Table of Contents
At Apono, we constantly hear from customers how difficult it is to set up granular permissions with F5, so we decided to dive in and see what’s so frustrating. We found a total of 6 issues. Check them out below.
Quick Overview: What is F5?
F5 is a company specializing in application security, multi-cloud management, online fraud prevention, application delivery networking (ADN), application availability & performance, network security, and access and authorization.
Challenges of F5 Permission Management
- Not flexible
- Distributed workforces, rapid cloud adoption and a reliance on connected systems means that today sensitive data is copied, moved and shared to systems and collaboration tools that reside outside of the business.
- No internal auditing processes.
- Legacy data permission practices and technology make it impossible to audit data permissions based on a business’s sensitive information and where it lives. As a result, system administrators struggle to stay on top of data access.
- No way to generate temporary permissions on-demand.
- Permissions are static, so any change needs to be done manually, which takes time and manpower.
- Too many over-privileges
- For many companies, the quickest and simplest way to give out permissions is to just assign a person the highest and widest access policies.
- Requires manual oversight to maintain.
- Manual provisioning and de-provisioning of access is labor-intensive and prone to human error or oversight. It is not an efficient or sustainable way to manage user identities and access, especially for large enterprises.
- Customer data not secure.
- With the proliferation of over-privileged credentials, it’s easier than ever for attackers to gain access to secure information, which is why it’s important that permissions be temporary and limited in scope.
- Proxy-based.
- F5 has a roof that allows you to set a workflow such as “this IP can access this IP,” which is too broad for granular-level access policies.
Luckily, there are ways to overcome these obstacles. Read on below to find out how.
How Apono Makes F5 Permission Management Work
- Just-in-Time (JiT) Access. “Always-on” privileged accounts have long reigned as the default mode for administrative access. Today, these powerful, always-on accounts proliferate across enterprises. This means that the privileged access, rights, and permissions are always in an active mode and ready to be exercised—for legitimate activities as well as for illicit ones.
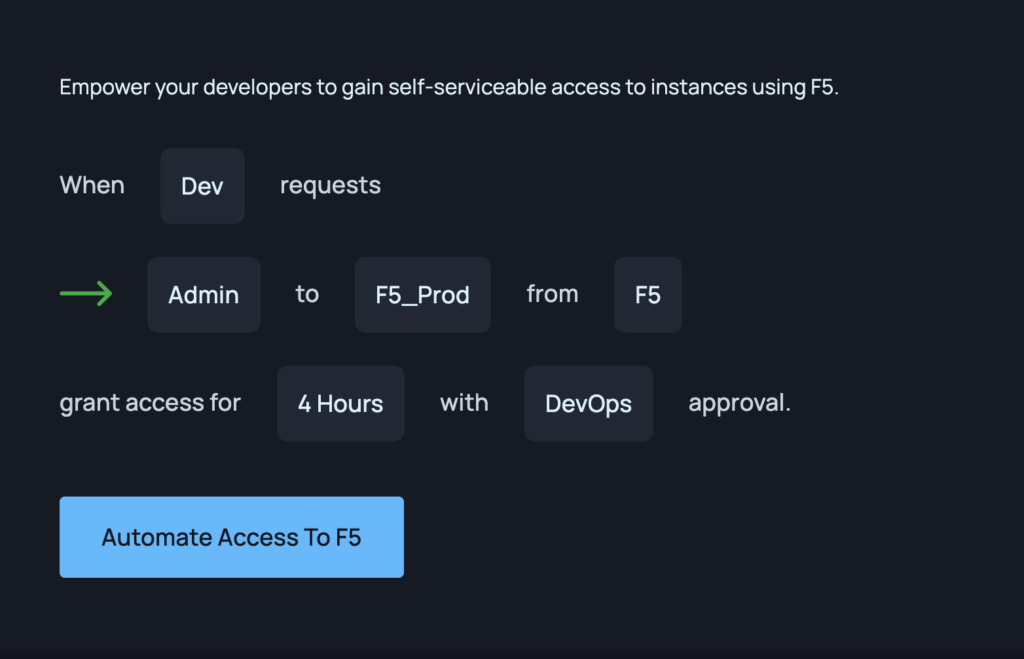
2. Automated Access Workflows. Setting up automatic workflows saves manual labor and time. They also allow for break-glass scenarios when needed, which decreases MTTR and downtime.
