Top 10 Privileged Access Management Software Solutions

The Apono Team
September 29, 2025

Identity-related threats are draining time and resources faster than security teams can keep up. The challenge is no longer just about stopping breaches; it’s about keeping up with the scale of alerts and risks.
On average, organizations spend 11 person-hours investigating each identity-related security alert. Meanwhile, credential theft has soared 160% in 2025, making privileged accounts and non-human identities (NHIs) a prime target for attackers.
Modern Privileged Access Management Software Solutions (PAM) offer a way forward by automating access controls and reducing standing privileges, filling the gaps left by traditional approaches and securing your organization.
What are privileged access management software solutions?
Privileged Access Management software secures and controls access to high-value accounts like admin users and NHIs—basically any accounts that hold the keys to critical infrastructure. These solutions enforce the principle of least privilege, ensuring that users and services only get the access they need, for the minimum time required.
PAM software centralizes and automates access workflows, such as vaulting credentials, issuing short-lived tokens, monitoring privileged sessions, and enforcing policies like Just-in-Time (JIT) access. These tools provide many big ticks for security and compliance, such as creating audit trails for frameworks like SOC 2 and GDPR.
The need for PAM solutions is especially critical in today’s cloud environments, where non-human identities outnumber human users by more than 80:1. For example, instead of leaving a cloud service account (an NHI) with standing database or API security permissions, PAM tools can issue time-bound credentials only when that service is actively running a job.
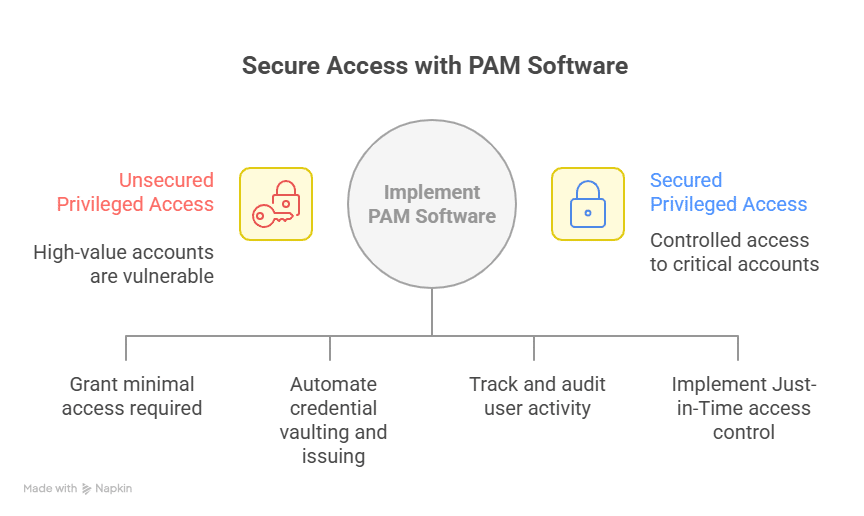
Benefits of Privileged Access Management Software Solutions
Effective PAM platforms deliver more than protection—they streamline access and ensure that even machine-to-machine credentials are properly governed.
- Reduces security risk: Eliminates excessive or standing privileges, protecting against credential theft and identity-based attacks, especially those targeting non-human identities (e.g., API keys and bots).
- Improves visibility into non-human identities: Discovers, monitors, and governs machine-to-machine credentials and Agent2Agent workflows that are often overlooked but frequently exploited.
- Improves efficiency: Automates provisioning and revocation, removing ticket queues and giving developers on-demand and time-bound access via familiar tools like Slack.
- Simplifies compliance: Generates detailed audit logs and automated reports to meet requirements like HIPAA, SOC 2, GDPR, and CCPA. Usually includes governance across critical workloads like data management and storage environments.
- Supports scalability: Manages access consistently across thousands of users, apps, and cloud environments without slowing teams down.
Key Features of Privileged Access Management Software Solutions
To understand why PAM is critical today, let’s look at what these solutions actually do and how they work.
- Just-in-Time (JIT) access: Issues temporary, auto-expiring permissions so users and services only have access when needed.
- Credential vaulting & rotation: Securely stores privileged credentials and automatically rotates them to prevent reuse or compromise.
- Session monitoring & auditing: Records privileged activity for visibility, forensic analysis, and compliance reporting.
- Granular policy enforcement: Applies least-privilege access controls at a fine-grained level—down to databases, APIs, Kubernetes clusters, and environments used for AI code generation and automated builds.
- Machine identity management: Discovers, governs, and secures credentials for service accounts, APIs, and other NHIs across cloud and DevOps environments.
