What is Just Enough Privilege? Definition, Examples, and Best Practices

The Apono Team
November 27, 2025

Every automated workflow, microservice, and CI/CD integration needs credentials to run, but those credentials often live far longer and reach far wider than anyone intends. The result is a growing attack surface hidden in plain sight.
Concerningly, 26% of organizations believe more than half of their service accounts are over-privileged. This is a staggering figure when you consider that machine identities now vastly outnumber human users by 80:1.
Engineers need fast access to deploy, debug, and deliver, yet static or “always-on” permissions keep the door open long after the job’s done. And it’s not just people—non-human identities (NHIs) quietly expand the attack surface when left unchecked.
That tension between agility and control is where the idea of Just Enough Privilege (JEP) comes in. JEP is the practical evolution of least privilege: giving users and NHIs only the exact permissions they need, for the time they need them.
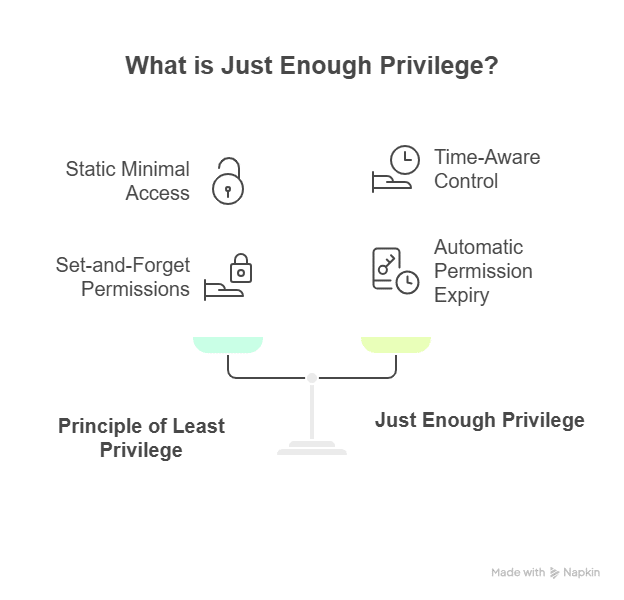
What is Just Enough Privilege?
Just Enough Privilege (JEP) grants users or systems the exact access they need to perform a specific task, and only for the duration that access is required. Once the task is complete, permissions automatically expire, whether that task is triggered by a developer or an automation bot. This approach keeps exposure short-lived and contained, limiting how much damage a compromised human or machine identity can cause, while eliminating standing access.
Where the principle of least privilege (PoLP) focuses on static, minimal access, JEP adds time awareness to that control. It avoids the trap of “set-and-forget” permissions that accumulate over time. While JIT access ensures temporary access at the right time, it doesn’t always guarantee the minimum scope unless paired with least-privilege policies. JEP unites both, enforcing the right level of access for the right time and scope.
Why Just Enough Privilege Matters
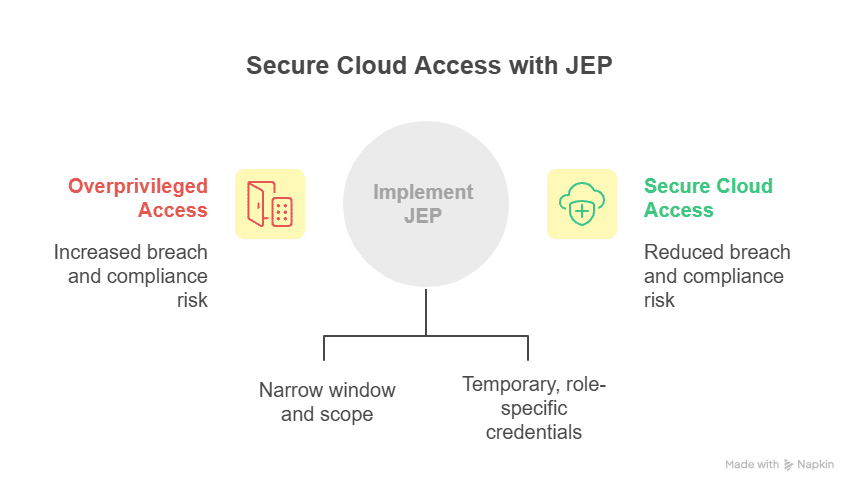
Overprivileged access is one of the easiest ways to increase breach likelihood and compliance exposure, a challenge that cloud PAM solutions are specifically designed to solve. In many security incidents, compromised credentials, not software flaws, were the primary entry point. Excess permissions give attackers room to escalate privileges and linger unnoticed.
