Selling to Regulated Customers: 5 Requirements You Need to Know and Prove

Gabriel Avner
February 19, 2026

So you’ve got a groundbreaking product that has outstanding market fit. Your prospects love it and are raring to buy. Amazing. But before they can hit approve on the order, they need to make sure you’re SOC 2 or ISO 27001 compliant because their compliance officer won’t let them work with any vendor that hasn’t passed their audit. This is the joy of selling to regulated customers — which today, let’s be honest, is almost everyone. If you handle, process, or integrate with sensitive data, your buyers are going to hold you to a higher security standard.
And if your access practices don’t measure up, you don’t just put yourself at risk — you put them at risk. So how do you show that your security is enterprise-grade?
Who Are Regulated Customers?
Yes, healthcare, banking, and insurance are the obvious regulated industries. But in reality, almost every organization that collects, stores, or transmits personal or sensitive data falls under some kind of regulation.
That means your prospects might range from a fintech startup processing payments to an e-commerce brand storing customer addresses, or even a SaaS that integrates with payroll or HR data.
If they handle regulated data, you need to prove that you can protect it.
Common Regulations Across Verticals
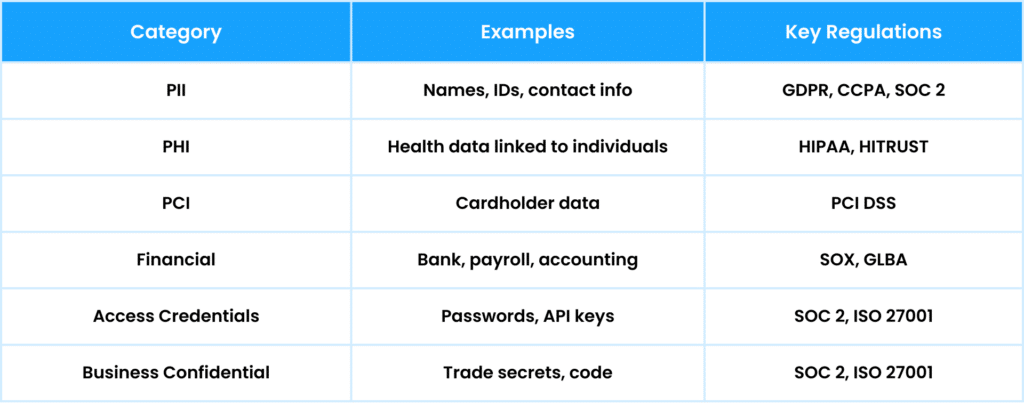
Common Access Security Principles Across All Frameworks
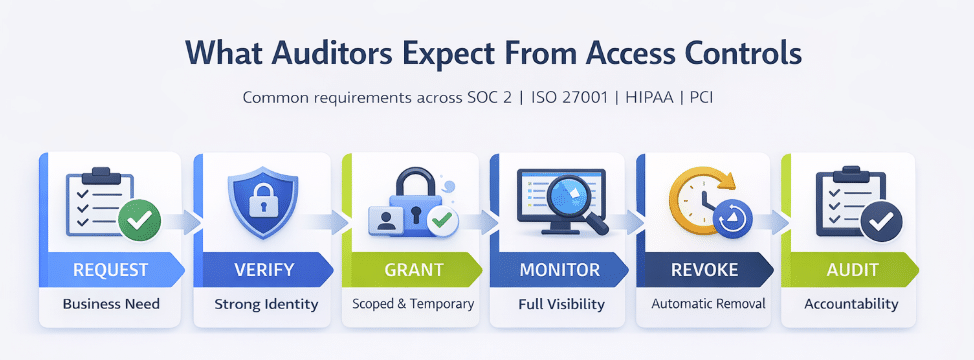
No matter which regulation your buyer cites, the core controls are the same. Auditors want to see that access is limited to what’s needed, granted only when required, and fully traceable. If you can show these basics are operational every day, you’re already speaking their language.
- Limit access based on least privilege and business need
- Require strong authentication (MFA, unique IDs)
- Review and revoke access regularly and on role changes
- Log and monitor all access to sensitive systems
- Maintain segregation of duties to prevent misuse
- Provide visibility and accountability for every access decision
What Regulated Customers Care About
Security Risks
For your buyers, vendors are often their biggest exposure point. Attackers increasingly target the supply chain — the third-party vendors, tools, and integrations that connect into their systems. If one of your privileged accounts or API tokens is compromised, an attacker can use it as a doorway into your customer’s environment. Even if the breach happens on your side, your customer takes the hit.
