API Gateway Security: The Essential InfoSec Guide

The Apono Team
June 17, 2025
As the software world shifted toward microservices and distributed architectures, the volume and complexity of API traffic have skyrocketed. Unfortunately, so has the number of API-related breaches and cyber attacks.
Last year, nearly 44% of all advanced bot traffic online targeted API endpoints, while traditional web applications received just 10% of the malicious traffic. It’s no surprise that 57% of organizations admit to having suffered API-related breaches in the past two years.
Your API gateway serves as the primary public-facing interface to your digital services. As such, its functionality and protection are often critical for business operations and your organization’s overall resilience against cyberattacks. Understanding how API gateways work (and where they fall short) is key to defending against API-related breaches.
How API Gateways Work
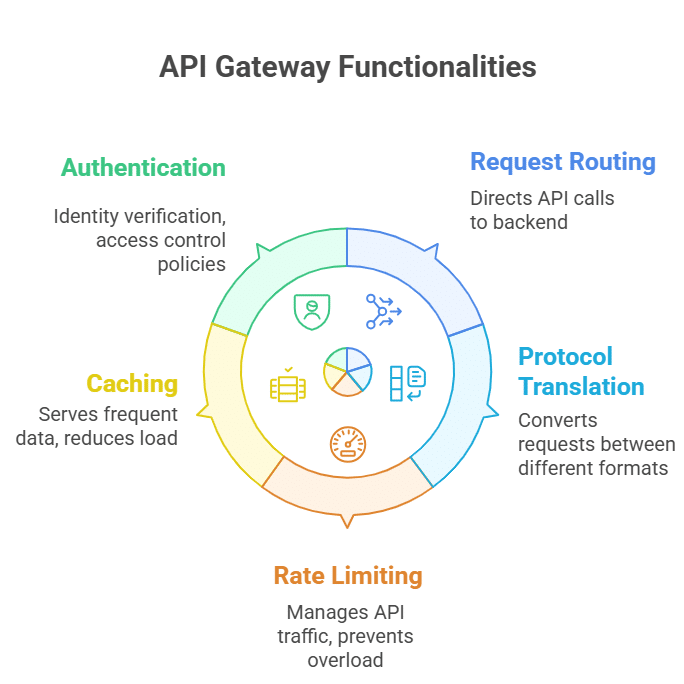
An API gateway acts as a front door to your API ecosystem. It sits between clients and backend services, centralizing the execution of common tasks to simplify architecture and enhance scalability. Key capabilities of an API gateway include:
- Request routing – Directs incoming API calls to the appropriate backend service based on predefined policies and rules.
- Protocol translation – Converts requests between different formats (like HTTP to WebSocket or REST to gRPC) to enable smoother interoperability.
- Rate limiting and throttling – Manages incoming API traffic to protect backend services from overload or abuse.
- Caching – Serves frequently requested data to reduce backend load and improve response times.
- Authentication and authorization – Performs initial identity verification and enforces high-level access control policies.
How does an API gateway improve security?
From an InfoSec perspective, an API gateway is the first line of defense against API-based threats. It can reject malformed or unauthorized requests before they reach internal systems, acting as a centralized API firewall that helps stop common attack vectors (like injection attacks, credential stuffing, and brute-force entry attempts) by enforcing strict schema validation and access policies.
Ideally, an API gateway reduces your attack surface by enforcing a consistent set of security policies, ensuring that only properly formatted, authenticated, and authorized requests are forwarded to backend services.
