403 Forbidden: What is it and How to Solve it

The Apono Team
July 17, 2025
Modern software development is all about speed. To outpace competitors, rapid feature development, production deployments, and testing are conducted concurrently. But all it takes is one unexpected 403 Forbidden error to bring everything to a halt.
For DevOps and platform teams, a 403 Forbidden error can stall automated deployments and break CI/CD pipelines. These issues often stem from identity misconfigurations, especially as environments grow more complex and non-human identities (like service accounts and automation scripts) proliferate.
In response, 78% of enterprises say they are prioritizing identity security to ensure every action, whether triggered by a developer or a bot, has the right access at the right time. A simple 403 Forbidden error might just be the tip of a much larger access control problem, so it’s essential to understand why this issue happens in the first place.
What is a 403 Forbidden Error?
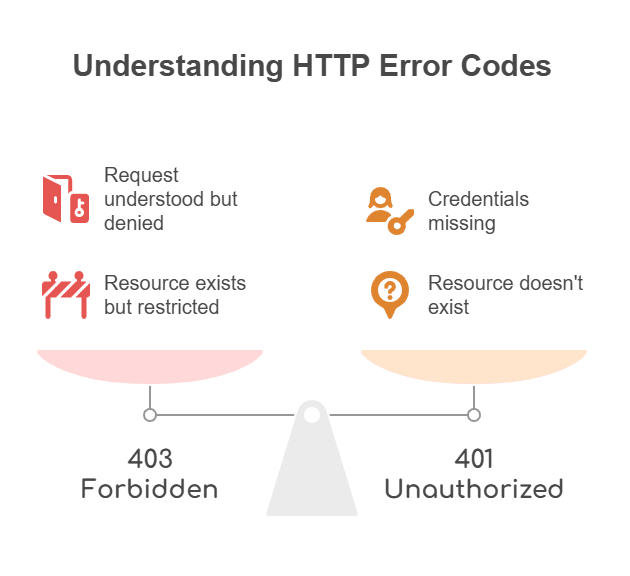
A 403 Forbidden error is an HTTP status code that means the server understood your request but won’t allow it. In simple terms, you’re not allowed to access the resource, even though the server knows what you’re asking for. It is different from other common errors:
- 401 Unauthorized means you haven’t logged in or your credentials are missing.
- 404 Not Found means the resource doesn’t exist at all.
Some services return a 403 when request quotas are exceeded, especially APIs that distinguish between rate-limiting (403) and authentication (401). Think of the comparison like this:
| Status Code | Explanation |
| 200 | OK: You’re in. |
| 401 | Unauthorized: You need a key. |
| 403 | Forbidden: You have a key, but the door is still locked. |
| 404 | Not Found: There’s no door at all. |
The proliferation of non-human identities (NHIs) lacking the exact permissions or scopes required to complete a task contributes to common 403 Forbidden errors.
For OAuth2-based APIs, a 403 may be triggered if a token is valid but lacks the required scope, such as read:user or write:repo. Always confirm scope claims and expiration (typically 15–60 minutes).
The Role of NHIs in 403 Forbidden Errors
While most developers associate 403 Forbidden errors with user permission issues, NHIs (e.g., machine identities, service accounts, and API keys) are often the silent culprits. Without active lifecycle management, these identities accumulate risks, such as stale tokens and outdated permissions. And, unlike users, they don’t raise support tickets. That’s why visibility and governance over NHIs are critical to diagnosing and preventing access failures.
What causes the 403 Forbidden error?
1. Incorrect File or Folder Permission
If the server settings don’t allow public access to a file or folder (like missing permission settings), it will block the request even if the file is there.
2. IP Address Blocking or Geo-Restrictions
Some servers are configured to deny requests from specific IP ranges or geographic locations, often to reduce fraud or bot traffic.
3. Missing or Misconfigured .htaccess File
On Apache-based servers, .htaccess controls access rules. A misstep in this file, such as denying access to all users, can instantly trigger a 403 error.
4. No Index Page or Wrong Default Document
Web servers expect a default file, like index.html. Users may get a 403 error instead of a page if that file is missing.