The problem has grown with the rise of identity-based attacks. Phishing campaigns, token theft, and shadow admin roles exploit the growing complexity of access controls. In cloud environments, non-human identities (NHIs) such as service accounts, workloads, and automation tools now outnumber human users by almost 80 to 1, creating a new class of unmanaged risk. Each of these identities can authenticate or modify configurations, often with privileges far beyond what’s required.
JEP addresses these challenges by narrowing the window and scope of access. When privileges are both minimal and time-bound, lateral movement within systems becomes harder, and insider misuse is limited. Temporary, role-specific credentials ensure engineers can deploy and troubleshoot without leaving long-lived permissions behind.
While frameworks such as NIST SP 800-53, ISO 27001, and SOC 2 don’t explicitly define ‘Just Enough Privilege,’ they require enforcement of least privilege and controlled access; principles that JEP operationalizes in practice.
Examples of Just Enough Privilege in Action
Just Enough Privilege works best when applied to everyday workflows, not just theoretical policies. The goal is to make access feel more natural for engineers, keeping risk exposure as minute and short-lived as possible. A few scenarios where JEP delivers that balance:
Temporary Read-Only Access for DevOps Engineering
Picture a DevOps engineer investigating a production issue in AWS; logs aren’t updating, and the team suspects a problem in an AWS S3 bucket. The team needs to trace what’s missing and confirm the source of a failed deployment to get the service back online. Instead of granting broad or standing access to the bucket, the engineer requests a temporary, read-only session through a cloud-native access management platform like Apono. Now, they can review objects, verify log flow, and confirm the fix without touching or modifying data.
Once the time window expires, that access quietly expires on its own. The engineer must re-request access if further review is needed, creating a natural audit trail and ensuring access doesn’t persist longer than required. It’s the same agility engineers expect, but with zero-trust discipline built in by design.
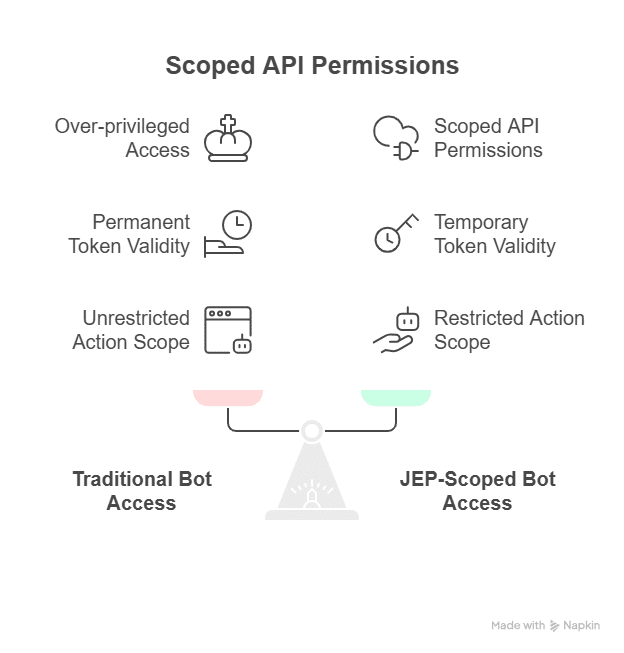
Scoped API Permissions for a Deployment Bot
The biggest NHI risks often come from automation itself. Bots and service accounts rarely request less access; rather, they just inherit whatever’s easiest to configure. JEP helps right-size that by enforcing temporary, scoped credentials for every task.
A CI/CD deployment bot is responsible for updating Kubernetes configurations during a release. Traditionally, such bots are over-privileged with full cluster or repository access to avoid friction in the build process. With JEP, you can define scoped API permissions that limit the bot’s actions and where they can be used.
In this setup, the bot gets a token tied to one pipeline instance, which is valid for the duration of that deployment run. It can update specific YAML configurations or apply manifests, but can’t read secrets or access unrelated namespaces. Once the job is completed, automation will immediately revoke the token.
