Top 10 Identity Lifecycle Management Tools

The Apono Team
June 12, 2025

Often overlooked, identities are prime targets for bad actors. In December 2024, a compromised API key in the BeyondTrust Remote Support SaaS environment was enough to cause a privilege escalation attack. The year before, Microsoft hit the headlines as an SAS token leak exposed over 38TB of sensitive data.
The good news is that simplifying user access and eliminating security risks from standing privileges has never been more achievable thanks to the right identity lifecycle management (ILM) tools.
With the rapid growth of non-human identities (NHIs), such as service accounts and APIs, the importance of smart automation in identity management is soaring. As a result, 78% of organizations are gearing up to boost their Identity and Access Management (IAM) spending in 2025, including on ILM tools.
10 Best Identity Lifecycle Management Tools at a Glance
- Best overall for Cloud privilege access management: Apono
- Easiest integration with the Microsoft ecosystem: Microsoft Entra ID
- Best for comprehensive enterprise identity governance: SailPoint IdentityIQ
- Best for SaaS integrations: Okta
- Best for converged identity & privileged access security: CyberArk Identity
- Best for SMBs: JumpCloud Identity Lifecycle Management
- Best for large enterprises & complex hybrid environments: Ping Identity
- Best for user-friendly SSO: OneLogin
- Best for developers building custom app authentication: Auth0 (by Okta)
- Best for Oracle-centric enterprises: Oracle IAM
What are identity lifecycle management tools?
Identity lifecycle management refers to the entire process of managing a user’s digital identity and their associated access privileges from the moment an identity is created until it is deprovisioned.
Identity lifecycle management tools are software solutions designed to automate and streamline complex processes. They are crucial for handling tasks such as automated provisioning and deprovisioning for both human and non-human identities (NHIs) and just-in-time (JIT) access, as well as implementing robust role and policy-based access control (RBAC and PBAC).
Automating these functions significantly reduces manual effort and enhances your organization’s overall security posture. ILM tools provide a centralized platform for:
- Managing user accounts: This encompasses the creation, modification, and deletion of user accounts across various systems and applications. For example, handling changes in employee status.
- Assigning permissions: Identity lifecycle management tools enable the precise assignment of access rights and privileges to users based on their roles, responsibilities, and specific business needs.
- Enforcing policies: These tools are instrumental in enforcing organizational security policies and compliance mandates in line with requirements like GDPR and SOC 2.
- Maintaining an audit trail for compliance: Meticulously recording all identity-related activities and access events.
Types of Identity Lifecycle Management Tools
While many identity lifecycle management (ILM) solutions offer a broad range of capabilities, understanding these distinctions can help you identify the right one for your needs.
- Identity Governance and Administration: Focuses on governance by managing digital identities and access rights, enforcing policies, conducting access certifications, and ensuring compliance. Provides visibility into who has access to what.
- Access Management: Deals with how users (human and non-human) authenticate and authorize access. Includes SSO, MFA, API security, and adaptive access policies, ensuring only authenticated and authorized users reach resources.
- Privileged Access Management: Secures and manages highly sensitive accounts and credentials (e.g., administrators and service accounts). Controls, monitors, and audits privileged access to critical systems, often with session recording and just-In-time (JIT) access.

Benefits of Identity Lifecycle Management Tools
- Enhanced security: ILM tools are your secret weapon for enforcing least privilege, ensuring every single identity (human or non-human) gets precisely the minimal access it needs.
- Improved operational efficiency: Automating identity processes cuts manual overhead, freeing up teams for strategic work.
- Simplified compliance & auditing: ILM tools offer clear visibility into access for regulatory compliance and easier audits.
- Better user experience: Self-service portals in ILM tools mean quicker access requests and smoother onboarding for human users.
- Reduced human error: Automating identity lifecycles minimizes manual mistakes that can create vulnerabilities or access issues.
What key features should you look for in an identity lifecycle management tool?
Unified Identity Management
Several key features are essential for robust security and efficient operations when selecting an identity lifecycle management tool. First, the tool should seamlessly integrate with all major cloud platforms, your preferred DevOps tools, and CI/CD pipelines for a unified approach to identity management.
