7 Man-in-the-Middle (MitM) Attacks to Look Out For

The Apono Team
September 30, 2025

Today’s man-in-the-middle (MitM) attacks go far beyond coffee-shop Wi-Fi: they target browsers, APIs, device enrollments, and DNS infrastructure. Using automated proxykits and supply-chain flaws, attackers hijack session cookies, tokens, and device credentials—turning one interception into persistent, high-value access.
Concerningly, these are not edge cases. Automated cyber threat activity surged 16.7%, with over 1.7 billion stolen credentials circulating on the dark web—fueling a 42% increase in credential-based targeted attacks. Passwords and simple MFA fail unless access is limited and continually verified.
Security teams can implement best practices, such as cutting token lifetimes and just-in-time elevation, to protect against man-in-the-middle attacks. Let’s review a comprehensive list of security controls you can implement immediately to make intercepted credentials worthless to attackers.
What are man-in-the-middle (MitM) attacks?
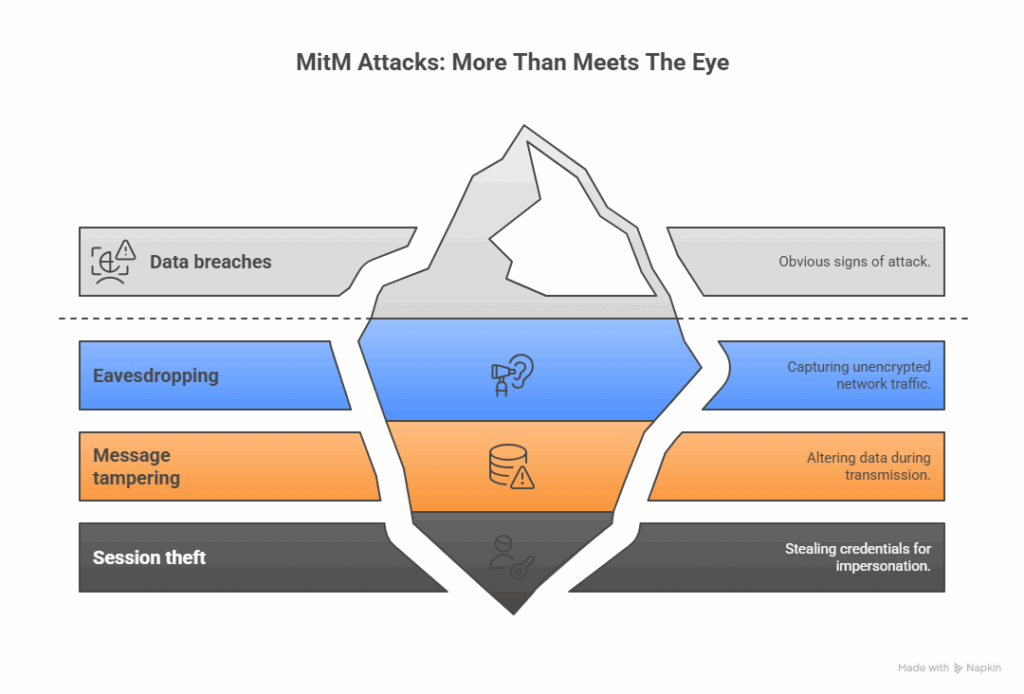
A man-in-the-middle (MitM) attack happens when an attacker secretly intercepts and manipulates communications between two parties. The attacker is positioned in the “middle” of the data exchange, between a user and an app, or between two users or two apps, without anyone noticing. With MitM attacks, the adversary can eavesdrop, steal credentials, alter data, or impersonate one of the parties involved.
Today’s MitM attacks target API calls, machine-to-machine traffic, and even naive agent-to-agent protocols in distributed, cloud-native environments. With stolen tokens or cookies, an attacker gains the same level of visibility and control as a legitimate service account.
Some examples of MitM techniques include:
- Eavesdropping/sniffing: Capturing unencrypted traffic (credentials, config).
- Message tampering: Altering data in transit (API responses, payloads).
- Session & credential theft: Stealing cookies, tokens, or certs to impersonate users/services.
A successful man-in-the-middle adversary gains the same level of visibility and control as the legitimate user or service. Non-human identities (NHIs)—like service accounts, workloads, and agents—are particularly vulnerable. In fact, machine identities now outnumber human identities by as much as 80:1, multiplying the blast radius of a single interception. Without a strong enterprise identity management strategy, these identities are often left overprivileged and unmonitored, creating an easy path for MitM attackers.
7 Man in the Middle (MitM) Attacks to Look Out For, Plus Security Best Practices
MitM attacks aren’t just theoretical risks; they can be the cause behind real breaches or even large-scale espionage campaigns. Let’s review the most relevant attack types that DevOps and engineering need to watch out for.
1. Classic HTTPS Spoofing and SSL Stripping
Attackers downgrade HTTPS connections to plain HTTP, eliminating the security layer of SSL/TLS. This attack vector leaves communication in plaintext, including login credentials, API keys, and session tokens. Misconfigured certificates, outdated systems, or user dismissal of browser warnings leave room for SSL stripping. DevOps teams are especially concerned about this in CI/CD pipelines and API endpoints, as a single misconfigured connection can become the entry point of a MitM attacker.
Example: The 2015 Superfish adware fiasco showed how software that installed its own root certificate could intercept HTTPS traffic by trusting a single private key. Because those certificates shared a key, anyone with the key could impersonate sites (including banks) without browser warnings.
Security best practices:
- Enforce TLS 1.3 across all applications and services.
- Use HTTP Strict Transport Security (HSTS) to prevent downgrade attempts.
- Automate certificate renewal and rotation to reduce the risk of expired or misconfigured certificates.
- Build a structured validation plan to ensure TLS configurations and certificate management are consistently tested across environments.
2. DNS Spoofing (Cache Poisoning)
DNS hijacks and registrar compromises let attackers redirect entire domains to malicious infrastructure.
Example: Sea Turtle was a sophisticated espionage operation uncovered in 2019. Attackers targeted domain registrars, registries, and other DNS infrastructure to compromise DNS records and surreptitiously redirect traffic for targeted organizations to attacker-controlled servers. It allowed the attacker to intercept web and email traffic, steal credentials, and even serve forged or fraudulently issued TLS certificates to avoid immediate detection.
Security best practices:
- Enforce DNSSEC and monitor DNS records via passive-DNS feeds (alert on unexpected delegations).
- Lock registrar accounts with MFA and role separation; require multi-person approval for DNS changes.
- Use certificate transparency and automated cert monitoring to detect fraudulent issuance quickly.
- Use a cloud-native access management platform that limits what compromised DNS traffic can expose, since JIT access makes sensitive tokens and API keys time-bound.
So, what would these best practices look like in practice? Let’s look at an example. Caris Life Sciences used Apono to enforce JIT folder-level permissions in AWS S3—so even if DNS traffic were redirected, attackers couldn’t leverage long-lived standing credentials.
3. ARP Spoofing in Internal Networks (LAN-level MitM)
Attackers poison ARP tables on local networks to force traffic to flow through a malicious host, enabling sniffing and tampering with internal traffic.
Example: Pentest and tool writeups repeatedly show that cheap implants (like Wi-Fi Pineapple and Raspberry Pi) enable LAN ARP attacks. Effective data center management, such as strict network segmentation, helps reduce exposure to LAN-level MitM attacks.
Security best practices:
- Segment east-west traffic using VLANs and microsegmentation.
- Deploy IDS/IPS rules for ARP anomalies and enable switch port security (sticky MACs, BPDU guard).
- Encrypt internal service traffic (mTLS) so LAN sniffing yields little usable data.
- Microsegmentation plus JIT permissions ensures that even if lateral movement is attempted, overprivileged standing access isn’t available.