This is exactly what we saw in the Salesloft-Drift supply chain breach — and why access security now dominates vendor assessments.
In August 2025, attackers from UNC6395 compromised OAuth tokens used by Drift, an AI chat tool integrated with Salesloft. Those tokens granted access to customer systems like Salesforce, exposing data such as AWS keys and Snowflake tokens. The impact? Over 700 organizations were affected, and the breach spread across connected platforms including Google Workspace, Slack, AWS, and Microsoft Azure.
The lesson is simple: even trusted integrations can become attack vectors if access isn’t temporary, scoped, and auditable.
Compliance Requirements
Compliance is what turns security from a “nice-to-have” into a deal-breaker.
If your customer is audited and their vendors don’t meet the same standards, they fail. That’s why many buyers won’t even begin procurement until they see SOC 2, ISO 27001, or HIPAA-aligned controls in place. It’s the transitive property of compliance: your security posture becomes theirs.
What Companies Need to Know Before Selling to Regulated Customers
1. You’re Part of Their Compliance Boundary
The moment you process regulated data, you’re inside your customer’s compliance scope. Expect detailed security questionnaires, proof of least-privilege enforcement, and visibility into how you manage privileged accounts, contractors, and integrations.
2. Access Security Is Non-Negotiable
Buyers want evidence that:
- Privileges are Just-in-Time and removed automatically
- Zero Standing Privileges is enforced in production environments
- All access is approved, logged, and monitored
These aren’t just security best practices. They’re now procurement requirements.
3. Compliance Is the Starting Line
SOC 2 or ISO 27001 certification is no longer a differentiator; it’s table stakes. What stands out is your ability to demonstrate continuous control and operational maturity, not once-a-year audits.
4. Transparency Builds Trust
The easiest way to win over risk and compliance teams is to make their job easier. Offer a trust portal, share policies and certifications, and clearly explain how your access controls protect their data. Transparency accelerates approvals.
5. Compliance Requires Consistency, Not Exceptions
Regulated customers are wary of access models that rely on exceptions, one-off approvals, or manual workarounds to function in production. Even if individual exceptions are justified, they erode confidence in the control environment and create audit risk over time.
To pass compliance reviews, companies must show that privileged access is handled consistently through policy, not through ad-hoc decisions — with the same rules applied across users, environments, and systems.
How Apono Helps You Sell to Regulated Customers
If you’re trying to close enterprise or regulated deals, you need to show that your access security is airtight — not just once, but every day. That’s exactly what Apono enables.
- Demonstrate least privilege by default
Apono enforces granular, role- and resource-level permissions across clouds, databases, and SaaS platforms. Our dynamic, ephemeral role creation on the fly ensures that your access aligns automatically with your specific business needs. - Implement Just-in-Time and Enable Zero Standing Privileges
Permissions are granted only when required and revoked right after use, shrinking your attack surface and satisfying customer compliance checks. - Automate access reviews and audit evidence
Every access request is logged and auditable, so you can deliver SOC 2 or ISO 27001 evidence without manual effort. - Secure Non-Human Identities and Integrations
Apono discovers and manages service accounts, API keys, and automation tokens — the same weak spots exploited in the Salesloft-Drift breach. - Integrate seamlessly with your stack
Connects directly via API with Okta, Entra ID, AWS, GCP, and Kubernetes — no proxies, no added friction for engineers.
With Apono, you can walk into any regulated customer conversation knowing you can prove least privilege, auditable access, and modern compliance.
Because when you sell into regulated industries, the deal doesn’t hinge only on your product — it hinges on your security. And with Apono, you’ve got both.
Ready to win regulated customers with confidence?
When security becomes part of the sales conversation, you need more than certifications. You need proof that your access controls are continuous, enforced, and audit-ready in real environments.
Apono helps you:
- Eliminate standing privileges in production
- Enforce Just-in-Time, least-privilege access by default
- Deliver clear, defensible audit evidence instantly
- Reassure security and compliance teams during procurement
Don’t let access risk slow down your next enterprise deal.