JIT Access
Second, the ability to enable just-in-time (JIT) access is vital. This dynamic approach grants precisely scoped, temporary permissions that automatically disappear when no longer needed. JIT access eliminates risky standing privileges, preventing prolonged exploitation, as seen in incidents like the Internet Archive Zendesk Token Exposure in 2024, which involved unrotated API keys.
Automated Provisioning & Deprovisioning
Look for automated provisioning and deprovisioning capabilities that streamline efficient onboarding, role changes, and offboarding. This feature is crucial given that compromised non-human identities are increasingly leveraged in real-world attacks. For instance, the Okta Support System Breach in October 2023 involved a compromised service account that lacked sufficient monitoring, allowing attackers to steal customer credentials.
Security for NHIs
Robust non-human identity (NHI) support is a must. The best tools specifically manage the unique lifecycle and security needs of NHIs, such as service accounts and API keys, with the same rigor applied to human users.
Granular Access Control
Self-serve, granular access control allows for fine-grained control over permissions, dynamically leveraging attributes and context, like time or location, to create highly specific access policies.
10 Top Identity Lifecycle Management Tools
1. Apono

Apono is a cloud-native access management platform that modernizes identity lifecycle management by automating just-in-time (JIT) and least privilege access. Apono manages access dynamically, granting precisely scoped, temporary privileges for identity’s that are automatically revoked. It ensures all identities (both humans and non-humans) have the right access to do just what is needed, helping bring zero trust to all your identities. With Apono you can:
- Streamline onboarding and offboarding for all identities and provides detailed audit logs to enhance lifecycle visibility.
- Enable on-demand, self-serve, granular permissions directly from Slack, Teams, or your CLI and integrates with various cloud providers.
- automatically suggest dynamic policies that fit your business needs, streamlining cloud access lifecycle and gaining control of cloud privileged access.
Best overall for Cloud privilege access management.
Price: By inquiry.
Review: “As head of IT, It gives me peace of mind when I know that only the right users get proper access to the system’s DB at the right time; with Apono I don’t need to worry about managing DB privileges since Apono makes sure that the key is automatically revoked upon completion.”
2. Microsoft Entra ID (formerly Azure Active Directory)
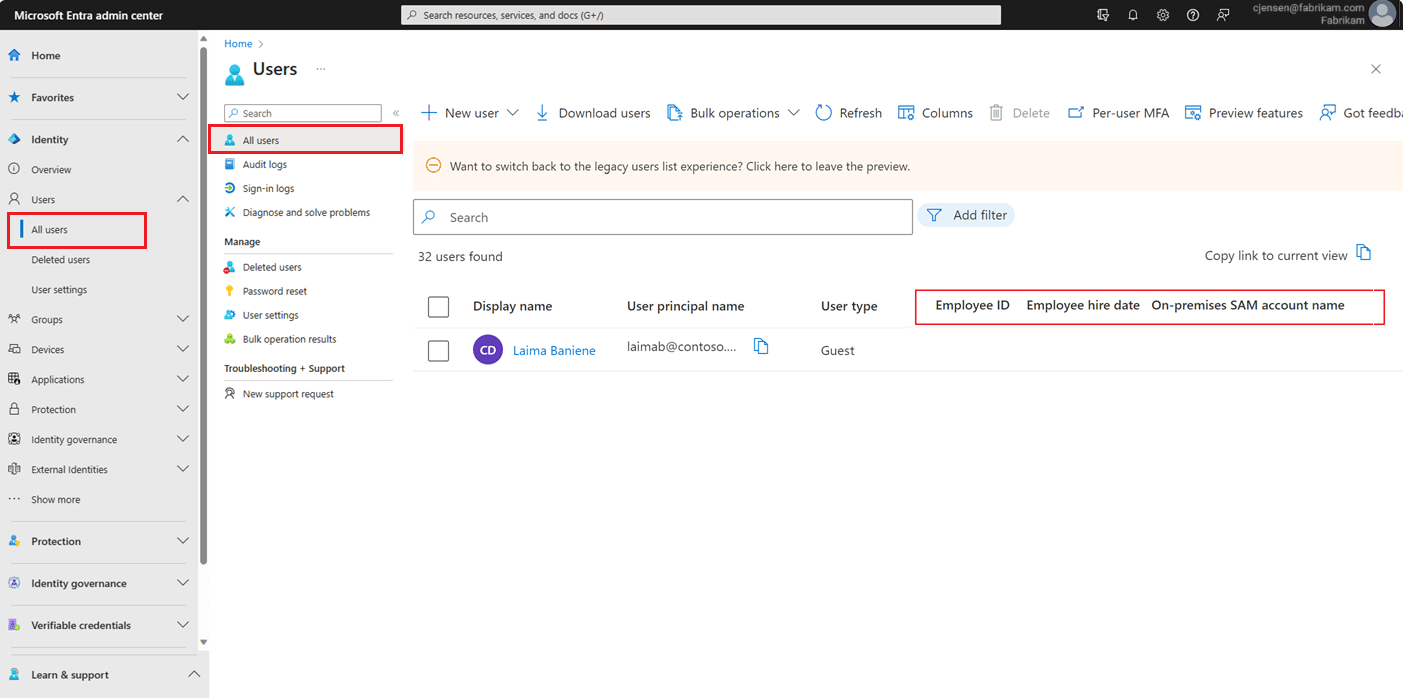
