What is Agent2Agent (A2A) Protocol and How to Adopt it?

The Apono Team
October 1, 2025
Imagine autonomous agents negotiating and acting on your behalf—no manual hand-offs, just an efficient, policy‑driven communication. That’s the promise of Google’s Agent2Agent (A2A) Protocol, unveiled at Google Cloud Next in April 2025. Developed with input from over 50 partners, A2A is now open-sourced under the Apache 2.0 license and governed by the Linux Foundation.
But excitement quickly collides with reality. Early adopters report compliance blind spots (who approved that token and when?), latency added by cross-agent orchestration, and the operational overhead of adding another standard into pipelines. As agent-based architectures become the backbone of AI-driven automation, the pressure is mounting on engineering teams to enable secure, autonomous interactions between services.
A 2025 global AI survey reveals that 29% of enterprises are already running agentic AI in production, with another 44% planning to join them within a year. Cost-cutting and reducing manual workloads are among the top goals for adoption. Understanding the Agent2Agent Protocol is vital for building secure and scalable systems that can keep up with the next wave of automation.
What is the Agent2Agent (A2A) Protocol?

Google’s Agent-to-Agent (A2A) Protocol is an open, vendor-neutral language that lets independent AI agents discover each other, negotiate how they will talk (text, files, streams), and work together without exposing their private code or data.
Google unveiled the spec on April 9, 2025, at Cloud Next. It is backed by more than 50 technology partners and is now maintained as an open-source project under the Apache 2.0 license.
Google kicked the A2A project off after running large, multi-agent systems for customers and seeing the same pain points repeat:
- Brittle one-off integrations.
- Security gaps.
- No common way for agents from different vendors to “shake hands.”
How does the Agent2Agent Protocol work?
The four-step flow below illustrates the full A2A handshake from discovery to streaming task updates.

1. Discovery with an Agent Card
Every agent publishes a tiny JSON file, /.well-known/agent.json, listing its name, endpoint, skills, and supported auth flows. A client agent simply fetches this card (directly or via a registry) to see who can do what and how to connect.
2. Auth in Micro-slices
The card also tells the caller which OAuth 2/OIDC method to use. The client obtains a short-lived token (minutes), allowing access to be scoped and automatically expires. This step eliminates hardcoded secrets, marking a shift from static secrets to dynamic machine identity management, where each agent authenticates based on policy, context, and lifespan.
3. Task Exchange Over Web Standards
With a token in hand, the client sends a task/send or task/sendSubscribe request via JSON-RPC 2.0 over HTTPS.
- Synchronous work:task/send returns the answer right away.
- Long-running work:task/sendSubscribe opens a Server-Sent Events (SSE) stream so the remote agent can push status and partial results. Tasks move through states (submitted → working → completed) and can include messages or artifacts (files, JSON blobs, images).
4. Built-in Observability
Each request/response carries trace IDs, and agents emit structured logs and metrics in OpenTelemetry Protocol (OTLP) format. You can drop A2A traffic straight into existing dashboards without bolting on a separate telemetry layer. This level of observability is essential for identifying anomalies and containing the risks of non-human identities operating in complex, distributed environments.
Many teams adopting A2A have struggled with blind spots, like losing track of which agents initiated sensitive operations or where tokens are reused across flows. Without built-in tracing and structured logs, auditing multi-agent systems becomes a fragmented, manual task. A2A’s observability layer helps reduce that operational burden, but it still requires thoughtful integration with existing security tooling.

What is the Agent2Agent Protocol designed to do?
At its core, A2A gives every software agent a common language and contract so they can:
- Discover one another without manual registry updates.
- Exchange tasks securely with scoped tokens and auditable IDs.
- Stream real-time results (via SSE) from remote agents for both quick jobs and long-running workflows.
By replacing brittle webhooks and custom RPC layers with an open JSON-RPC spec, the Agent2Agent Protocol eliminates glue code and reduces integration overhead across ecosystems.
Because discovery, auth, transport, and telemetry are part of the spec, you don’t waste cycles reinventing service discovery, API gateways, or audit pipelines. You wire agents together (much like microservices), then layer governance tools on top to enforce least-privilege, time-boxed access across your infra. It reduces repetitive integration tasks, which improves developer productivity across teams working in complex environments.
Why is the Agent2Agent Protocol a good thing?
The Agent2Agent Protocol solves real pain points in DevOps and automation by making agent communication smarter and safer. Here’s why it’ll be beneficial in the long run.
Plug-and-Play Interoperability
Any AI agent that speaks A2A can call, or be called by, any other agent.
Example: If a vulnerability scanner agent discovers a patch management agent during a CI run, it can send a task with the CVE list and stream the fix status back to the build.
Built-in Security
Short-lived OAuth/OIDC tokens and signed task IDs keep access scoped and auditable without requiring the hardcoding of secrets.
