Just-in-Time Access
Replace standing privileges with temporary access that automatically expires. Engineers request access through Slack, Teams, MCPs, or CLI and get approved in seconds, not hours.
Learn more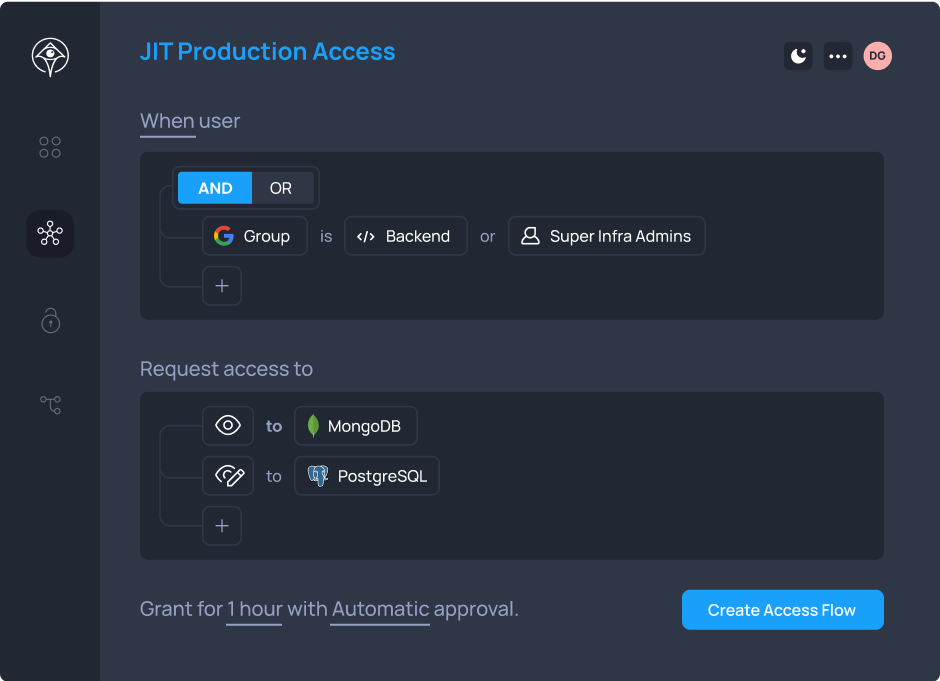
Apono replaces standing permissions with Just-in-Time and Just-Enough access for humans, service accounts and AI agents. Permissions are time-bound, least-privilege, and fully audited.
The result: effortless elimination of 96% of excessive privileges.
Trusted by Security, IAM and DevOps
The Standing Privilege Problem
Engineers burn hours waiting for access
Delays can stretch into hours or days, slowing delivery and extending MTTR by over 50%.
Admins spend their time on manual fixes instead of strategic work
Time is wasted with admins caught in endless role maintenance, ticket queues, and audit remediation.
Most standing access is excessive
Up to 96% of privileges are excessive, dramatically expanding the attack surface and blast radius.
Solution
Stop managing permissions and access decisions manually. Start orchestrating them dynamically. Apono discovers every permission across your cloud, eliminates unnecessary access, and provisions just-in-time privileges through the tools your team already uses.
Map standing privileges, unused permissions, and shadow access across AWS, Azure, GCP, and 200+ services.
Grant temporary, risk-based access that auto-expires. Dynamic policies adapt to business and risk context without manual intervention.
Get actionable insights to eliminate standing privileges, right-size permissions, and accelerate engineering velocity with data-driven recommendations.
How it works
Platform pages
Zero Standing Privileges
Just-in-Time Access
Just-Enough Access
Break Glass Incident Response
Ensure Compliance
Secure DB Access
Cloud Privileged Access
Cloud Access Governance
Replace standing privileges with temporary access that automatically expires. Engineers request access through Slack, Teams, MCPs, or CLI and get approved in seconds, not hours.
Learn more
Enforce access policies throughout your cloud resources. Prevent unauthorized access with automated, risk-based provisioning while enhancing engineering productivity.
Learn moreGain unified visibility and control across AWS, Azure, GCP, and 200+ services. Manage who accesses what, when, and how while maintaining compliance and developer velocity.