Microsoft Entra ID, formerly Azure Active Directory, is Microsoft’s cloud-based IAM solution. It is a central hub for managing user identities and controlling access to applications and resources, both within the Microsoft ecosystem and for third-party services. Its features include single sign-on (SSO), multi-factor authentication (MFA), and lifecycle workflows for human users.
Price: Offers a free tier and various paid editions (e.g., Premium P1, Premium P2) with per-user pricing.
Best for: Easiest integration with the Microsoft ecosystem.
Review: “It offers seamless integration with Microsoft 365 and Azure services, strong identity protection, SSO, and conditional access policies.”
3. Ping Identity

Ping Identity provides an enterprise-grade identity platform for securing customer and workforce access. It offers a range of authentication, authorization, and identity governance solutions, API security capabilities, and flexible deployment options (cloud, on-premises, hybrid).
Price: By inquiry.
Best for: Large enterprises & complex hybrid environments.
Review: “Ping Identity is super easy to use and configure; their support team has helped us with any issues we’ve had during setup.”
4. OneLogin

OneLogin, now part of One Identity, is a cloud-based platform offering secure single sign-on (SSO), multi-factor authentication (MFA), and lifecycle automation. It simplifies access control by centralizing identity management in a single directory, helping organizations sync user data across applications and enforce consistent security policies.
Price: By inquiry; tiered pricing based on features and user count.
Best for: User-friendly SSO.
Review: “Remembering one passphrase that gives me access to all my corporate applications is as simple as it can get.”
5. Auth0
Auth0 is an identity platform designed to support developer productivity by simplifying the implementation of authentication and authorization within custom applications. It provides tools for building secure identity services in web, mobile, IoT, and backend applications.
Price: Offers a free developer plan, then tiered pricing based on active users and features.
Best for: Developers building custom app authentication.
Review: “What I really like about Auth0 is its flexibility in authentication flows. I can easily set up social login and multi-factor authentication.”
6. SailPoint IdentityIQ
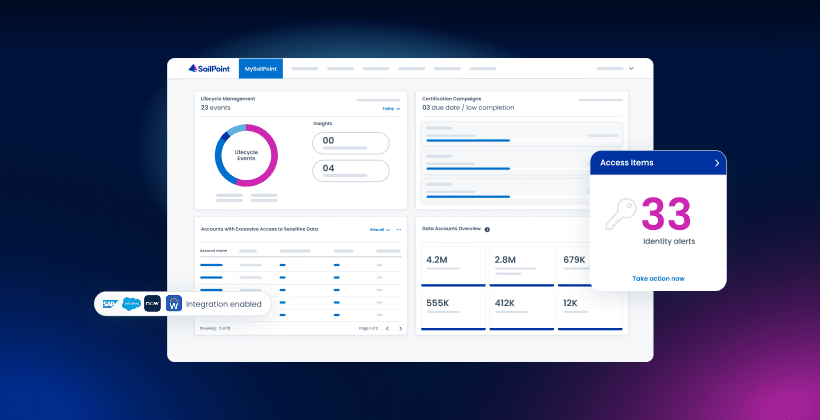
SailPoint IdentityIQ is a comprehensive identity governance and administration (IGA) solution that helps large organizations manage digital identities and access rights. It offers automated provisioning and deprovisioning to streamline identity lifecycle management, plus robust reporting capabilities.