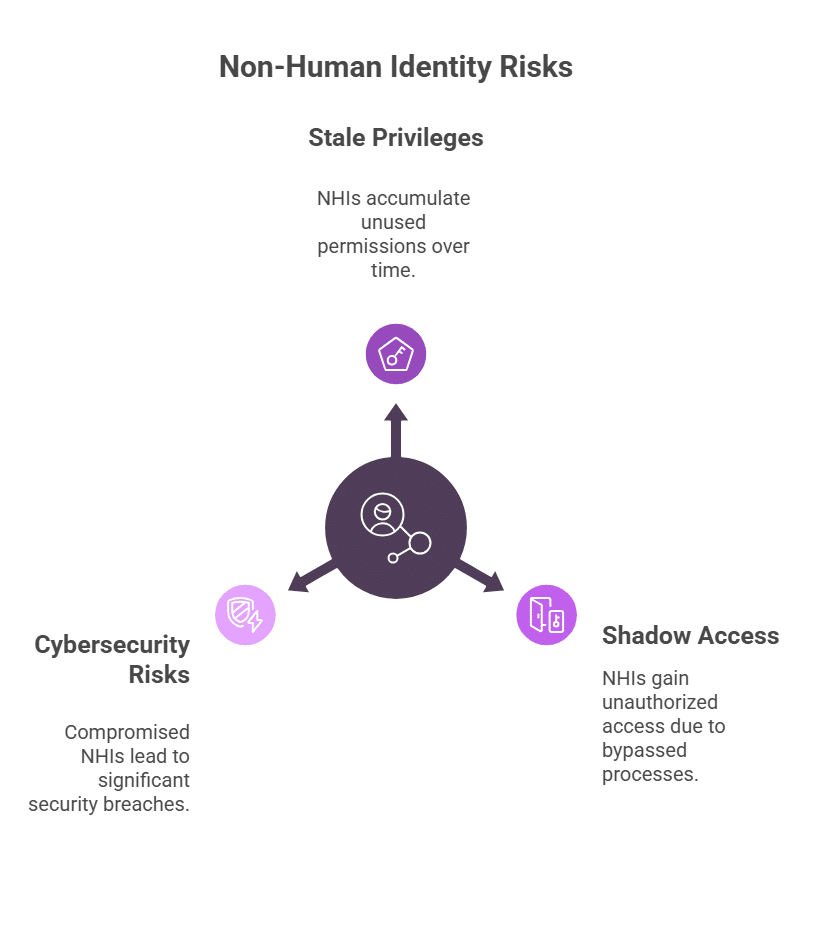
That said, API gateways have inherent limitations. Most lack the fine-grained, identity-aware access controls needed to manage non-human identities (NHIs) like service accounts, API keys, and tokens. Gartner estimates machine identities outnumber human identities by 45x. These machine identities often have broad, persistent access privileges, making them attractive targets in API abuse scenarios.
As your software architecture becomes more complex and your organization scales, this design limitation can evolve into a serious security gap. In fact, several organizations have already experienced high-impact breaches as a result.
Real-World Consequences of API Gateway Limitations
While API gateways are critical for managing traffic and providing initial authentication, their inherent limitations, especially around unmanaged and risky non-human identities (NHIs) with excessive access permissions, make them a primary vector for attacks.
The following real-world breaches from recent years illustrate just how dangerous these vulnerabilities can be.
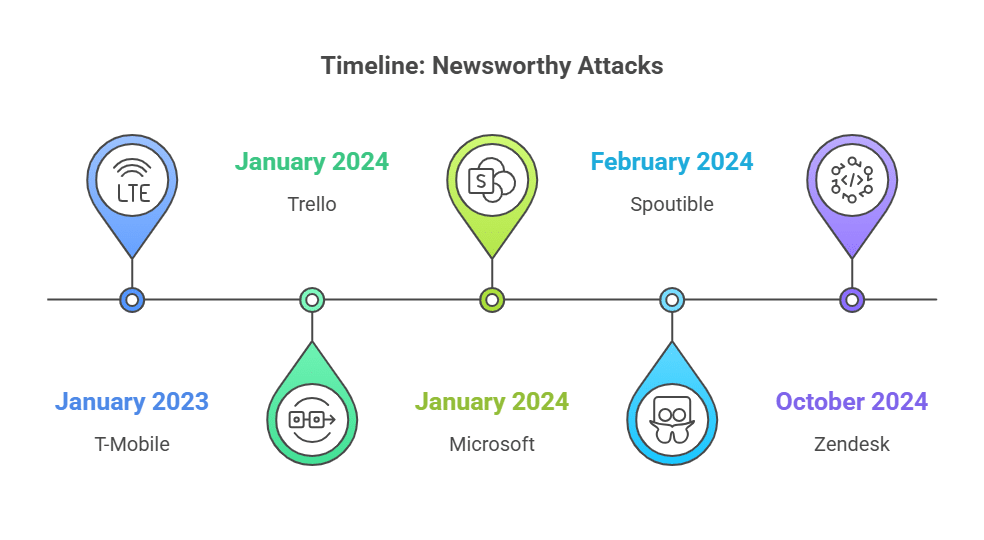
1. Trello: API Enumeration Exposed 15 Million Users
In January 2024, researchers found that Trello’s public API could be exploited to enumerate user accounts. Attackers scraped roughly 15 million profiles, including usernames, email addresses, and other personal identifiable information (PII), which they then offered for sale on the Dark Web. Although there was no system intrusion, attackers achieved data scraping of publicly available API endpoints.