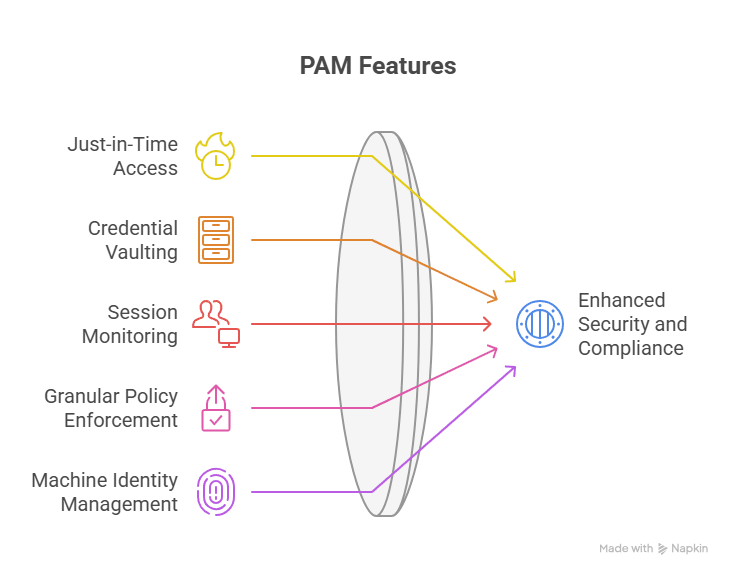
How to Choose the Right Privileged Access Management Software Solution
When comparing PAM tools, it’s important to balance security with usability and scalability. Here are key factors to guide your decision-making.
- Prioritize automation: Look for tools that offer JIT access, automated provisioning, and credential rotation to minimize human error and manual overhead.
- Check integration coverage: Ensure the PAM solution integrates seamlessly with your cloud providers, CI/CD pipelines, and collaboration tools like Slack or Teams. The solution should also scale governance across both human and machine identities.
- Assess compliance support: Verify that the PAM solution provides detailed audit logs, reporting, and policy controls to simplify SOC 2, HIPAA, GDPR, and broader data security compliance.
🔍 Compare PAM Platforms with Confidence
Turn your shortlist into a smart choice. See the capabilities that matter for AI workloads, Zero Standing Privilege, and NHI governance. Download the 2025 Access Platform Buyer’s Guide here
Top 10 Privileged Access Management Software Solutions
1. StrongDM
StrongDM is a zero trust PAM platform that centralizes access across infrastructure, such as servers, databases, Kubernetes, cloud, and SaaS. Its key features include access policies and capturing session data for audits and compliance.
Main Features:
- JIT access and credential automation
- Records SSH, RDP, Kubernetes, and database sessions for auditing
- Utilises a Cedar‑based policy engine for context-aware access control
Price: Starts at $70/user/month.
Review: “Their platform is intuitive and highly secure, which makes it easy for us to recommend to clients across industries.”
2. Apono
Apono is a cloud-native access management solution built to eliminate standing privileges and reduce identity-based risks without slowing developers down. While most PAM solutions still rely on vaults and manual workflows, Apono eliminates these bottlenecks with a cloud-native, Just-in-Time model built for scale. It deploys in less than 15 minutes and integrates with developer-friendly tools like Slack, Microsoft Teams, and CLI, making secure access simple and scalable.
Main Features:
- Granular policy enforcement: Enables fine-grained access down to individual databases, APIs, and cloud resources, with flexible approval workflows.
- Automated JIT access: Issues time-bound, auto-expiring permissions so users and non-human identities (like service accounts and APIs, etc) get access only when needed.
- Break-glass and on-call flows: Pre-configured emergency access workflows ensure teams can remediate incidents quickly.
- Comprehensive audit logs and reporting: Delivers full visibility into who accessed what, when, and why to simplify audits.
- Self-serve access requests: Empowers developers to request and receive access instantly via Slack, Teams, or CLI.
Price: Tailored pricing depending on team size and infrastructure complexity. A free trial is available, and enterprise-grade plans are available upon request.
Review: “Apono’s product does exactly what it claims to […] it saves me time, and provides value to my users by streamlining the process of granting access to our resources in a precise, auditable way.”
3. Heimdal Privileged Access Management
Heimdal Privileged Access Management is a comprehensive PAM module that enables JIT elevation and automatic de-escalation of user rights. It’s embedded within Heimdal’s broader cybersecurity suite.
Main Features:
- Zero‑trust execution and threat‑driven session termination
- Integration with Heimdal’s broader security suite for centralized governance
- Granular access control via role-based permissions
Price: By inquiry.
Review: “While the solution can be complex to implement and manage, the benefits it provides in terms of enhanced security and improved efficiency are worth the investment.”
4. Wallix Bastion