5. Authentication Required but Not Provided
The server may block the request if a resource needs login access, but none is provided. This scenario differs from a 401 error, as a 403 means you’re already authenticated but not allowed in.
6. Access Control Lists (ACLs) or Firewall Rules
Firewalls and ACLs can restrict who can access certain parts of the system. If your request doesn’t meet the rules, you’ll be blocked.
7. Browser Cache
Sometimes, your browser responds with outdated cache data or cookies, which can cause the server to reject your request.
8. Token or API Key Issues
Missing, expired, or misconfigured API keys and tokens can cause 403 Forbidden errors. NHIs often rely on static tokens or long-lived credentials, which may silently expire or become misaligned with access policies. Without lifecycle automation, these identities can generate 403s with no clear root cause in logs.
9. Misconfigured IAM Policies or Access Roles
IAM roles define what users and systems can access in secure cloud environments like AWS, GCP, or Azure. If roles or policies are misconfigured, access can be denied even with valid credentials.
Let’s look at a quick example. In AWS, a Lambda function might receive a 403 if its execution role lacks permission to invoke a service, or if the trust relationship isn’t configured to allow Lambda to assume that role.
How can I fix the 403 Forbidden error?
403s in CI/CD pipelines often appear as failed stages in GitHub Actions or GitLab CI when secrets are missing, expired, or revoked; for example, when calling external APIs or protected resources. Integrating access validation steps into the pipeline can catch these early, and fixing a 403 error depends on who you are and what you control.
Below are fixes tailored for site owners, DevOps teams, and developers.
For Site Owners and DevOps Teams
These issues are often tied to server settings or cloud infrastructure.
1. Check File and Directory Permissions
- Make sure your website files and folders have the correct access settings.
- Use chmod to set permissions and chown to set ownership (on Linux).
- Common settings: folders should be 755, and files should be 644.
2. Review Server and Application Logs
- Check your server’s error logs for details about what caused the 403 error.
- Logs can show which file or rule is blocking access.
3. Inspect the .htaccess File
- The .htaccess file controls access rules.
- Look for lines like Deny from all that may be blocking users by mistake.
Order deny,allow
Deny from all
4. Check Firewall Rules or Security Groups
- Cloud platforms like AWS, GCP, and Azure support security groups to restrict access.
- Ensure the right ports are open and IP rules aren’t too strict.
5. Clear Browser Cache and Cookies
- Clearing outdated cookies ensures the browser isn’t sending bad information with each request.
For Developers
If you’re building or proactively testing apps, the issue may come from how the request is made.
1. Check Authorization Headers or Tokens
- Make sure your requests include the right headers.
- If you’re using OAuth or API keys, confirm they’re attached properly.
- For non-human identities, double-check that service tokens or workload identity bindings are configured with scoped access, especially in Kubernetes, CI/CD tools, or cloud automation scripts.
2. Verify API Access Permissions
- Ensure your API client or app has permission to call the endpoint.
- Double-check IAM roles or token scopes.
3. Rotate or Refresh Expired Tokens
- Many APIs use short-lived tokens.
- If yours is expired, generate a new one or refresh it through the provider.
4. Test from a Different IP or Network
- If you suspect IP blocking or geo-restrictions, try requesting another location (like using a VPN). It helps rule out location-based blocks.
How to Prevent 403 Forbidden Errors in the First Place
Although 403 errors may seem like isolated incidents, they usually have underlying issues related to permissions or identities. The following tips outline how to prevent 403 errors entirely.