Learn more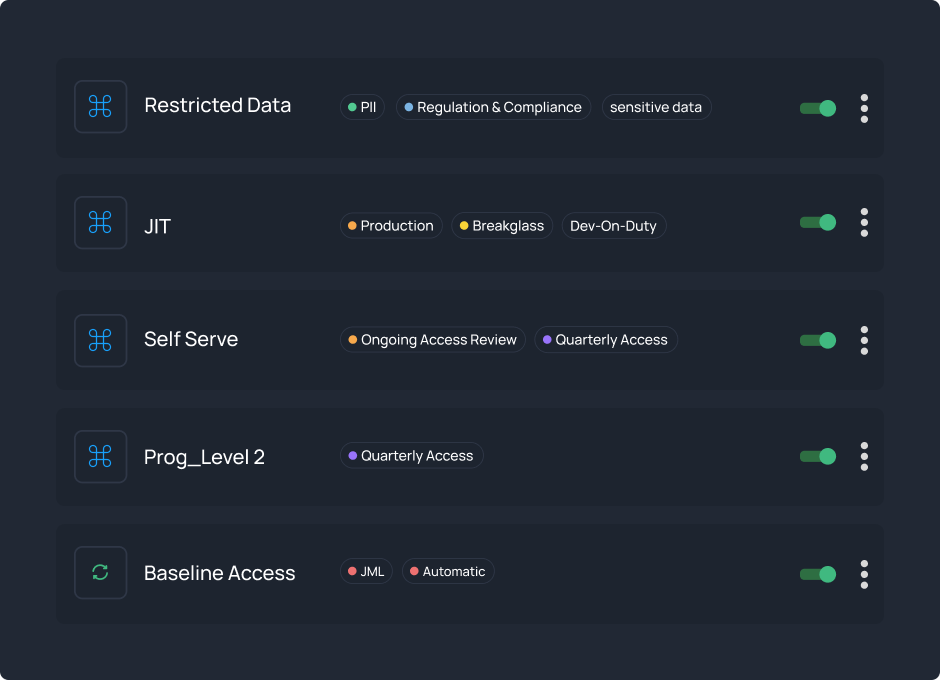
Enable emergency access for critical incidents without compromising on security policies. On-call responders get immediate access to production systems while maintaining complete audit trails.
Learn more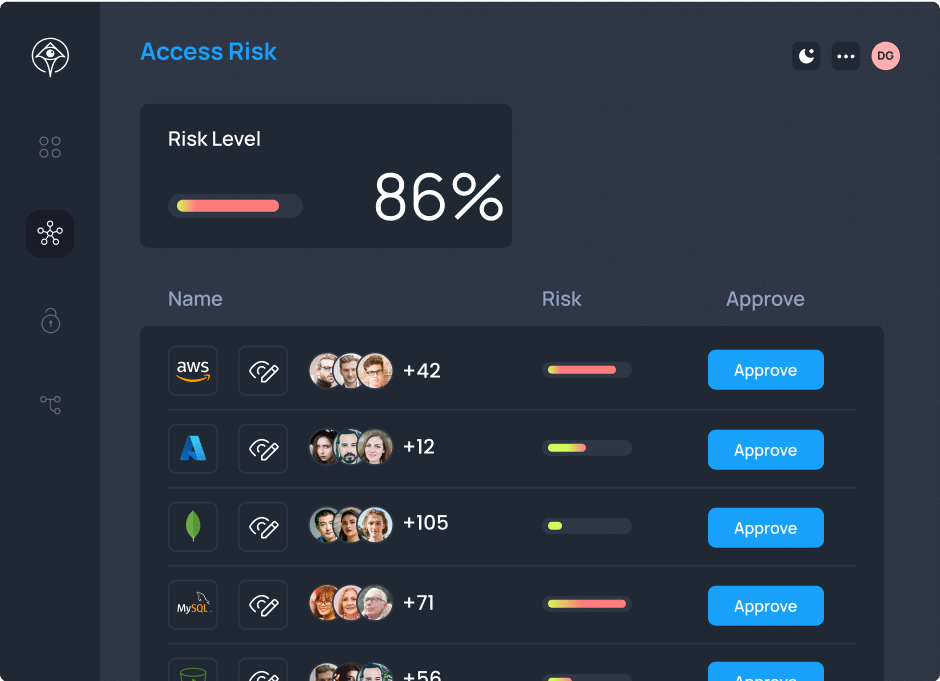
Automate access reviews and generate audit-ready reports for SOC 2, ISO 27001, and HIPAA. Maintain detailed logs of every access request across your environments.