2. Microsoft OAuth Application Compromise
The threat group APT29 compromised a non-production tenant account and then exploited a test OAuth application, which acted as an overprivileged non-human identity. This activity led to unauthorized access to Microsoft employee email accounts and demonstrated how NHIs can be leveraged for lateral movement, as documented in Microsoft’s blog.
3. Spoutible: Insecure API Exposed User Data and Credentials
Also, in early 2024, the social platform Spoutible suffered a breach due to multiple critical API vulnerabilities. These included broken authentication, inadequate token validation, and exposed endpoints. These flaws allowed attackers to access sensitive user data (including hashed passwords), highlighting serious gaps in data privacy and the lack of effective security controls to protect user information.
4. Internet Archive Zendesk Token Exposure
Attackers exploited unrotated API keys and Zendesk tokens, which are static non-human credentials, to gain access to approximately 800,000 support tickets from the Internet Archive. This incident underscored the critical importance of managing and securing NHIs, particularly in customer support systems.
5. T-Mobile: API Misuse Exposed SIM Data and User Metadata
In a headline-making breach in 2023, T-Mobile exposed the personal data of approximately 37 million customers due to a misconfigured API with overly permissive access to sensitive customer data. The data leaked included phone numbers, account metadata, and SIM card information that put users’ privacy at risk.
How API Gateways Fall Short in Authentication and Authorization (and How Access Management Platforms Can Help)
All these incidents expose a recurring pattern: static credentials and over-privileged service accounts. OAuth 2.0 client credential abuse is one of the most common non-human identity (NHI) abuse vectors, exploiting often long-lived and overly permissive access tokens.
In every case, the API gateway did its job (routing traffic and enforcing basic policies). Still, it failed to prevent the breach or leak as it lacked the identity-aware security layer with the granularity and dynamic nature required to effectively protect modern APIs in cloud environments.
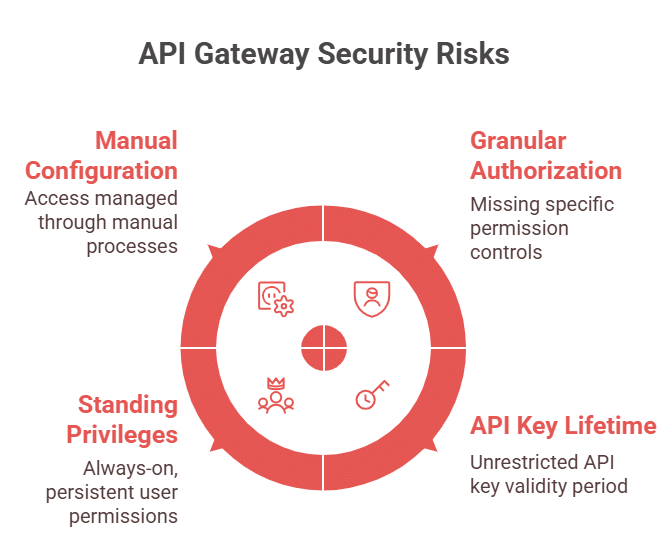
1. Lack of Granular Authorization
Most API gateways rely on binary access control: a user is either allowed or denied access based on high-level roles or tokens. They lack the ability to enforce “just enough” or context-specific permissions. This challenge highlights the need for a robust cloud-native access management platform like Apono. For example, Apono bridges this gap by enabling fine-grained authorization down to the API endpoint or database field level, ensuring users and services can access only what they truly need.
2. Unlimited API Key Lifetime
API gateways typically don’t support time-limited, conditional access for NHIs, meaning an API key, once issued, remains valid until manually revoked, regardless of context. If an API key is valid, it works, no matter when, how, or by whom.
Apono’s just-enough and JIT (just-in-time) access models grants temporary, on-demand permissions, which expire automatically. Enforcing just-enough access with a platform like Apono drastically reduces the risk of credential misuse if a key or service token is compromised.
3. Standing Privileges
Standing privileges are one of the most dangerous blind spots in API security. Gateways don’t track or limit persistent access by NHIs. Yet, an automated access management platform eliminates this risk by automatically revoking access once it’s no longer needed, shrinking the attack window for compromised access credentials.
4. Manual Access Management Configuration
Gateways often require manual configuration changes or ticket-based workflows to grant API access, slowing down engineering teams and increasing the risk of configuration drift. That’s why selecting a platform that integrates with tools like Slack, Teams, and the CLI is important, granting developers self-serve access to make requests safely and quickly without compromising on security or compliance.
Let’s look at an example. When paired with an API gateway, Apono brings the identity-aware, context-driven security that today’s API-driven environments demand and can close the gaps that API gateways alone simply aren’t designed to address.