Example: When a monitoring bot detects a spike, it requests a one-off token to spin up extra pods. The token expires automatically once scaling is complete, aligning with enterprise identity management best practices.
Less Glue Code, Faster Pipelines
The Agent2Agent Protocol includes built-in support for agent discovery, JSON-RPC 2.0 transport, and SSE streaming. Teams can focus on features instead of writing adapters and polling loops.
Example: A scheduler agent queries rightsizing agents in AWS, GCP, and Azure, aggregates savings, and opens a single cost-cutting PR. No polling scripts are required.
Enterprise-Grade Observability
Every request carries trace IDs and standard OTLP metrics, which are dropped straight into Grafana/Prometheus dashboards, regardless of whether those agents are operating in the cloud, across edge services, or in traditional data centers.
Example: A chatbot passes a billing request to a payment agent via A2A; the handoff is fully logged, and the one-time token expires as soon as the charge is completed.
Agent2Agent Protocol Design Principles
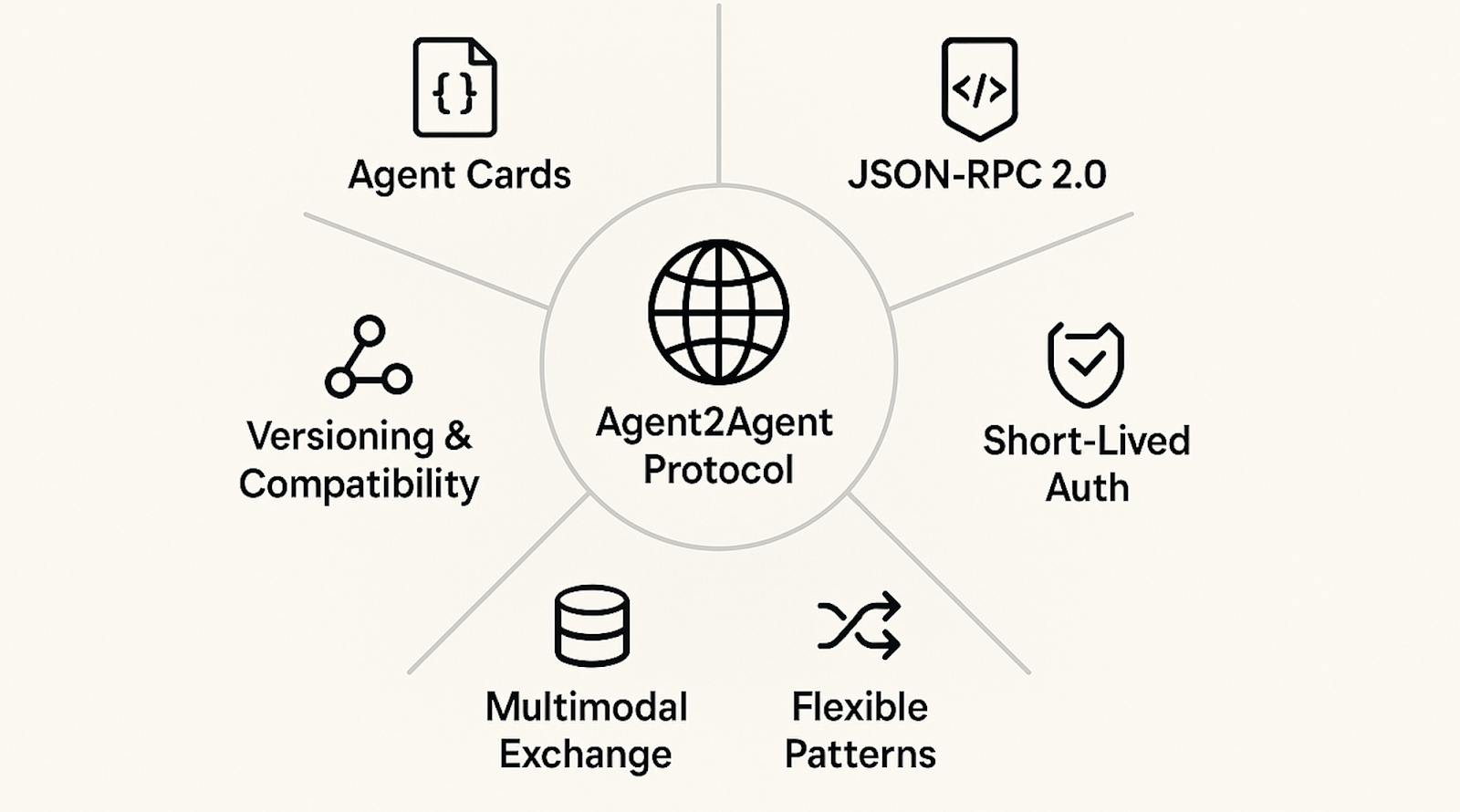
These guiding principles explain why A2A stays flexible, secure, and developer-friendly as the ecosystem expands.
