than a solved discipline. Manual access management is unworkable at scale, but automated access control systems support fast workflows and safer access.
The automated access control platforms below help teams grant access automatically and maintain least privilege at scale. They support multi-cloud, SaaS, and modern CI/CD workflows, reflecting the future of identity security.
What are automated access control systems?
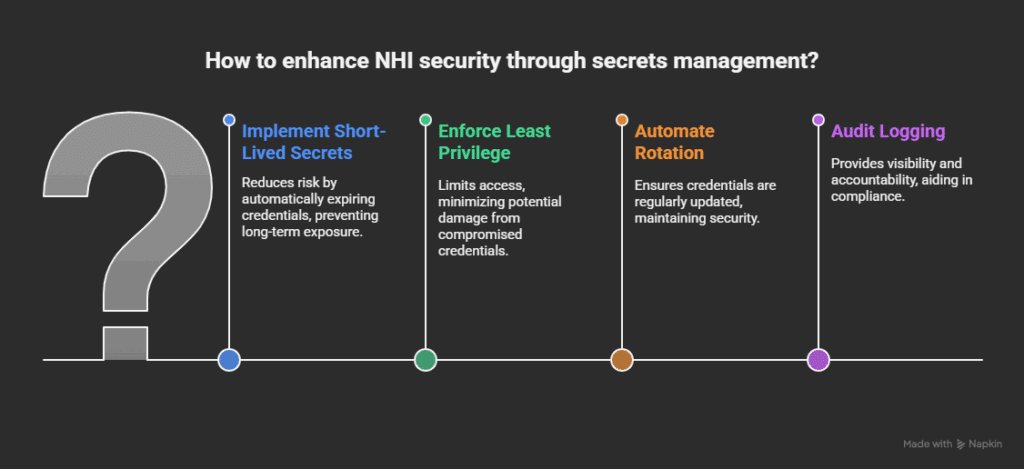
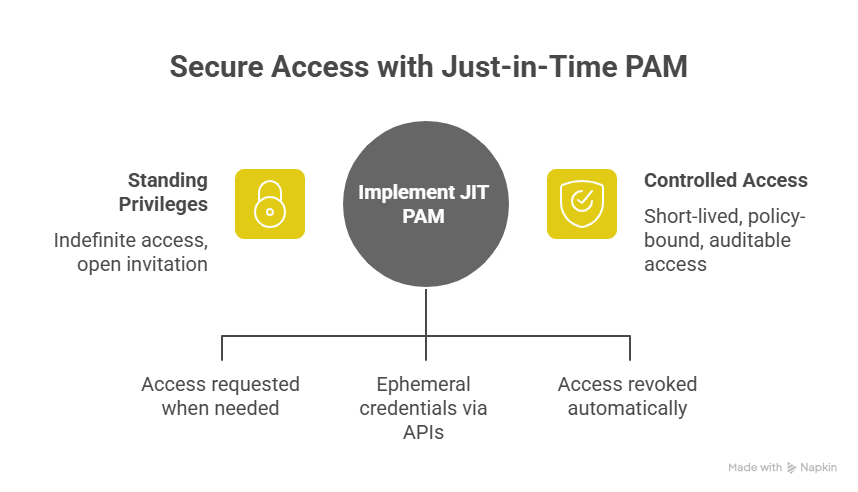