Table 1: API Gateway Security Risks and Solutions
| API Gateway Security Risk | Solution (Using Access Management Platform) |
| Lack of granular authorization | Enable fine-grained authorization down to the API endpoint or database field level. |
| Unlimited API key lifetime | Enforce just-enough access to drastically reduce the risk of credential misuse if a key or service token is compromised. |
| Standing privileges | Automatically revoke access once it’s no longer needed, shrinking the attack window for compromised access credentials. |
| Manual access management configuration | Integrate the platform with tools like Slack, Teams, and the CLI, granting developers self-serve access to make requests safely and quickly. |
7 API Gateway Security Best Practices for InfoSec
When appropriately configured with the right stack and aligned with cybersecurity standards, API gateways can safeguard your systems from attackers and prevent unintended data leaks.
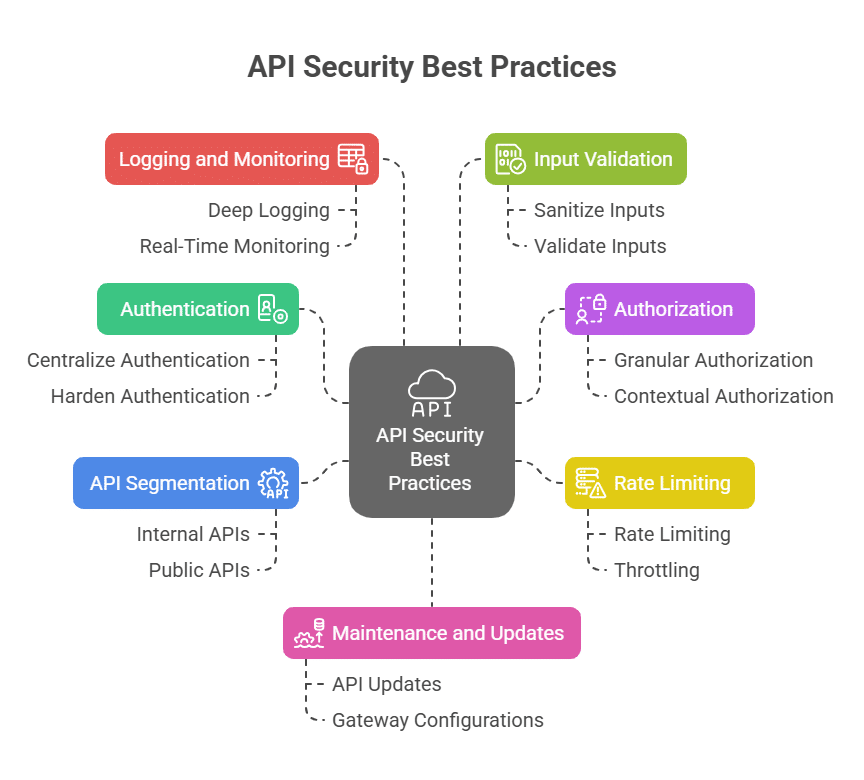
1. Centralize and Harden Authentication
To ensure a unified identity layer and avoid inconsistencies across services, use centralized authentication with standards like OAuth 2.0 or mutual TLS (mTLS). This best practice simplifies policy enforcement and reduces your attack surface. Configure your gateway to automatically reject requests without valid tokens (that are both signed and cryptographically validated).
2. Implement Granular and Contextual Authorization
While authentication confirms identity, authorization controls what that identity can do. Broad access controls often lead to excessive permissions. Apply role- and attribute-based access controls (RBAC/ABAC) at the API level. Integrate policy engines like OPA (Open Policy Agent), projects like Cedar (AWS), or gateway-native plugins to enforce least privilege consistently. This strategy helps reduce the blast radius if credentials are compromised, preventing attackers from achieving worst-case-scenario outcomes like remote code execution.
3. Apply Rate Limiting and Throttling to Curb Brute-Force Attacks
API gateways excel at managing traffic. To defend against brute-force tactics like credential stuffing, configure IP-based rate limiting, API key quotas, and per-client thresholds. Tailor these limits to each endpoint’s risk profile. Login and registration routes, for example, should have stricter controls and visibility.
4. Segment Protection of Internal and Public APIs
Treat public and internal APIs differently. Route internal traffic through a dedicated ingress path, reinforced by stricter firewall rules and identity lifecycle management policies. API gateways should support internal vs external routes with different ingress controllers or namespaces. Use gateway tags, virtual services, or separate gateways to enforce segmentation. Without clear separation, attackers can pivot laterally once inside the perimeter.