Price: By inquiry.
Best for: Comprehensive enterprise identity governance.
Review: “The most helpful feature is its ability to automate access reviews and policy enforcement, which simplifies managing user permissions and ensures everything stays secure.”
7. Okta
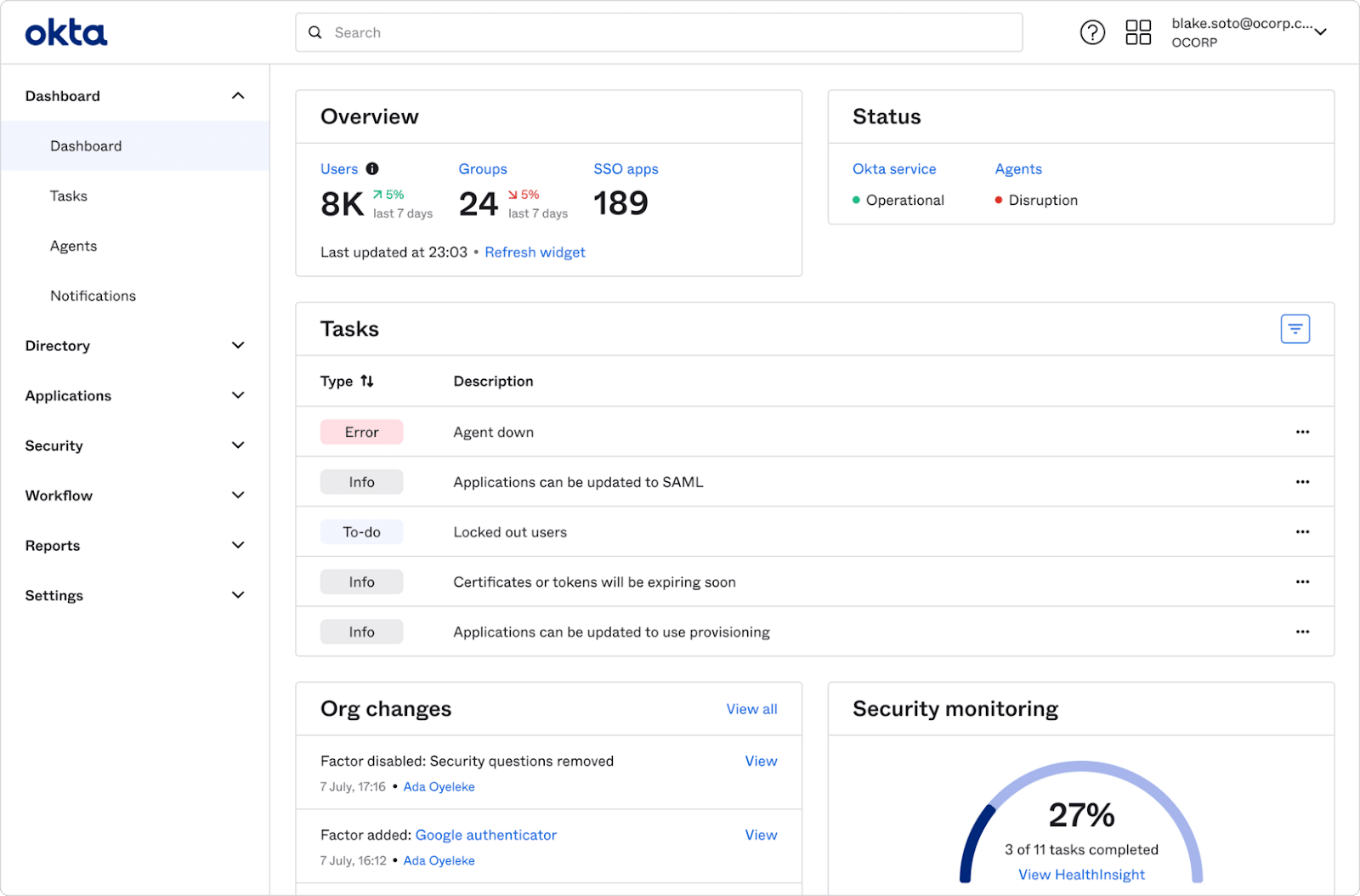
Okta is an identity provider that offers a cloud-based platform for managing and securing workforce and customer identities. It supports SSO, MFA, API access management, and automated user provisioning and deprovisioning across various applications and services.