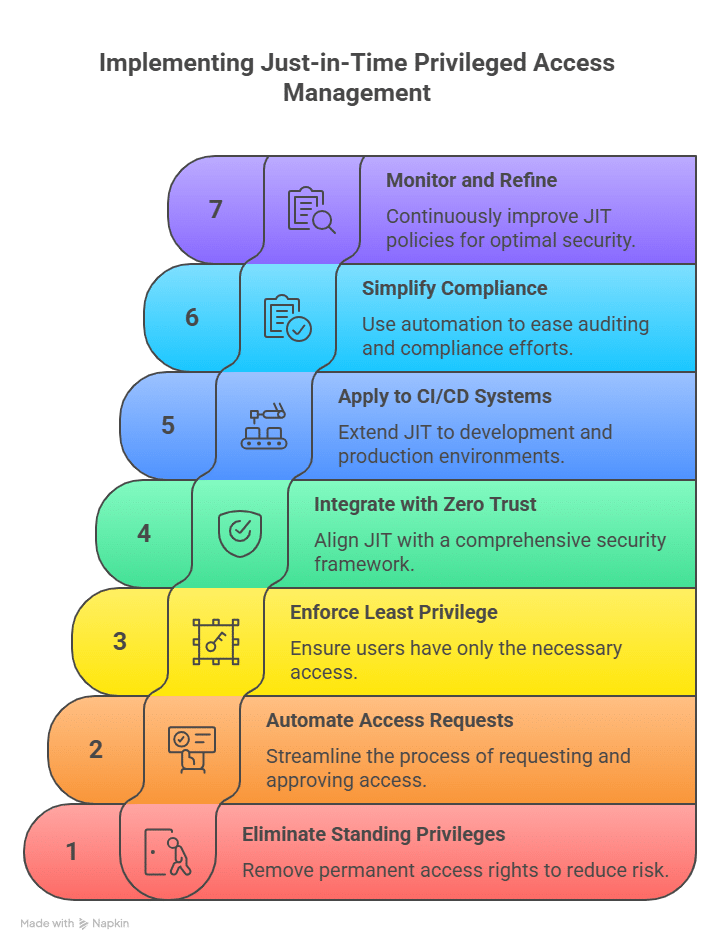
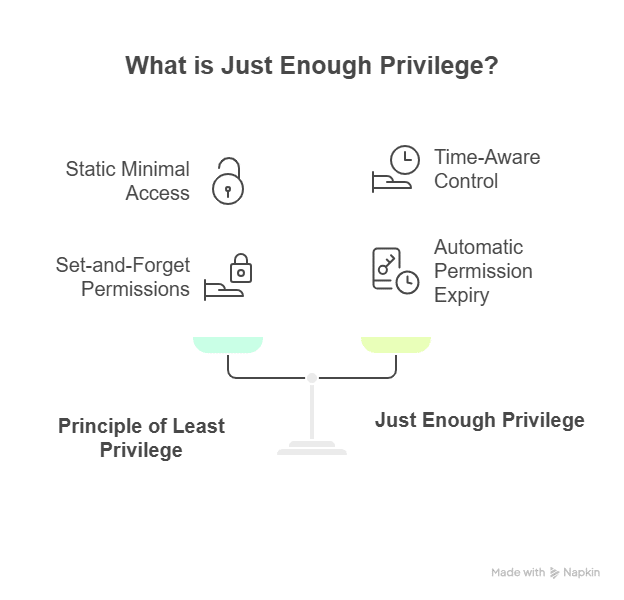
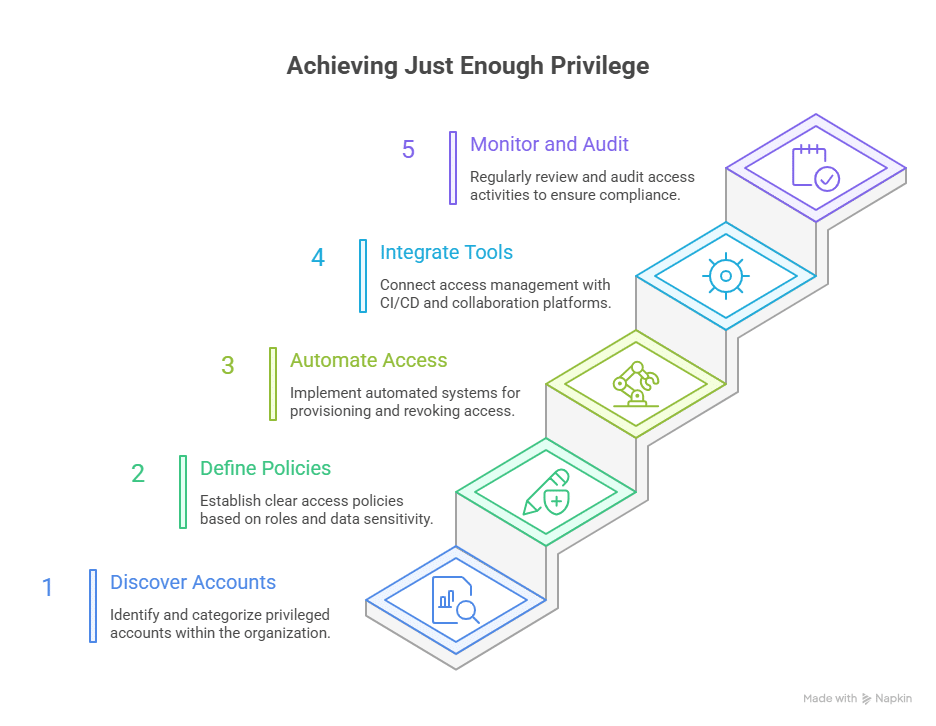
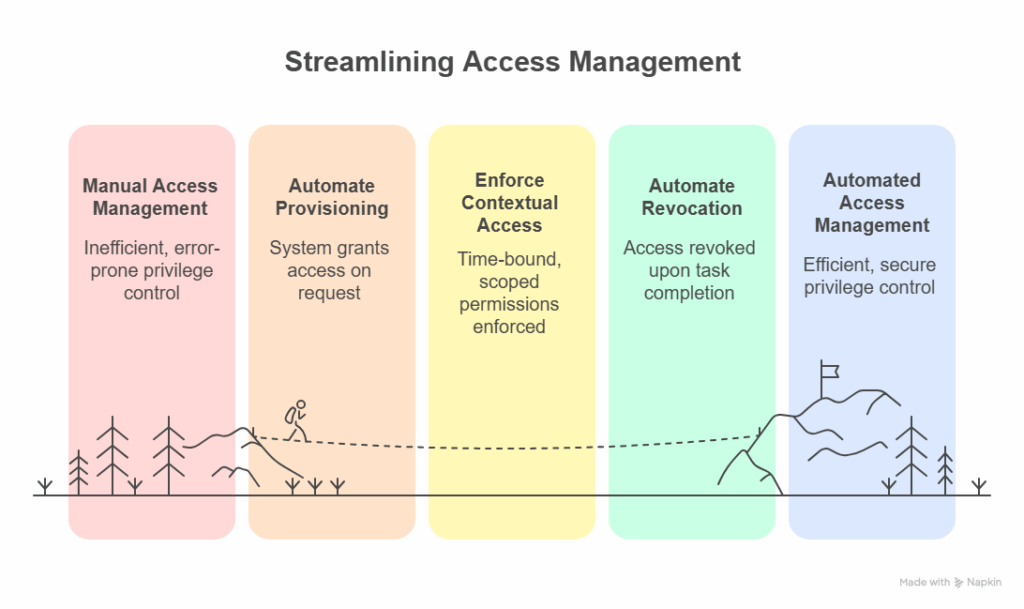
Automated access control systems use policy context and workflow automation to grant and revoke permissions without tickets, manual reviews, or long-lived credentials. Access opens only when it’s needed, remains active for the duration of a specific task, and then closes automatically, eliminating the risk of forgotten or persistent privileges.
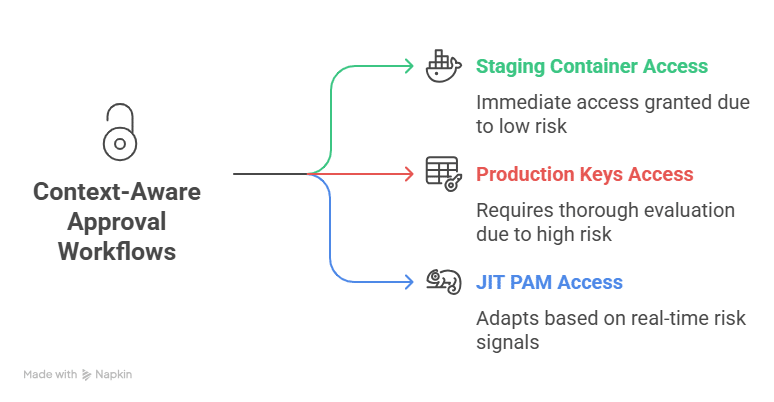
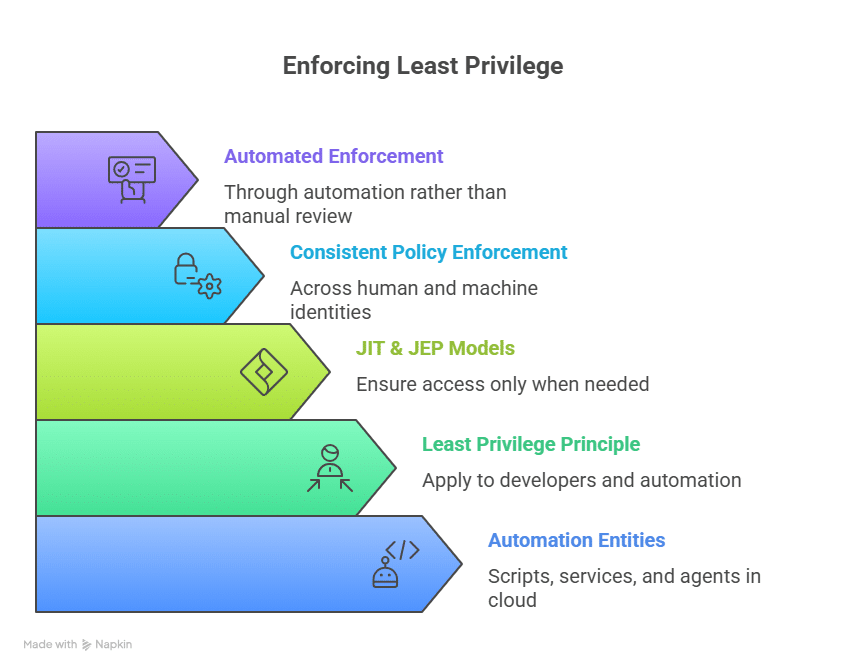
Automated access control systems reduce reliance on static, role-based access with short-lived, purpose-based permissions that align with least privilege and Zero Trust principles. Every access decision is logged and evaluated against contextual signals such as user role, device posture, location, risk score, and, in advanced systems, workload behavior.
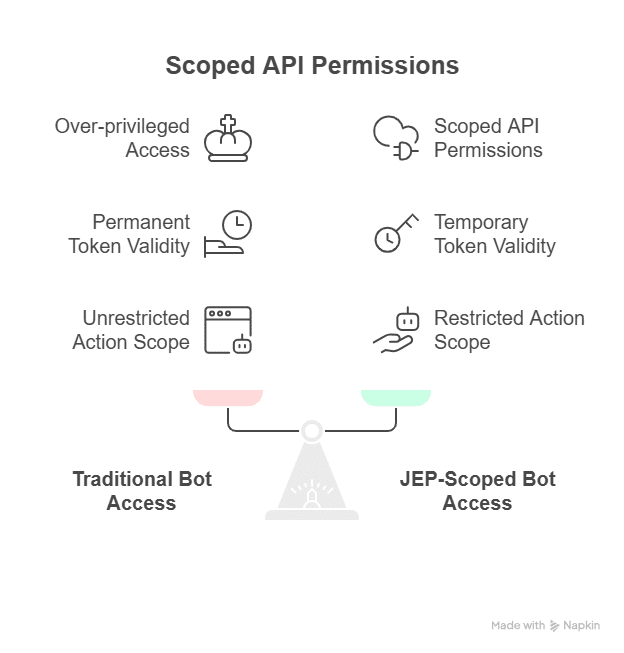
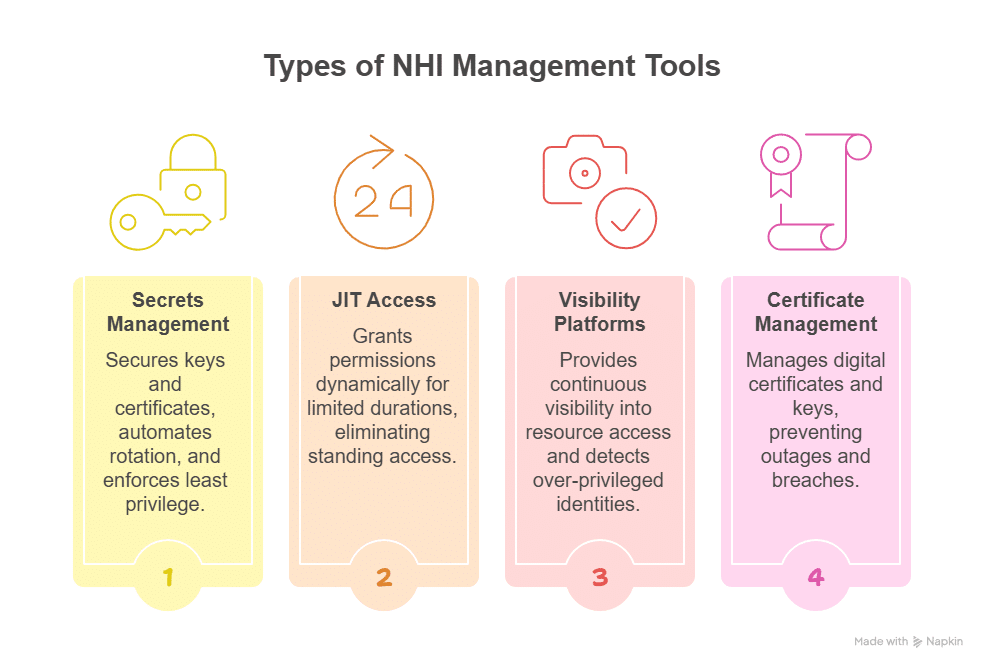
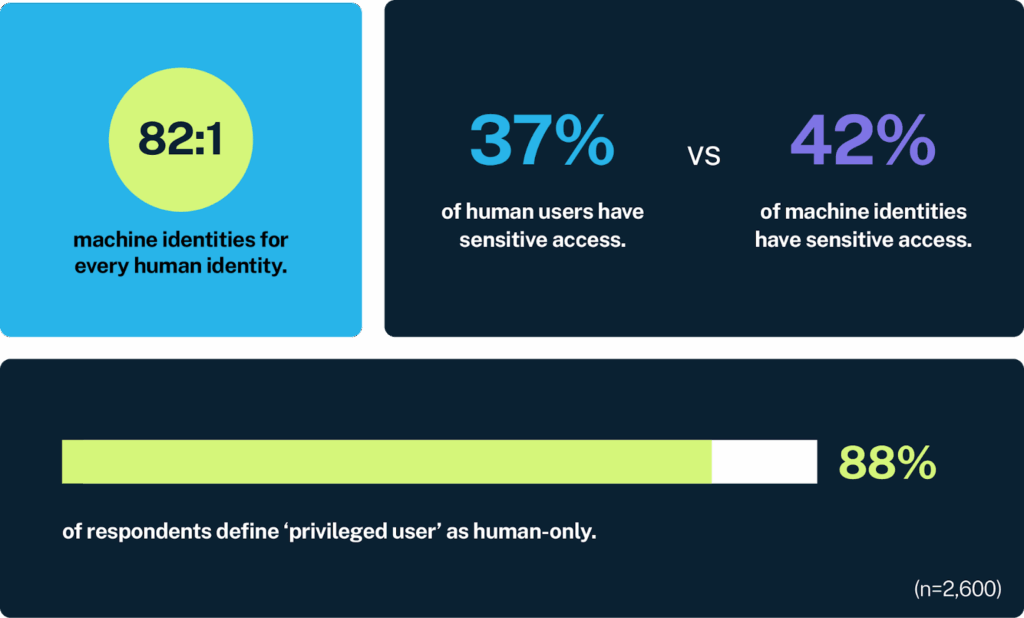
Non-human identities (NHIs), aka the service accounts, API keys, bots, CI/CD jobs, and cloud workloads running behind the scenes, now outnumber human users by an estimated 80:1. They move faster than any engineer and often carry the highest levels of privilege. The problem is that many NHIs still rely on long-lived IAM keys or broad, static roles. When that happens, they quietly turn into one of the largest and least-watched attack surfaces in the entire cloud environment.
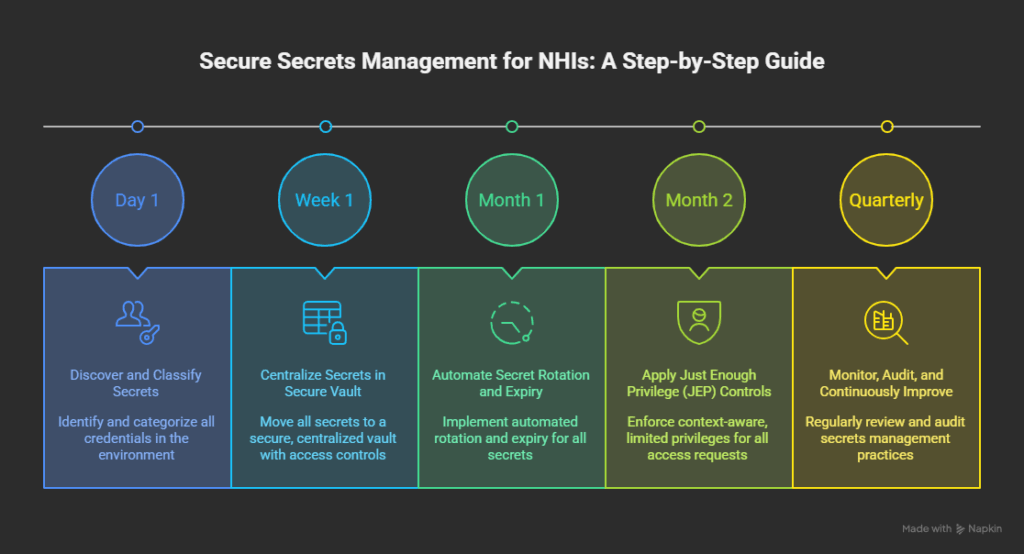
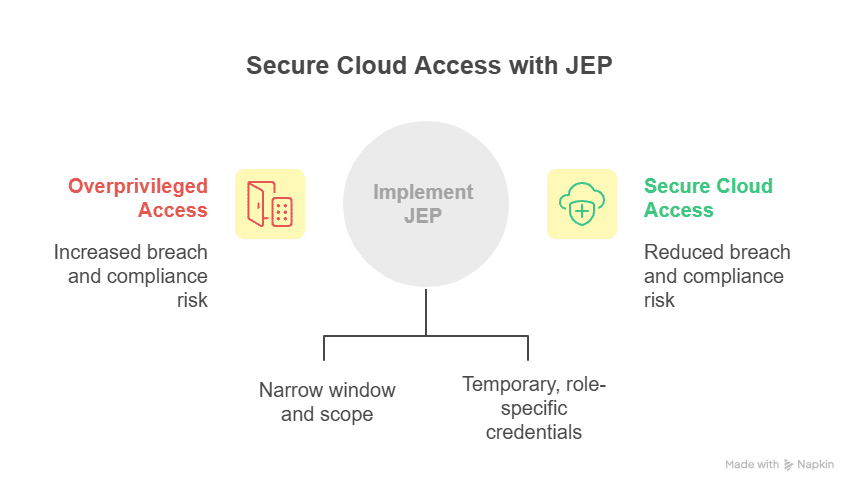
With automated access control systems, you can manage NHIs issuing short-lived, scoped permissions for each pipeline run or automation task, and revoke them cleanly as soon as work completes. This heightened risk is why teams increasingly rely on NHI management tools to right-size permissions and eliminate long-lived credentials.
Teams simply cannot track that level of entitlement sprawl or enforce credential rotation manually. Automated access control systems close that gap and consistently enforce least privilege. Modern platforms also integrate directly into CI/CD pipelines, issuing ephemeral credentials to remove long-lived secrets and reduce overall threat exposure.
Benefits of Automated Access Control Systems
- Replaces long-lived and risky access with short-duration, Just-in-Time permissions, strengthening your overall privileged access management strategy.
- Improves delivery speed by letting users request and receive access through familiar channels such as Slack, Teams, or CLI, without waiting in a queue.
- Produces automatic and timestamped audit records suitable for SOC 2, HIPAA, GDPR, and CCPA evidence reviews, giving security teams built-in compliance support.
- Reduces approval wait time and lowers the risk of misconfigured privileges by automating routing, access activation, expiration, and full teardown.
- Maintains consistent least-privilege enforcement across multi-cloud and hybrid environments through API-driven integrations.
- Controls non-human identities (NHIs) by issuing short-lived, scoped permissions, reducing one of the largest hidden attack surfaces in cloud environments.
Key Features to Look For in an Automated Access Control System
- Policy-driven access rules that adjust permissions based on identity, role, task, and context instead of fixed, long-term entitlements.
- Granular visibility and control across human and machine identities, cloud platforms, and sensitive services, with clear mapping of what each identity can reach.
- Native integration with cloud providers, identity platforms, collaboration tools, and CI/CD pipelines to align permissions with real activity and deployment flows.
- Self-service request and approval flows that let users obtain access quickly through approved channels without bypassing governance.
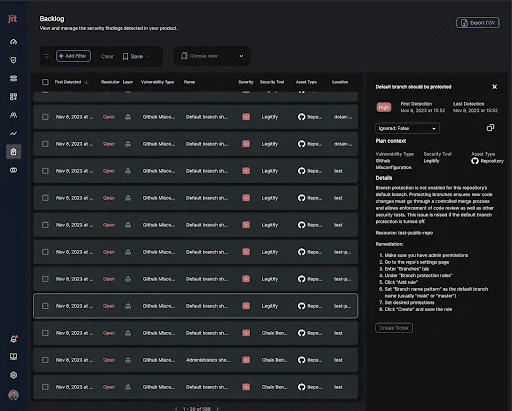
- Full audit and reporting coverage that records every access event, approval, and expiration with searchable logs for security and compliance teams.
- Break-glass and on-call escalation flows providing temporary emergency access with full audit trails and automatic expiration.
Top 10 Automated Access Control Systems
CATEGORY 1: Cloud-Native Access Automation
These solutions are purpose-built for fast-moving DevOps and SaaS teams that need automated Just-in-Time access and least privilege enforcement across multi-cloud environments.
1. Teleport
Teleport issues short-lived, identity-backed certificates for servers, Kubernetes clusters, databases, and internal applications. It removes static keys, records administrator sessions, and surfaces real-time activity to give teams a clear audit trail and tighter oversight of production access.
Best For: Teams that want certificate-based, Zero Trust access (with no standing credentials) across multiple clouds.
Price: Offers usage-based pricing for enterprises, and a free Community Edition is available.
Review: “I like that Teleport provides secure, certificate-based access to servers, databases, and Kubernetes clusters without needing a VPN.”
2. Apono
Apono automates Just-in-Time access across cloud infrastructure, SaaS tools, and data systems with policy-driven controls for both human and machine identities. Access is time-limited by default and revoked automatically. Engineers can request access from Slack, Teams, or CLI while Apono handles validation and approvals in the background.
Apono also eliminates privilege sprawl by continuously discovering over-privileged identities and automating remediation. Real-world teams are already doing this at scale. Organizations like Caris Life Sciences use Apono to replace broad, persistent database access with time-bound, auditable permissions aligned with Just Enough Privileges.
After adopting Apono, Caris reduced standing access across sensitive systems and accelerated on-call response by giving engineers fast, temporary access exactly when needed, without compromising compliance or security.
Best For: Organizations looking to automate the entire Just-in-Time access workflow, from request through revocation, with no manual steps.
Price: A 30-day free trial is available for JIT database access.
Review: “Most integration configurations are straightforward and backed up by informative yet simple documentation. In more complicated cases, Apono’s team were happy to help and solved issues fast and with high professionalism.”
3. Zitadel
Zitadel offers a modern approach to authentication, supporting OIDC, passwordless login, and both RBAC and ABAC. Developers get clean APIs and SDKs they can plug straight into their applications, which means they don’t have to own identity storage or user lifecycle management themselves.
Best For: Teams that want solid authentication and fine-grained authorization built into their services.
Price: A free tier is available, and paid plans are billed based on monthly active users.
Review: “I was relieved to discover ZITADEL, allowing us to leverage their expertise so we can focus on the rest of our platform development.”
CATEGORY 2: Developer-First Access & Authorization Tools
These tools support teams that want to control permissions at the application and service layers using code-driven policy logic, rather than relying on broad platform-level entitlements.
4. Cerbos
Cerbos is a lightweight policy engine that lets teams pull authorization rules out of their application code. At runtime, Cerbos evaluates those policies through an API, giving every service consistent access decisions, even for automated workflows collecting data at scale or interacting with internal systems.
Best For: Teams that want to externalize authorization logic without adopting a full IAM suite.
Price: Free open-source core plus paid Hub tiers (starting at $25/month) for managed policy tooling and scalable production deployment.
Review: “The best thing about Cerbos is how easily I can tweak access control logic without having to even touch the codebase.”
5. ConductorOne
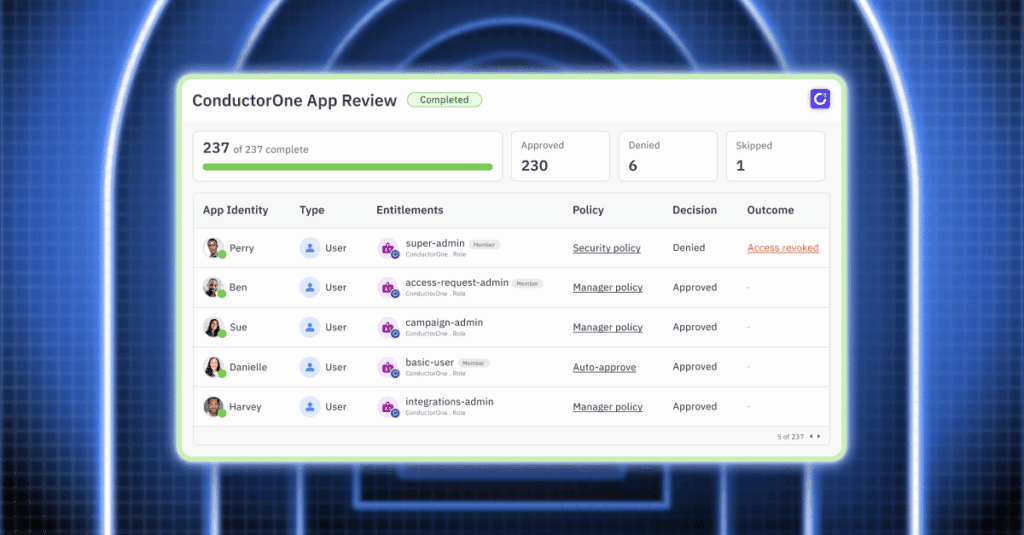
ConductorOne orchestrates SCIM-based provisioning, deprovisioning, and access reviews alongside existing IdPs. Its strong point is lifecycle management, with HR-triggered onboarding and offboarding plus one-click access to recertifications.
Best For: Organizations that want identity governance that keeps pace with cloud tooling, frequent onboarding changes, and rapid permission updates.
Price: Custom pricing.
Review: “The real strength behind ConductorOne is the ability to leverage its workflows against, at first glance, many disparate SaaS systems, which may not have cohesive workflows out of the box.”
CATEGORY 3: Enterprise IAM Platforms
This category serves organizations that manage large numbers of users and systems, requiring structured identity provisioning, governance workflows, and compliance-ready controls.
6. One Identity Manager
One Identity Manager links HR and directory data with enterprise apps to automate provisioning, enforce modeled roles, and run scheduled attestation cycles. It is well-suited for complex, regulated organizations that need full governance coverage across many identity sources.
Best For: Organizations operating under strict regulatory or audit requirements that need structured provisioning, role governance, and attestation cycles.
Price: Enterprise pricing is available upon request.
Review: “We saw a significant boost in IT staff productivity after adopting the One Identity platform.”
7. Ping Identity
Ping Identity delivers a broad range of enterprise IAM services, including SSO and policy-based access control tailored to hybrid and multi-cloud deployments. It integrates seamlessly with legacy infrastructure while offering modern authentication flows, such as passwordless login and adaptive risk evaluation.
Best For: Organizations modernizing hybrid IAM without overhauling legacy systems.
Price: Starts at $35,000 annually for Essential and $50,000 for Plus, with pricing adjusted by scope and features.
Review: “This use of open standards and overall stability makes it an excellent platform to base user authentication upon.”
8. Okta Workforce Identity Cloud
Okta Workforce Identity Cloud combines MFA and automated lifecycle workflows with a deep catalog of prebuilt connectors. This gives teams turnkey provisioning and offboarding coverage across thousands of SaaS and enterprise applications.
Best For: Companies standardizing workforce identity across SaaS and hybrid cloud.
Price: Tiered pricing, with core authentication in lower plans and lifecycle, device, and API security features in advanced plans.
Review: “It provides a secure, centralized way to manage user access across multiple applications, which saves time and reduces risk.“
CATEGORY 4: Data-Centric & Authorization Intelligence Platforms
These platforms focus on deep data-layer visibility and contextual authorization, making them ideal for organizations tackling entitlement sprawl and enforcing least-privilege access at scale.
9. Twilio Verify / Identity
While not a full access control platform, Twilio Identity supports access workflows by validating user identity and risk signals before permissions are granted. It delivers API-based verification, including phone, document, and risk-based checks, so applications can validate users in real time.
Best For: Apps needing flexible, API-first user verification workflows.
Price: Pricing is usage-based per verification, with volume pricing available for higher throughput workloads.
Review: “I was looking for a communication API for my new product when I came across Twilio. It’s super easy and fast to implement, paired with a good customer support team.”
10. Veza
Veza builds an Access Graph across cloud, SaaS, and data systems to reveal effective permissions and hidden entitlements. It helps teams spot unused or over-privileged access and recommends least-privilege adjustments grounded in real data-layer visibility.
Best For: Organizations tackling complex entitlement sprawl across data and SaaS ecosystems.
Price: Custom pricing.
Review: “Veza gives us both broader and deeper visibility into who has access to our data, and how they have access to that data, so we can trust and verify that personnel only have the access they need.”
Why Temporary, Contextual Access is the New Standard
Identity security is moving fast, and the direction is clear: access needs to be temporary, contextual, and fully auditable. The shift toward automated, policy-driven controls IS how engineering teams keep pace with multi-cloud complexity and the explosion of human and non-human identities.
Apono’s approach aligns directly with the trends outlined above by automating Just-in-Time access and enforcing least privilege for both human and machine identities. Auto-expiring permissions, break-glass and on-call workflows, and full access discovery make Zero Trust practical, and it’s all deployable in under 15 minutes.
If you’re ready to see how automated access actually works in a real environment, get a personalized walkthrough today.