5. Enable Deep Logging and Real-Time Monitoring
Log every request, status code, authentication result, and header. These logs should integrate with your observability tools to help detect anomalies like spikes in 401/403 responses, sudden usage shifts, or repeated failures. Implement alerting rules to transform this data into real-time incident detection that your SOC team can act on.
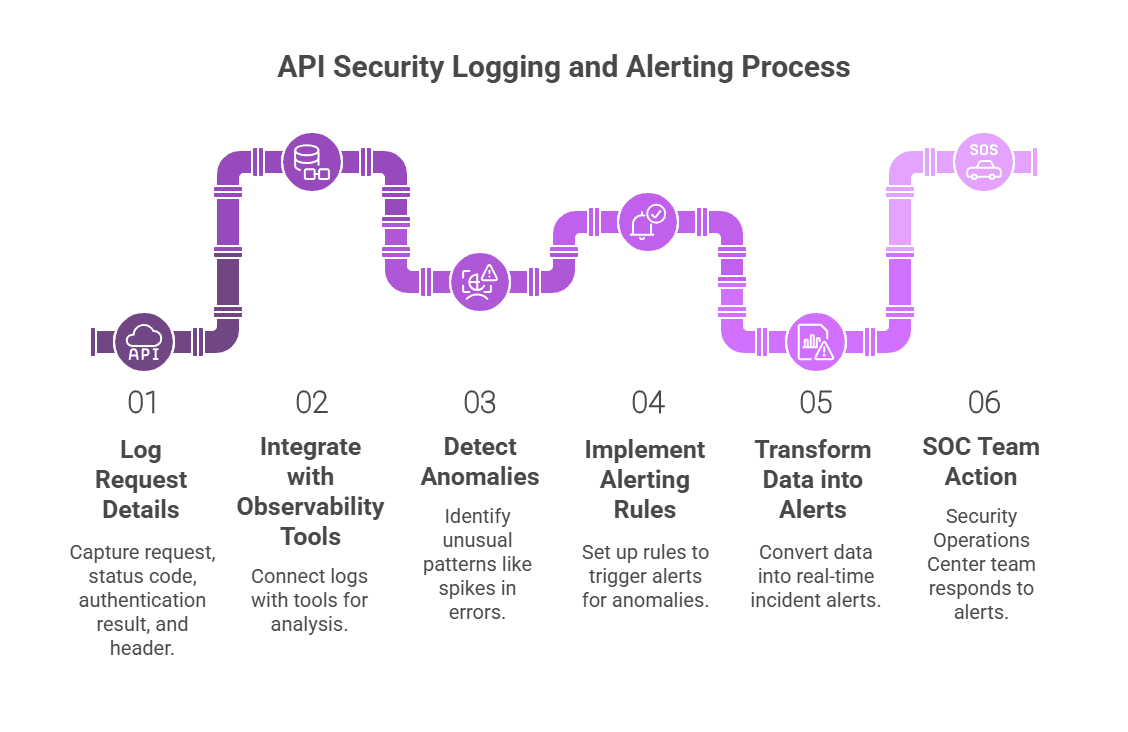
6. Sanitize and Validate Inputs at the Gateway
APIs are prime targets for injection attacks and schema abuse. Block malformed or malicious requests by enforcing JSON schemas, rejecting oversized payloads, validating query parameters, and performing JSON Web Token (JWT) validation. Many gateways support native request validation or allow you to layer WAF or custom middleware logic at the ingress point.
7. Maintain and Update APIs and Gateway Configurations
Unmaintained endpoints and hard-coded credentials are the leading causes of API-related breaches. Codify your gateway configurations and integrate them into your CI/CD pipeline. It supports versioning, deprecation enforcement, and secrets management. Maintain an updated API catalog and monitor for exposed or unauthorized endpoints in production.
Bridging the Authorization Gap with Apono
API gateways are essential for managing traffic, enforcing perimeter-level policies, and providing a first line of defense against API abuse. But as we’ve seen, their built-in capabilities fall short when it comes to fine-grained access control—especially for NHIs, which are prime targets for attackers. As we saw in the examples above, Apono helps to seal the gap in your API gateway security.
While your API gateway handles traffic routing, rate limiting, and basic authentication processes, Apono enforces the granular, context-aware access controls that define who (or what) those APIS can actually do. Automated Just-enough access helps to eliminate elevated standing privileges across your stack including machines without slowing down development.
Combined with comprehensive audit logs and automated reporting, Apono provides full visibility into every permission: who has it, how they got it, and why.Are you ready to close the gap in your API security strategy? Book a demo to see Apono in action.






