Legacy PAM vs. Cloud PAM: Why Just-in-Time Access (JIT) Matters Now

Gabriel Avner
January 7, 2026
Privileged access programs were designed for environments where access could be defined ahead of time. That assumption no longer holds in the cloud.
Legacy PAM emerged in a world of static infrastructure, long-lived systems, and a relatively small number of privileged users. Access patterns were predictable. Roles could be created in advance, assigned broadly, and reviewed periodically. That model was imperfect, but it worked well enough.
Cloud environments operate at a very different pace. Infrastructure is created and changed continuously. Identities appear and disappear through automation. Privileged access is no longer limited to administrators. It is used constantly by developers, CI pipelines, service accounts, and increasingly AI-driven systems operating across production environments.
For cloud security teams, this shift turns privileged access into a dynamic security problem. Static access models struggle to keep up.
This is why the move from legacy PAM to Cloud PAM is not incremental. It is architectural.
Why the Cloud Broke Static Privileged Access
The move to the cloud changed how access behaves, not just where systems run. Several shifts matter most for cloud security teams.
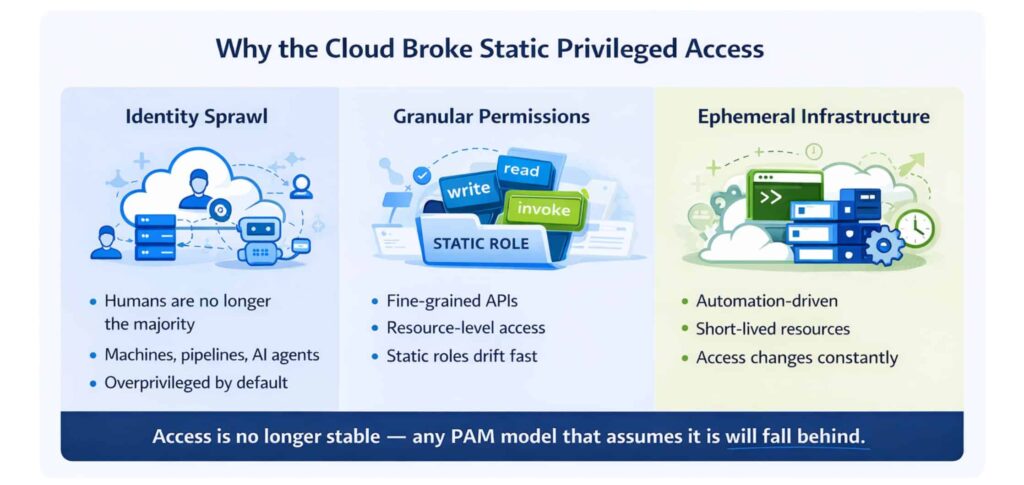
Identity sprawl across humans, machines, and AI
Human users are now outnumbered by service accounts, pipelines, automation, and third-party integrations. These identities are often overprivileged and difficult to monitor at cloud scale. AI agents add further risk by introducing access patterns that cannot be fully predicted upfront.
Granular permissions
Cloud platforms expose fine-grained permissions at the API and resource level. Least privilege is achievable, but only if access can be adjusted dynamically. Broad, static roles quickly become misaligned with real usage.
Ephemeral infrastructure
Cloud resources are created and changed continuously by automation. Access needs evolve just as quickly, leaving static roles and predefined permissions struggling to stay relevant.
Together, these shifts make one thing clear. Access needs are no longer stable. Any PAM model that assumes they are will fall behind.
Why Static PAM Fails in the Cloud
Legacy PAM struggles in the cloud not because it is slow or manual, but because it is static by design.
Static PAM assumes access needs can be modeled in advance. Roles are pre-created. Approval paths are fixed. Privileges are granted long before they are actually needed, then reviewed periodically to correct drift.
That approach worked when systems changed slowly. In cloud environments, it produces predictable problems.
- Privileged roles expand to cover new services and workflows
- Standing access becomes the default because removal feels operationally risky
- Reviews lag behind reality and turn into reactive cleanup
- Security teams spend more time maintaining access models than enforcing outcomes
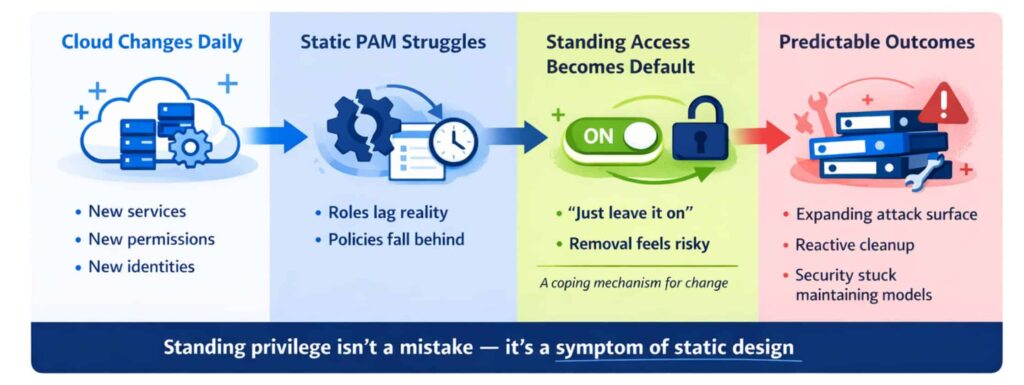
At cloud speed, access needs change continuously. New services, permissions, and identities appear daily. Static models require teams to anticipate these changes and update roles and policies ahead of time. That work inevitably falls behind.
