Identity Is NOT the New Perimeter, Context Is (Just Ask Security Vendors)

The Apono Team
July 29, 2025
In today’s cloud-native, remote-first world, identity alone can’t determine access. Security vendors are leading the shift toward context-aware controls — where who, what, when, where, and how — all factor into access decisions.
“Identity is the new perimeter” had its moment. But as cloud-native environments and distributed teams become the norm, this mantra is starting to show its age. The risks tied to static, identity-based access are now too big to ignore, and no one sees that more clearly than security vendors themselves.
They’re leading a quiet but critical shift toward context-aware access controls: smarter, more dynamic systems that evaluate not just who is requesting access, but whether that access makes sense in the moment.
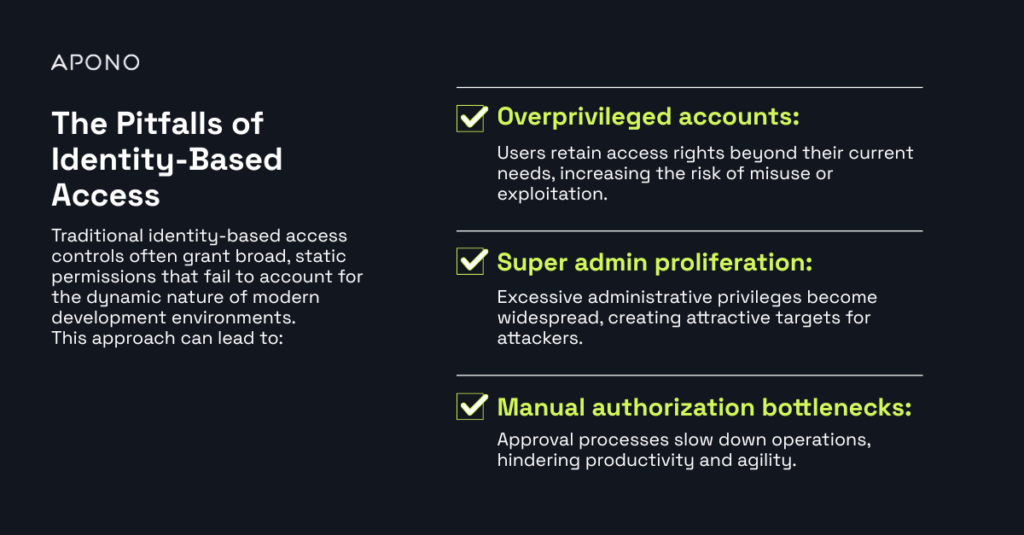
The pitfalls of identity-based access
Traditional identity-based access controls often grant broad, static permissions that fail to account for the dynamic nature of modern development environments. This approach can lead to:
- Overprivileged accounts: Users retain access rights beyond their current needs, increasing the risk of misuse or exploitation.
- Super admin proliferation: Excessive administrative privileges become widespread, creating attractive targets for attackers.
- Manual authorization bottlenecks: Approval processes slow down operations, hindering productivity and agility.
Moreover, access decisions that hinge on identity alone miss critical nuances. A developer may be authorized, but are they on a secure device? At the correct location? During an approved change window? Are they accessing a low-risk staging environment or a sensitive production one? Without considering these factors, it’s impossible to control secure access.
We’ve already seen the enormous cost of static, identity-only access models. During the 2023 Okta support system breach, attackers used a compromised service account to access customer support files via valid credentials. Identity checks alone failed to flag the activity – there were no controls to assess whether the device, IP address, or session behavior were normal. Context-aware controls could have raised alerts or blocked the session entirely. Instead, the attacker exfiltrated sensitive logs affecting multiple enterprise customers.
For security companies – often custodians of sensitive customer data and regulatory compliance – these gaps introduce unacceptable levels of risk. Worse still, an internal access control failure can undermine the very credibility on which a security company is built.
Embracing contextual access control
However, context-based access controls, like Apono’s, overcome these pitfalls by evaluating multiple contextual controls before granting access. They are:
- User identity: Who is trying to access the resource?
- Device identity: Does the device identity match the user identity?
- Device health: Is the device secure and compliant?
- Resource sensitivity: What is the risk level of the resource?
- Time & location: Is the access request at an appropriate time and location?
- Access History/Behavioral Baseline: Is this access normal for this user?
- Workload/Task Context: Is this part of a sanctioned workflow?
Considering context in access decisions also enables Just-in-Time (JIT) and Just-Enough-Privilege (JEP) access, further enhancing our customers’ security postures.
In short: Context = Identity + Environment + Intent Again, this shift is especially valuable for security vendors, whose internal controls must not only be strong, they must be demonstrably best-in-class.
Context’s role in Just-in-Time (JIT) access
JIT access determines when access is granted, and for how long. It limits the time window during which elevated privileges exist, thereby shrinking the attack surface and reducing the standing privilege.
Contextual access controls provide the information necessary to decide when to grant temporary access and how long for.
For example, if an administrator attempts to troubleshoot a server issue during off-hours from a known location and using a managed device, a contextual system can trigger a JIT workflow to grant temporary, time-limited access to that server. Access is automatically revoked once the issue is resolved or the access window expires.For security companies, JIT reduces the blast radius of credential theft or account compromise, ensuring that even a breach yields little value to attackers.
Context’s role in Just-Enough-Privilege (JEP) access
Just-Enough-Privilege (JEP) determines what access is granted, based on the specific task and situation. Unlike broad role-based access, JEP utilizes real-time context to apply least privilege principles dynamically.
Context-based access controls allow for highly granular controls over permissions. Instead of granting broad role-based access that might include unnecessary permissions, these systems can tailor access exactly to the task at hand and the current circumstances.
For example, a user might generally have access to a specific application, but a contextual access control system could limit their ability to export sensitive data from that application if they are accessing from an untrusted device or outside of business hours.
Context-based access in action

Take EverC, a FinTech SaaS provider managing over 20 sensitive databases. Manual access provisioning created security bottlenecks and compliance risks. With Apono’s contextual access controls, EverC eliminated hours of administrative overhead, accelerated developer access, and improved compliance with ISO 27001 and SOC 2.
Security companies know poorly managed access is not just a technical flaw; it’s a reputational and commercial liability. That’s why forward-thinking vendors are embracing JIT & JEP controls, not just to secure their stack, but to stay competitive.
Want to secure your infrastructure without slowing your team?
View Our Solution Brief to see how contextual access, JIT, and JEP can reduce risk, eliminate standing privileges, and boost compliance, all without sacrificing speed.

Or dive deeper: Download our security-focused eBook, “The Security Leader’s Guide to Eliminating Standing Access Risk” to explore the full strategy and implementation insights.