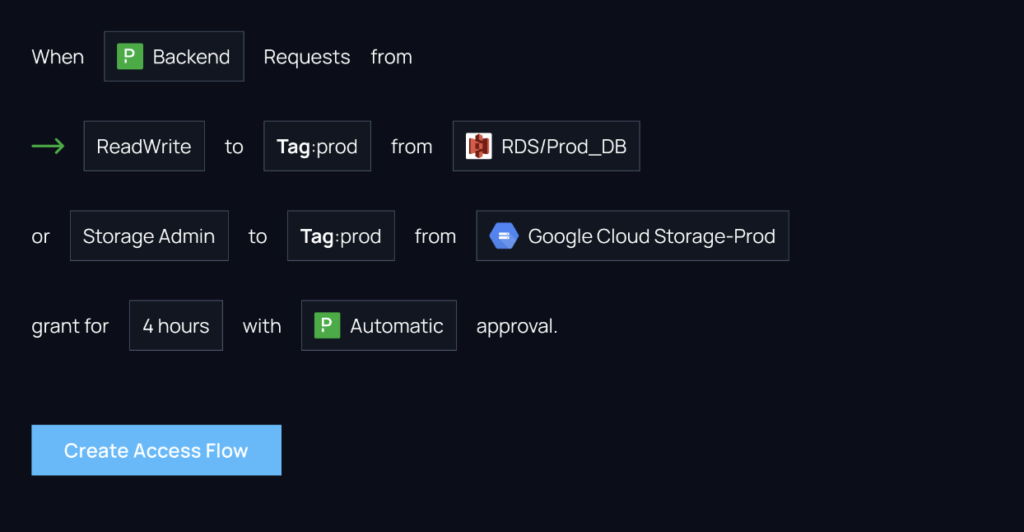
3. Self-Serve Permissions. Self-service access workflows allow you to create a process for your users to request access to datasets quickly and easily.
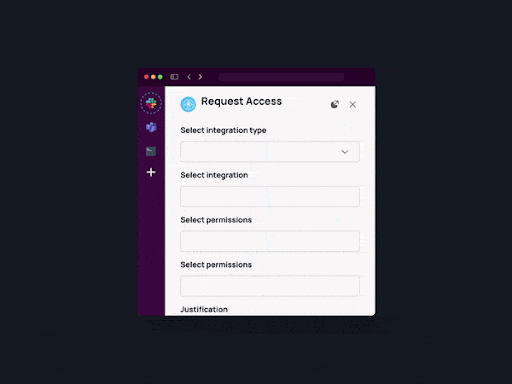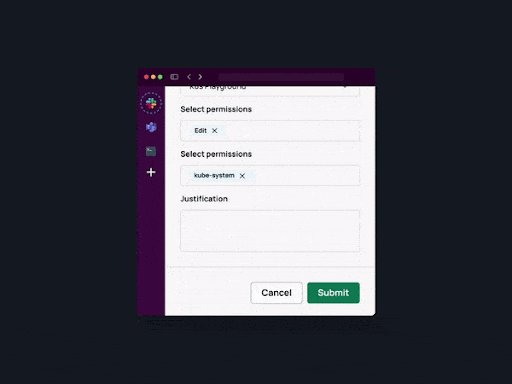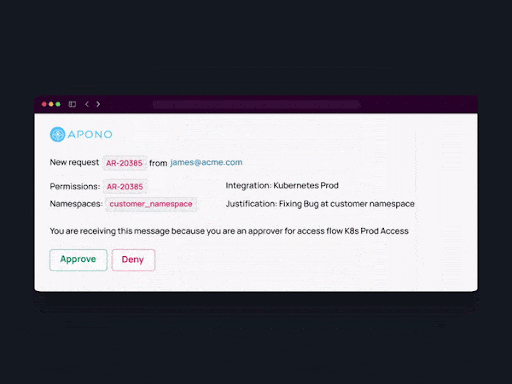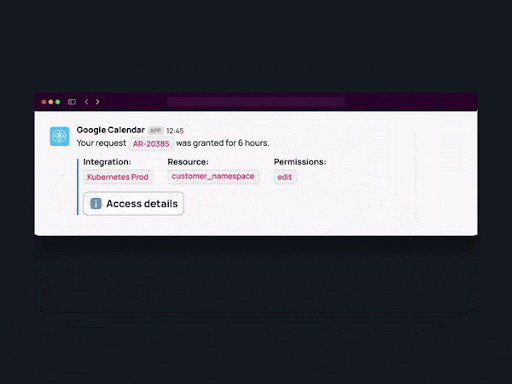
4. Resource-based access policies. Apono allows you to grant permissions to granular-level resources such as down to specific namespaces.
“Apono allows us to generate temporary permissions upon request on a very granular set of restrictions, delivering huge value to the business by reducing that Excel phase and optimizing the day-to-day work of multiple teams, including the R&D operations and security teams.”
As you can see, creating on-demand, granular-level permission access policies is impossible to do with just F5 alone. In order to benefit from JIT with F5, it’s imperative that you use a tool that can handle dynamic context. In other words, F5 permission management doesn’t have to suck anymore.