Standing privilege becomes a coping mechanism for change, even as it increases risk. This is a structural limitation of static access models in dynamic environments.
How Cloud PAM and Just-in-Time Access Change the Model
Cloud PAM refers to privileged access systems built specifically for cloud environments, integrating directly with cloud control planes and APIs rather than relying on vaults, jump hosts, or session proxies. But Cloud PAM alone is not enough. Many Cloud PAM solutions still rely on pre-created roles and static permission models, which reintroduce standing access even in cloud-native architectures.
The real shift comes from Just-in-Time privileged access. Just-in-Time access changes how privileged permissions are granted, used, and removed. Instead of existing permanently, privileged access is provisioned only at the moment it is needed. Zero Standing Privilege builds on this model by making Just-in-Time access the default. Privileged access does not exist unless it is explicitly requested, approved if required, and granted for a limited duration.
Rather than relying on long-lived roles, Just-in-Time access delivers permissions that are scoped to the specific task, enforced at request time, and automatically revoked when the task is complete. This approach aligns privileged access with how cloud environments actually operate and eliminates standing privilege as a byproduct of static design.
In practice, Cloud PAM aligned with Just-in-Time access means:
- Privileged access is temporary rather than permanent
- Access decisions are made at request time
- Context such as environment and resource sensitivity informs access
- Privilege expiration is enforced automatically
For cloud security teams, this turns privileged access into a continuous control rather than a corrective process.
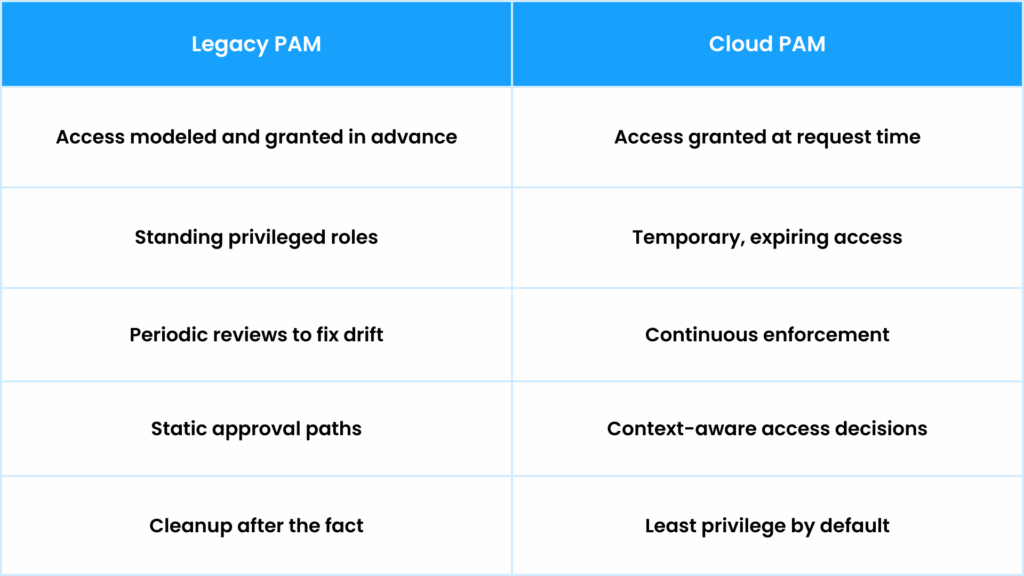
Legacy PAM vs. Cloud PAM at a Glance
Legacy PAM was designed for static infrastructure. Cloud PAM is built for environments that change constantly. This comparison shows how those models diverge in practice.
How Apono Makes Zero Standing Privilege Work at Cloud Speed
Apono was built to implement Cloud PAM in a way that truly supports Zero Standing Privilege at cloud scale.
Rather than requiring teams to pre-create and maintain privileged roles, Apono dynamically creates ephemeral roles at request time. Permissions are assembled based on context and the specific task being performed. Access is granted Just-in-Time, scoped Just-Enough, and removed automatically when no longer needed. This allows organizations to eliminate standing privilege without constantly rebuilding role models as environments evolve.
Static Access Cannot Secure a Dynamic Cloud
Cloud environments are not slowing down. Neither is the risk created by static privileged access.
For cloud security teams reassessing how access is granted, reviewed, and revoked, the next step is understanding where standing privilege still exists and how Just-in-Time access can replace it.

If you’re exploring Cloud PAM options, our Privileged Access Buyer Guide + RFP Checklist can help. It walks through the capabilities that matter most for operationalizing Zero Standing Privilege and offers clear guidance for comparing cloud-native approaches with legacy PAM solutions.