Price: By inquiry. Pricing varies based on features and user count.
Best for: SaaS integrations.
Review: “What I like best about Okta is that it [provides] one-step sign-in for most of the tools we use.”
8. CyberArk Identity
CyberArk Identity is part of CyberArk’s broader Identity Security Platform. It’s designed to secure access for all types of identities—including workforce users, customers, and particularly privileged users—across various applications and IT environments. CyberArk Identity evaluates real-time context (e.g., location and behavior) to make dynamic access decisions.
Price: By inquiry.
Best for: Legacy identity & privileged access security.
Review: “The CyberArk Identity tool has various capabilities such as managing privileged accounts [and] providing secure access to resources.”
9. JumpCloud Identity Lifecycle Management
JumpCloud Identity Lifecycle Management is offered as part of a broader cloud directory platform designed to unify identity and device management. It provides a single, cloud-based directory to manage all user identities and automates granting and revoking user access to applications.
Price: Offers a free tier for up to 10 users/devices, then tiered pricing based on features and user count.
Best for: SMBs.
Review: “We use it for everything from enforcing security policies on Macs to managing SSO across dozens of SaaS tools.”
10. Oracle IAM

Part of Oracle’s broader enterprise software suite, Oracle IAM offers identity governance, access management, directory services, and security for both on-premises and cloud environments. Another big tick is that it seamlessly integrates with other Oracle databases and cloud services.
Price: By inquiry.
Best for: Oracle-centric enterprises.
Review: “Very easy to add groups, user access, and user control.”
Table 1: How the Solutions Stack Up
| Solution | Key features | Best for | Price |
| Apono | Automates JIT access. Enables on-demand self-serve, granular permissions. Streamlines the cloud access lifecycle. | Best overall for cloud-native & DevOps teams | By inquiry |
| Entra ID | Lifecycle workflows for human users within the MS ecosystem and third-party services. | Integration with the Microsoft ecosystem | Free & paid tiers |
| Ping Identity | Authentication, authorization & identity governance solutions. | Large enterprises & complex hybrid environments | By inquiry |
| OneLogin | Centralizes identity management in a single directory. | User-friendly SSO | Tiered pricing |
| Auth0 | Authentication and authorization within custom applications. | Developers building custom app authentication | Free & paid tiers |
| SailPoint IdentityIQ | Identity governance and administration (IGA), incl. provisioning and deprovisioning. | Comprehensive enterprise identity governance | By inquiry |
| Okta | SSO, MFA & API access management. | SaaS integrations | By inquiry |
| CyberArk Identity | Real-time context analysis. | Converged identity & privileged access security | By inquiry |
| JumpCloud | Automates granting and revoking user access to applications. | SMBs | Free & paid tiers |
| Oracle IAM | Identity governance, access management & directory services. | Oracle-centric enterprises | By inquiry |
Apono: Purpose-Built for Modern Identity Access Challenges
Managing identities, especially non-human ones like service accounts and API keys, has become a real challenge in today’s cloud-native environments. Apono stands out as the top solution for revolutionizing identity management. Apono helps teams define and enforce who can access what, when, and for how long, without slowing down engineering workflows. It’s not just about security anymore; it’s about enabling productivity while staying audit-ready.
Apono empowers secure, efficient operations with configurable break-glass and on-call access flows to remediate production errors faster while providing granular access to required resources. It also deploys in less than 15 minutes, allowing for rapid integration into your existing security stack.
Ready to eliminate standing privileges and automate lifecycle control for every identity? Book a demo with Apono and modernize your identity security strategy.