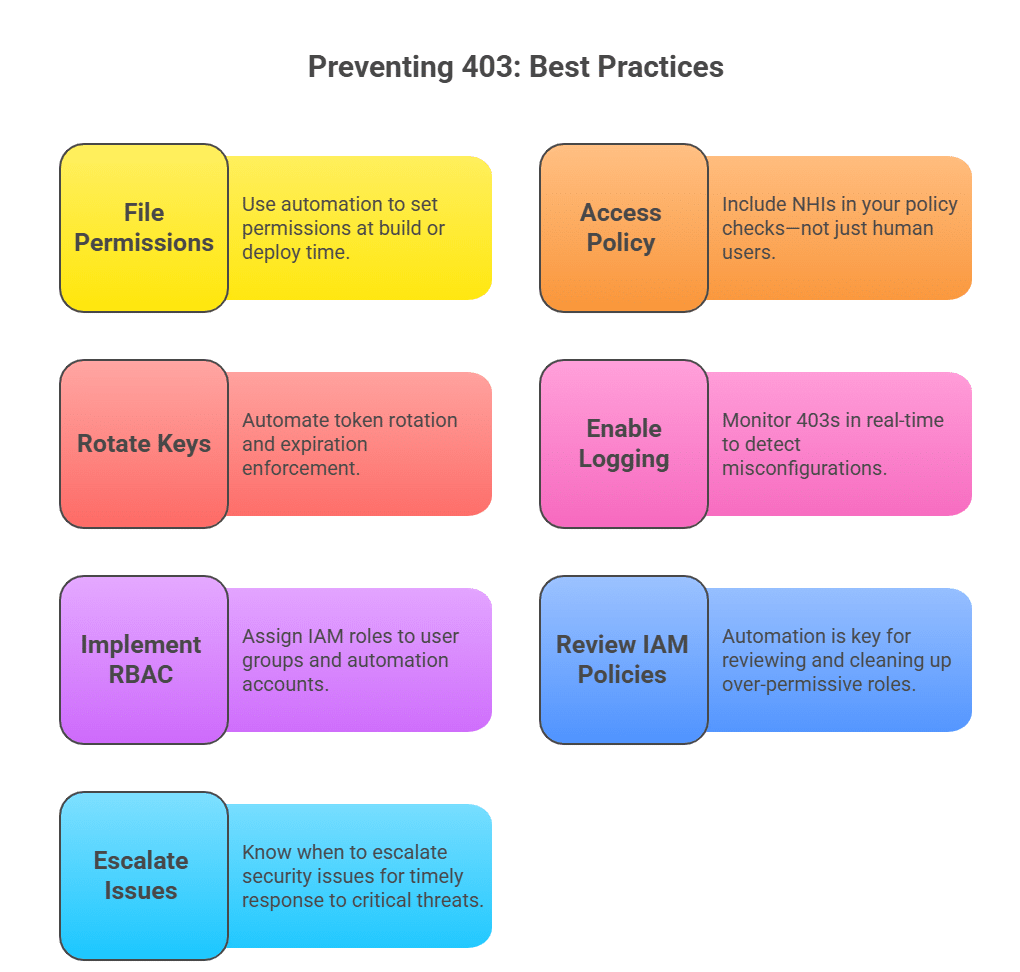
1. Set Correct File Permissions During Deployment
Don’t leave permissions to chance during CI/CD deployments. Use automation to set explicit file and directory permissions at build or deploy time.
Tips
- Use chmod 755 for folders and chmod 644 for public files.
- Don’t use overly permissive settings like chmod 777.
- Use CI/CD tools to enforce this step.
- Enforce Just-in-Time and Just-Enough Permissions to ensure access is granted only when needed, for the minimum required scope.
2. Automate Access Policy Validation
Manually reviewing IAM policies or firewall rules is error-prone and unsustainable as you scale. This best practice prevents someone from accidentally revoking access or overexposing resources.
Tips
- Use policy-as-code tools to detect access risks before they’re deployed.
- Include NHIs in your policy checks, not just human users. Validate that each service account, API caller, and automation tool has exactly the permissions it needs, and nothing more.
- Access misconfigurations are as risky as exposed secrets or unpatched services, meaning access control should be included in all vulnerability management best practices.
3. Rotate API Keys and Tokens Regularly
Long-lived tokens and hardcoded API keys commonly cause 403 errors, especially when they expire or are revoked. NHIs often use static credentials that never expire. Automating token rotation and expiration enforcement helps avoid 403s caused by credential drift.
Tips
- Automate key rotation every 30-90 days, as a minimum.
- Use short-lived, ephemeral tokens where possible.
- Store secrets in a vault.
- Implement webhook-based credential injection so tokens are never stored in config files.
4. Enable Logging and Real-Time Monitoring
Monitoring 403s in real-time helps detect misconfigurations before they impact users or pipelines.
Tips
- Log HTTP response headers for failed requests.
- Log IP address, user-agent, status code, and request path.