Learn moreCentralize and automate permissions across MySQL, PostgreSQL, MongoDB, and all your databases. Grant granular, time-bound access that keeps sensitive data secure.
Learn more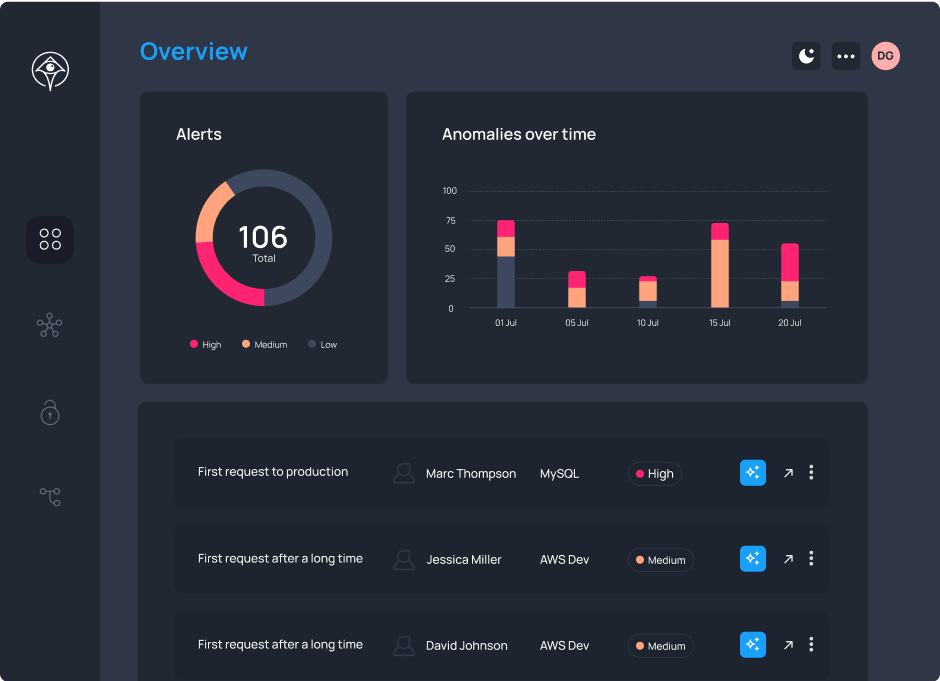
Detect anomalous access request patterns and terminate suspicious sessions in real-time. Stop lateral movement and prevent breaches with AI-powered threat detection and instant response.
Learn more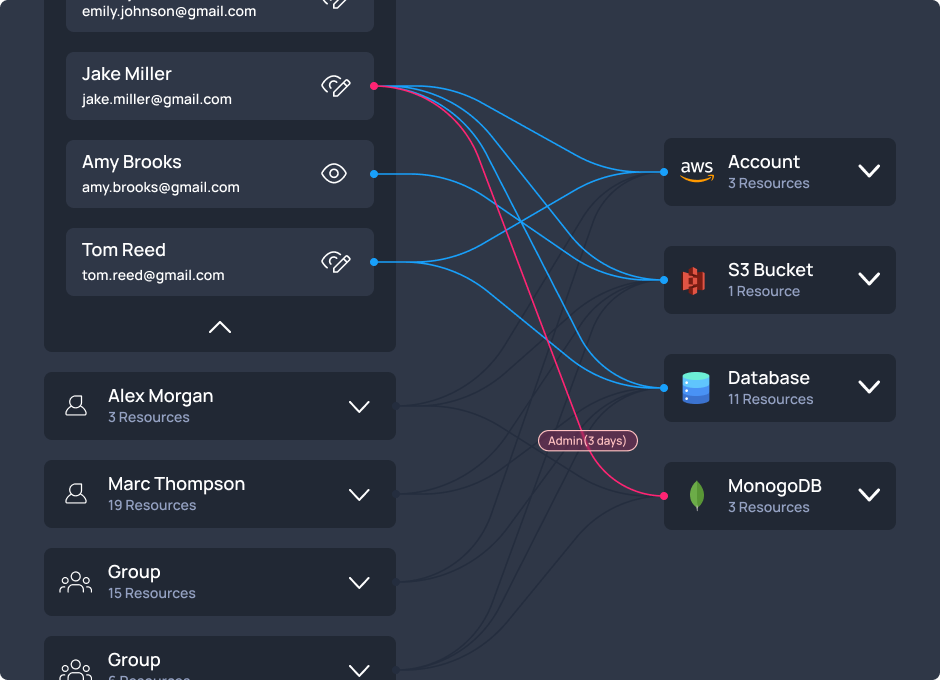
Cut 96% of excessive permissions by eliminating always-on access. Transform static privileges into dynamic, context-based permissions that adapt to risk and need.