4. Wi-Fi Eavesdropping & Rogue Access Points (Evil-Twin attacks)
Threat actors use evil twin or malicious hotspots to steal users and proxy or intercept their traffic. This type of attack happens frequently in airports, public charging points, cafes, and hotels.
Example: In July 2024, Australian police arrested an individual for operating an “evil twin” hotspot that harvested travellers’ credentials by redirecting victims to spoofed login pages.
Security best practices:
- Enforce VPN and device posture scans on all non-trusted networks; disable auto-join for enterprise devices.
- Educate staff to verify SSIDs and employ certificate-pinned applications on high-value services.
- Enforce 802.1X/enterprise Wi-Fi with device certificates and scan for duplicate SSIDs on the network.
- Integrate network posture scanning with JIT access to sensitive assets so access from high-risk networks is denied or further challenged.
5. Session Hijacking/Token Replay (Stolen Cookies & API Keys)
Attackers replay stolen session cookies, tokens, or API keys to impersonate services or users, often without passwords. Stolen cookies and tokens don’t just result from MitM attacks; client-side flaws like cross-site scripting (XSS) can also expose session data and API keys, as seen in CVE-2024-44308.
Example: In the Microsoft SAS Token Leak (2023), researchers inadvertently published a Shared Access Signature token granting full access to an Azure Storage account and exposing 38TB of sensitive data. This NHI breach showed the risks of over-permissive, long-lived tokens.
Security best practices:
- