
Just-in-Time Access To Identity-Aware Proxy (IAP)
With Apono you’ll be able to create dynamic Access Flows that grant permissions with high granularity and full audit.

Identity-Aware Proxy (IAP) is a Google Cloud Platform (GCP) service that provides secure access to web applications hosted on Google Cloud or on-premises infrastructure. It allows administrators to control access to web applications based on the user’s identity and context, rather than relying solely on traditional network-based security measures like VPNs or IP whitelisting.
Just-in-Time (JIT) access involves assigning permissions to users or systems in real-time as needed, rather than maintaining continuous access. This strategy is frequently employed in cybersecurity to reduce the risk of security breaches by restricting unnecessary access. It aligns with the principle of least privilege (POLP), emphasizing that users should only have the minimum access levels required to fulfill their tasks.
Use Cases
Developer JIT Access
- Limit access to the minimum required permissions and implement strict controls on when those permissions are granted. JIT access helps enhance overall security. This proactive approach reduces the risk of unauthorized access and potential security breaches.
- Integrate JIT access with your incident response plan. In the event of a security incident, having the ability to quickly adjust access permissions can be crucial for containing and mitigating the impact.
- Utilize JIT access with your identity management systems. This integration streamlines the process of aligning access permissions with changes in user roles, making it more efficient and less prone to errors.
Secure Break-glass Access
- Manage break-glass access, balancing the need for emergency access with the imperative of maintaining robust security measures.
- Implement comprehensive logging and monitoring systems to track and record break-glass access events.
- Dynamically grant only the permissions needed for the task at hand to prevent downtime and costly mistakes in production.
Automated Access
- Escape the frustration of ticket fatigue and the time-consuming nature of manual provisioning through the implementation of automated access flows.
- Embrace innovation to revolutionize your workflow, saving time and resources, enhancing efficiency, and ensuring a secure access management system.
- Automate your access control and witness a transformative shift in permission allocation within your organization.

Start automating access and permissions management in minutes.
Automate Kubernetes Permissions
Mitigate the challenges associated with ticket fatigue and enhance operational efficiency by seamlessly integrating automated access flows. Say goodbye to the manual provisioning grind as this innovative solution simplifies and accelerates the process, allowing for a more streamlined and user-friendly experience.
Customer Data Separation
Empower your organization by granting ownership to specific resources, while concurrently providing full audit capabilities that not only meet but surpass customer security requirements. Implementing this allows you to confidently navigate and fulfill stringent security mandates, fostering a culture of trust and diligence in resource management.
Time-Restricted Access
Rather than providing access for an indefinite duration, consider implementing a more strategic approach by opting for time-bound access provisioning. This nuanced strategy involves assigning access permissions for a specified and predetermined period, enhancing the control and security of your access management practices. By adopting time-bound access, your organization gains the flexibility to align permissions precisely with the temporal requirements of specific tasks or roles.
Self-Service Access Requests
Amplify employee productivity through the implementation of an efficient system that empowers individuals to seamlessly discover, request, and obtain access to essential resources in a matter of minutes. This transformative approach not only expedites operational efficiency but also cultivates an environment characterized by heightened agility and responsiveness.
How Apono works in 3 steps
Three easy steps are what it takes to create Just-In-Time and Just Enough
permissions for everyone with access to your cloud assets and resources.
Automatically locate all resources managed by IAP.
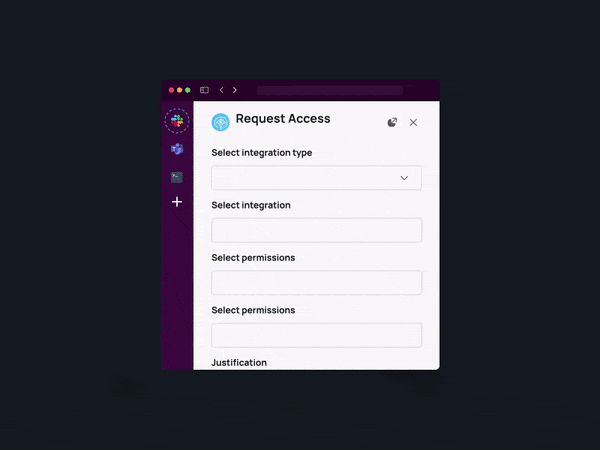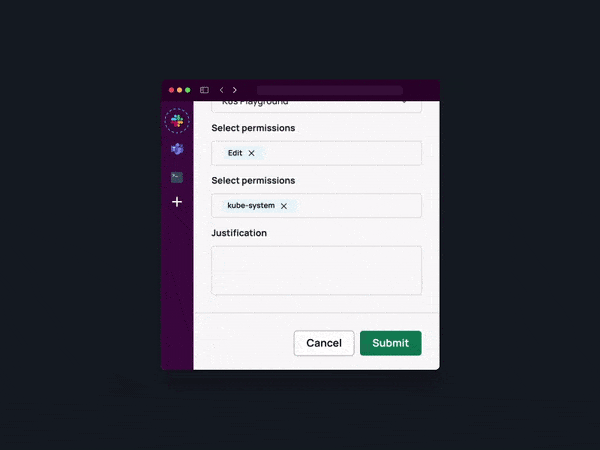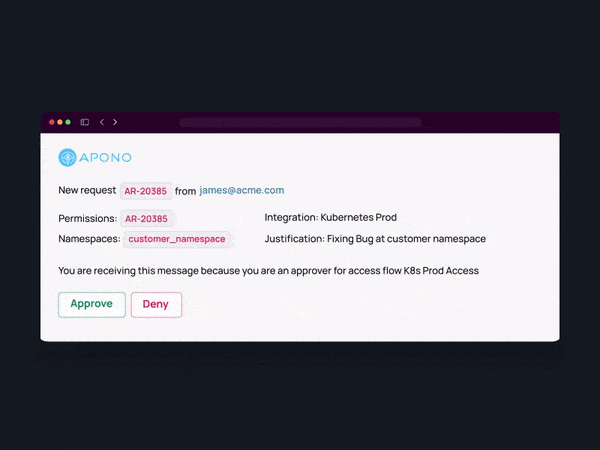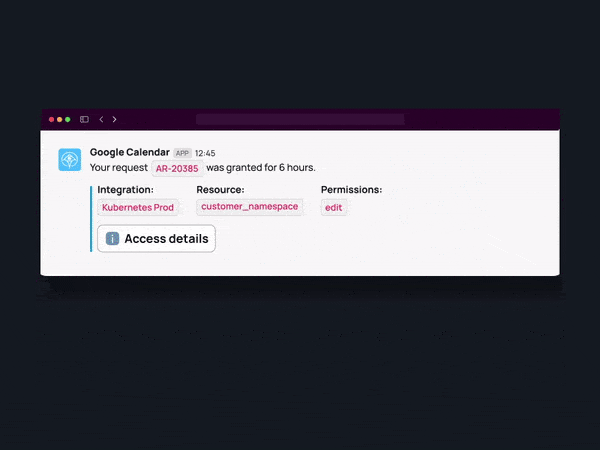
Define dynamic permission workflows and approval processes.

And that’s it! Now your team can directly request access to granular resources in a single click, automatically provisioned when you need it or shipped for approval – no more waiting for permissions or leaving them behind.
Review Access
View a detailed access audit of who was granted access to which instances with what permission level and why.
15-Minute Deployment
No Secrets Stored
Full Access Visibility