Learn moreConnect Apono to your existing stack in minutes. We speak the native API of every platform—no middleware, no maintenance.
Integration Catalog

Apono vs Others
Stop managing permissions. Start orchestrating them. Apono discovers every permission across your cloud, eliminates unnecessary access, and provisions just-in-time privileges through the tools your team already uses.
Capability |
 |
Legacy PAM |
Manual Process |
|---|---|---|---|
| Coverage in one product | Yes (200+ integrations)
Single platform covering AWS, Azure, GCP, Kubernetes, databases, and 200+ dev tools. No need for separate modules or add-ons. |
Limited (fragmented modules) | No |
| Granularity model | Yes (resource-level)
Grant access to specific S3 buckets, database tables, or K8s namespaces. Task-aware policies that understand context. |
Limited (role-level only) | No |
| Dynamic vs. pre-created roles | Yes (ephemeral, auto-expire)
Creates temporary roles on-demand that automatically expire after 1-8 hours. No pre-staging or cleanup needed. |
No (static roles) | No |
| Rightsizing with context | Yes (AI-powered)
AI analyzes usage patterns and risk scores to continuously recommend right-sized permissions. Built into the same platform. |
Limited (needs 3rd party) | No |
| Developer workflow & AI | Yes (natural language)
Request access via Slack, Teams, CLI, or IDE plugins. Use natural language like 'I need read access to production database.' |
Limited (portal only) | No |
| Deployment model | Yes (cloud-native)
API-first architecture. Deploy in minutes with Terraform or CloudFormation. No proxies, agents, or bastion hosts required. |
Limited (proxy-heavy) | No |
| Audit & Compliance visibility | Yes (centralized)
Complete audit trail of every request, approval, and action. One-click reports for SOC 2, HIPAA, GDPR compliance. |
Limited (fragmented) | No |
| Admin overhead reduction | Yes (>95% reduction)
Reduce access management from 40+ hours/month to under 2 hours. Eliminate ticket queues and manual provisioning. |
Limited | No |
| Fast provisioning | Yes (3-5 seconds)
Automated approval based on risk policies. P50: 3 seconds, P99: 15 seconds. Break-glass emergency access: instant. |
Limited (4-8 hours) | No (48-72 hours) |
| Risk reduction | Yes (96% fewer privileges)
Average customer reduces standing admin accounts from 847 to 51. 94% smaller blast radius. Zero standing privileges achieved. |
Limited | No (48-72 hours) |
Just-in-Time (JIT) and Just-Enough Privilege (JEP) replace standing access with short, least-privilege grants for people, service accounts, and AI agents.
Apono typically eliminates 96% of excessive standing privileges across cloud environments.
Most teams achieve initial deployment within 2 hours and full rollout within 2 weeks.
Yes – Apono uses a patented architecture where we never access your data or store secrets.
Apono provides unified governance for both human and machine identities at scale.
Yes. Through the Apono Assist MCP Server, an agent can request access from within its IDE or chat client. Your policies control scope, duration, and approvals. The agent never sees credentials. It gets commands or secure portal links, and everything is logged for audit.