- Use alerting rules for error spikes.
5. Implement Role-Based Access Control (RBAC)
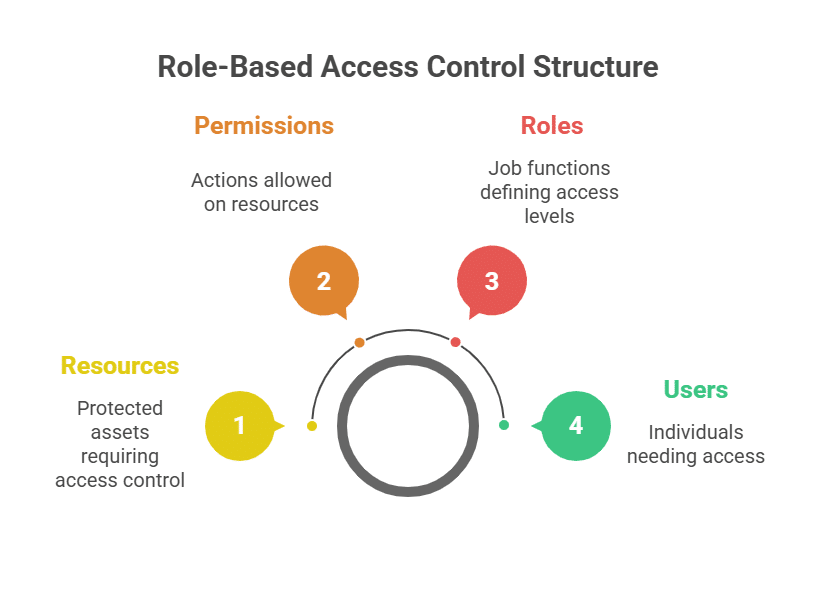
Grant access based on roles instead of individual users. For example, a developer might have full staging access but limited production access.
Tips
- RBAC helps keep your system secure by reducing the chance of unauthorized access.
- Assign IAM roles to user groups and automation accounts.
- Limit production access to approved roles only.
6. Review IAM Policies Automatically
In cloud environments, IAM policies can easily become messy. Automation is key for reviewing and cleaning up over-permissive roles.
Tips
- Apono, for example, helps streamline this by enabling Just-in-Time (JIT) access and least-privilege enforcement for machine identities that often get overlooked in traditional IAM reviews.
- Audit: Who has access to what? When was it last used? Is it scoped to what’s strictly necessary?
- Review both human and non-human identities. A common issue is over-permissioned service accounts that have access they don’t use, which violates least privilege and can result in access denial due to security guardrails.
7. Know When to Escalate
Not every 403 Forbidden error stems from your configuration. If you’ve already validated permissions, tokens, headers, and network rules—and the error persists—it may be time to escalate the issue. For example, some 403s may come from external systems rejecting an NHI that was previously whitelisted but has lost its token validity or falls outside the provider’s policy changes.
Tips
- Use a step-by-step root cause analysis framework to rule out internal misconfigurations and IAM drift.
- Collect the full HTTP request/response logs, headers, and timestamps.
- Check any recent changes in upstream systems, API versions, or identity configurations.
- Contact the support team of the service or vendor, sharing all relevant details to speed up triage.
Automate and Govern Access Decisions With Apono
403 Forbidden errors may seem small, but they can break pipelines and block users, ultimately slowing down fast-moving teams. These errors almost always come down to one thing: access mismanagement.
Missing or incorrect permissions, outdated IAM roles, expired tokens, and unauthorized non-human ones like service accounts and bots are common and often overlooked. Apono ensures both human and non-human identities receive only the access they need, when they need it, eliminating the root causes of most 403 errors in automated workflows.
Apono secures your environment while allowing teams to operate lean by enforcing least-privileged and JIT access for both users and machines. With Apono, you get:
- Time-bound access that auto-expires.
- Fine-grained access based on context (role, environment, request type).
- Full audit trails showing who accessed what and why.
- Policy-based workflows that prevent silent failures due to access gaps.
Struggling with identity sprawl or recurring 403 errors? If you’re dealing with access at scale, especially non-human identities, explore how Apono secures NHI and take control before the next pipeline break slows you down.