Limited Credentials for a CI/CD Pipeline Build Job
Pipelines are another common blind spot. These non-human actors perform critical steps in delivery but often use static secrets that live in plain text or config files.
Consider a build job that compiles code, runs tests, and pushes container images to a private registry, a core component of most CI/CD best practices. Normally, that step depends on long-lived credentials buried in an environment variable somewhere.
With JEP, the pipeline gets a short-lived token created just for that job. It does exactly what’s needed (authenticating and pushing a single image) and disappears the moment the build wraps up.
This approach removes the need for static credentials stored in environment variables or config files, common targets for supply chain attackers. It simplifies compliance reporting, since ephemeral credentials can be tied to defined owners, scopes, and expiry events within your audit logs. The result is a tighter control loop that protects the pipeline without slowing continuous delivery.
Scoped API Access for a Kubernetes Automation Bot
A Kubernetes automation bot might be used to apply configuration updates or manage secrets during runtime. Instead of giving it cluster-wide admin privileges, JEP enforces namespace-level access with an expiry that matches the deployment window.
During a deployment, the bot’s token allows write operations only within a specific namespace and only for the resources defined in the manifest. Once the update completes, automation systems revoke the token. Even if an attacker intercepts that token (a common vector in man-in-the-middle attacks), its scope and validity are too narrow to exploit.
Beyond reducing the attack surface, this approach brings operational transparency. Security teams can trace every privilege grant and expiry event, while DevOps teams maintain seamless automation.
5 Best Practices for Implementing Just Enough Privilege
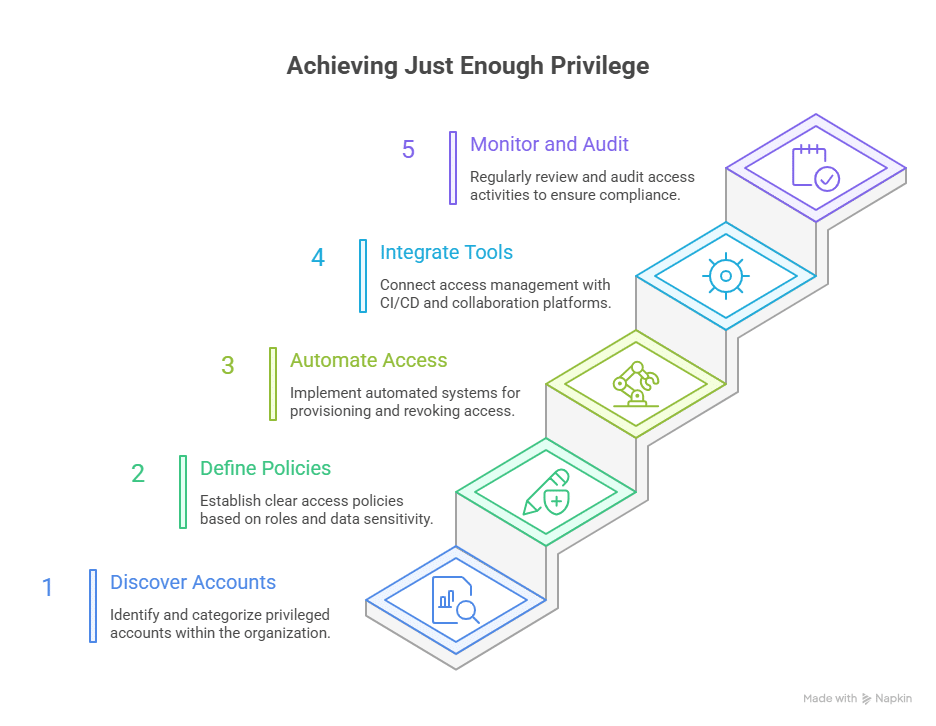
Applying Just Enough Privilege requires a structured and continuous approach. It’s not just about limiting access but doing it intelligently so that productivity isn’t lost in the process. Below are five practical ways to embed JEP into your environment.
1. Discover and Classify Privileged Accounts
Start by identifying all identities within your environment, both human and non-human, to control NHI privilege sprawl. You can’t secure what you don’t know. Map out service accounts, CI/CD tokens, API keys, and user credentials across systems and cloud providers. Classify each by its access level and business function, which helps expose hidden or orphaned accounts that often carry outdated permissions.