The Wallix Bastion PAM platform integrates password vaulting, session management, and access control, including HTML5 web sessions, with full video and metadata audits.
Main Features:
- Centralized credential management with automatic rotation
- Supports agentless, browser-based access (no VPN/fat client needed)
- Secure machine-to-machine password handling via APIs
Price: User- or resource-based pricing available, starting at around $103/month for 10-50 users.
Review: “The setup process was simple, and the solution can be implemented within less than one day.”
5. ARCON Privileged Access Management
ARCON PAM is an enterprise-grade solution delivering granular control over privileged identities and environments. It supports various features, from adaptive authentication to session monitoring and secrets management.
Main Features:
- Auto-discovers and onboards identities across AD, AWS/Azure/GCP
- Supports SSO, MFA, and microservices-based deployments on-prem or SaaS
- Securely vaults and rotates credentials (including SSH keys)
Price: By inquiry.
Review: “The UI has improved significantly over the past year, making navigation and policy configuration easier.”
6. Segura 360° Privilege Platform

Segura 360° Privilege Platform is an all-in-one PAM suite that spans the entire privileged access lifecycle. It covers password vaulting, DevOps secrets management, session recording, cloud identity governance, and more.
Main Features:
- Fast deployment in as little as seven minutes
- Full privileged access lifecycle coverage
- Grants time-limited permissions with JIT access
Price: All-inclusive licensing model available by inquiry.
Review: “The standout aspects are ease of use, robust security layers (MFA included), and excellent customer support.”
7. ManageEngine Password Manager Pro
This option is often categorized as a Privileged Password Management (PMM) tool rather than a full-featured PAM. Still, ManageEngine offers a centralized, AES-256 encrypted vault for privileged credentials and remote session control. It integrates with Active Directory and CI/CD tools for seamless access governance.
Main Features:
- Provides built-in compliance reports (PCI-DSS, ISO 27001, GDPR)
- Integrates with AD, LDAP, REST APIs, and ticketing platforms
- Records remote sessions (SSH, RDP) for forensic auditing
Price:
- Standard Edition: Starting at $595/year (2 admins)
- Premium Edition: Around $1,395/year
- Enterprise Edition: Approximately $3,995/year
Review: “Manage Engine Password Manager Pro is very user-friendly and easy to manage. [I use the] multi-factor authentication with strong encryption methods.”
8. Systancia

Systancia’s PAM solution adapts its control levels based on the task’s criticality, ranging from standard internal administration to high-risk, highly regulated operations. It delivers additional features like contextual session monitoring and secure credential injection.
Main Features:
- Adaptive control levels by context, from routine tasks to high-security
- Enables automated protective actions to halt suspicious activities
- Offers hardened virtual or terminal-based access
Price: By inquiry
Review: “Systancia Gate and Systancia Cleanroom allow us to implement these accesses very quickly and manage them very simply.”
9. Teleport
Teleport is a cloud-native platform providing PAM through zero trust principles and cryptographic identities. It unifies access across SSH, Kubernetes, databases, web apps, and cloud environments.
Main Features:
- Supports SSH, Kubernetes, databases, Windows desktops, and cloud apps under one policy plane.
- JIT, short-lived credentials
- Enforces least-privilege access controls via identity-based policies
Price: Free trial. Pricing is by inquiry.
Review: “Reviewers highlight centralized access management for SSH, Kubernetes, AWS, and RDS as a standout efficiency.”
10. Netwrix (formerly SecureONE)
Netwrix’s offering is a PAM platform that replaces standing privileges with just-in-time, ephemeral access. It delivers privileged account discovery, time-limited credentials, real-time session monitoring, and secure remote access without requiring VPNs.
Main Features
- Enables task automation (e.g., password resets, patch deployments)
- Deploys in under a day
- Automatically creates, enables, and cleans up privileged accounts on demand
Price: By inquiry
Review: “[Netwrix is] always very responsive and helpful every time we have an issue. The product itself is also very easy to use.”
Why Apono is Built for Modern Enterprises
Identity-based attacks are rising faster than traditional defenses can adapt, and you can’t afford to expose privileged accounts (human or machine). Modern PAM solutions offer an automation lifeline, cutting down investigation time and providing the audit trails needed for compliance.
In a world where machine identities outnumber humans and attackers exploit every overlooked credential, Apono delivers a safer and more scalable way to manage privileged access. Get started with Apono today and see how modern PAM can protect your organization without slowing down your teams.
Unlike legacy PAM platforms that rely on static roles, Apono takes a cloud-native, JIT approach. By automating the issuance and revocation of privileges down to individual databases, APIs, or Kubernetes clusters, Apono eliminates standing access and dramatically reduces attack surfaces. Developers can request access through Slack, Teams, or CLI, while security teams gain full visibility through comprehensive audit logs and compliance-ready reporting.
Want to Compare PAM Platforms Side-by-Side?
Before you choose a solution, see how security leaders evaluate Privileged Access Management platforms built for the AI era. Download the Apono Access Platform Buyer’s Guide to learn what differentiates modern, cloud-native PAM from legacy vault-based tools—and how to choose the right platform for your organization.