- Agent Cards for zero-config discovery: Every agent publishes a small JSON file at /.well-known/agent.json that lists its endpoint, skills, and auth method.
- Standard JSON-RPC 2.0 over HTTPS: Requests (tasks/send) and responses travel as JSON-RPC messages on plain HTTPS, so agents in any language interoperate through existing API gateways or mTLS proxies.
- Built-in auth with short-lived tokens: Tokens scoped per task and expiring in minutes eliminate long-lived secrets while integrating with enterprise SSO, a key cybersecurity best practice for identity-aware systems and zero trust architectures.
- Flexible interaction patterns: Uses a blocking call for quick answers and tasks/sendSubscribe for long tasks. Gives real-time updates via Server-Sent Events (SSE). Agents can even push webhooks for fully async workflows.
- Rich, multimodal data exchange: A single task can bundle text, JSON, files, images, or audio as separate “parts,” allowing agents pass artifacts logs, screenshots, CSVs without inventing new MIME schemes.
- Versioning & vendor-neutral extensibility: The spec includes a compatibility flag so new features roll out without breaking older agents. The A2A Apache-2.0 license prevents any one vendor from locking the rest out. On July 31, 2025, A2A version 0.3 was released—adding gRPC support, signed security cards, and extended Python SDK support; the protocol now counts over 150 supported organizations.
How to Adopt the Agent-to-Agent (A2A) Protocol in 6 Practical Steps
Follow this step-by-step guide to adopt your first A2A agents and weave them safely into your workflow.
Step 1: Install the Sample Toolkit
Clone Google’s reference repo and drop it into the Python SDK.
git clone https://github.com/a2aproject/a2a-samples.git
cd a2a-samples
python -m venv .venv && source .venv/bin/activate
pip install a2a-python # or a2a-js for NodeThe repo includes basic example agents and lightweight helper code for JSON-RPC calls and SSE streaming, but production implementations will need hardening.
Step 2: Launch a Demo Agent
Pick one of the ready-made agents (e.g., the “currency” FastAPI service) and run it.
uvicorn samples.python.currency_agent:app --port 10000 --reloadWhen the server starts, it auto-serves an Agent Card at: https://localhost:10000/.well-known/agent.json, advertising its skills and auth method.
Step 3: Expose the Agent Card
Make that JSON file reachable via a public URL, an internal LB, or a registry entry. Other agents can pull it and learn who you are and how to talk. No extra service-discovery layer is required. For production environments, agents can also publish to a centralized A2A registry, which supports indexed search and simplifies discovery across large infrastructures.
Step 4: Hook in Short-Lived Auth
Edit the auth block in the Agent Card to point at your OIDC or token issuer and set the TTL to minutes. Every task call will now carry a scoped, self-expiring token instead of a long-lived secret.
Step 5: Send a Task and Stream the Result
From another agent (or just curl), invoke the first agent:
TOKEN=$(<your_token_here> --ttl 5m --aud currency-agent)
curl -H "Authorization: Bearer $TOKEN" \
-X POST https://currency-agent:10000/tasks/sendSubscribe \
-d '{"input":{"amount":"50","from":"USD","to":"JPY"}}'The request uses JSON-RPC 2.0 over HTTPS; the sendSubscribe variant opens a Server-Sent Events stream, so you get live status until completed.
Step 6: Watch the Traces
The SDK emits OTLP logs/metrics with a shared trace ID. Point OTLP logs and metrics to your backend of choice for unified observability.
Security Automation for Safe A2A Implementation
The Agent-to-Agent (A2A) Protocol enables software agents to trade tasks and data on the fly, but it truly shines when access is tightly controlled and fully auditable. Apono and the A2A Protocol share a key mission: enabling secure, policy-driven access between non-human identities (NHIs) like service accounts, bots, and APIs. Apono ensures that, even as NHIs interoperate across boundaries, their access is ephemeral, precisely scoped, and compliant.
Apono’s platform is purpose-built to manage access for NHIs by enforcing Just-In-Time (JIT) and Just-Enough-Privilege (JEP) access, thereby reducing standing privileges and misconfigurations. It ensures every service account, bot, or API key gets only the access it needs for exactly as long as it’s needed.
Apono is designed to become the enforcer of orchestrated permissions across infrastructure by automating and right-sizing the lifecycle of access for NHIs—including provisioning, expiration, and auditability—to install least privilege for NHIs and bring zero trust to all of your identities.
With Apono’s auto-expiring tokens and centralized logs, you can narrow the window for misuse and provide security teams with a single source of truth when compliance and auditing questions arise.
Get hands-on with Apono. Request a demo to deploy in under 15 minutes and start eliminating overprivileged access.