2. Define Access Policies by Role and Sensitivity
Once you know what exists, define who needs access to what, when, and why. Build access policies that align with least privilege principles but include time-based controls. For example, a database administrator might need elevated access only during maintenance windows, while an automation script may need it for a single job. Document these patterns clearly to maintain consistency and accountability across teams.
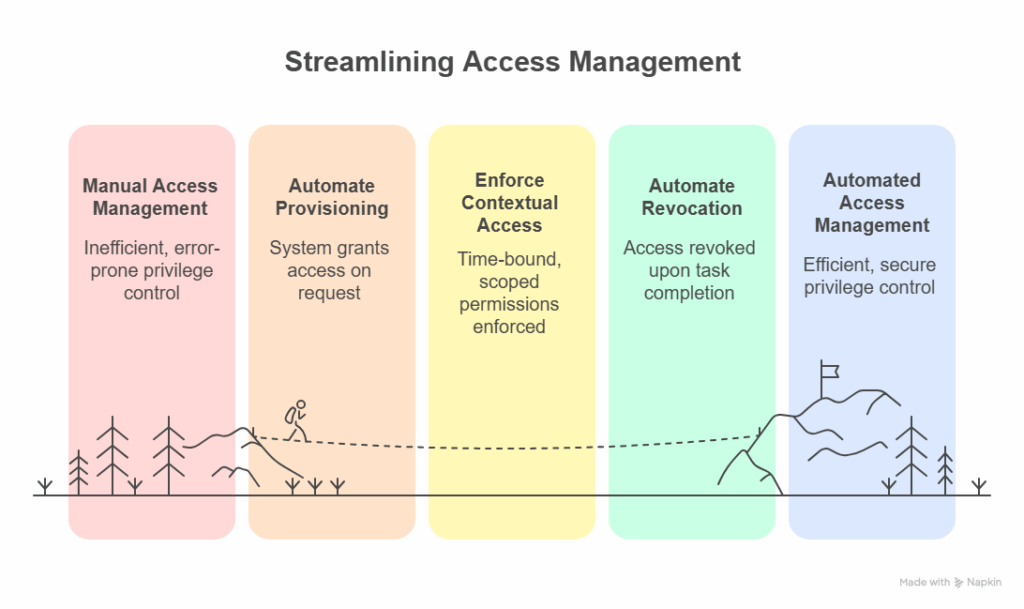
3. Automate Access Provisioning and Revocation
Manual access management rarely scales. Automating how privileges are granted and revoked ensures JEP works as intended. This kind of automation also reduces friction across engineering and project management workflows, freeing teams from manual approval loops while keeping permissions tightly controlled. Cloud-native access management platforms like Apono can enforce contextual, time-bound, and scoped access without constant admin involvement. When engineers request permissions, the system should automatically provision the right level of access and revoke it once the task is complete. This approach reduces friction and removes the human error often tied to privilege sprawl.
4. Integrate with CI/CD and Collaboration Tools
The best JEP systems blend into how your teams already work. Integrate privilege workflows into your CI/CD pipelines, Slack, or Teams channels. Now, engineers can request and approve access within familiar environments or directly through the CLI. Adopting becomes natural rather than forced when identity and access governance are built into daily workflows.
5. Monitor and Audit Regularly
Implement continuous monitoring to track how privileges are used, when they’re requested, and whether they’re still justified. Use logs and audit trails to detect factors like anomalies or privilege drift. Reviewing this data regularly helps refine access policies and align with compliance requirements such as SOC 2 and NIST SP 800-53.
Balancing Agility and Security with Apono
Every organization walks a fine line between agility and control. Engineers need fast access to deploy and deliver without waiting for approvals. Yet those same permissions, if left standing, quietly widen the attack surface. A single overprivileged account or forgotten service token can undo months of good security practice.
Apono helps teams enforce Just Enough Privilege (JEP) by automating how access is requested, approved, and revoked. With Apono, you can grant the right access to the right entity for as long as needed, without slowing down engineering workflows. Apono ensures security becomes invisible to the developer, but powerful enough to protect the entire organization. Deploy Apono in under 15 minutes and integrate it seamlessly with your cloud and CI/CD stack, then you’re ready to eliminate standing access and enforce least privilege at scale.
Get a demo to see how Apono helps you prove compliance effortlessly while keeping least-privilege access fully automated.







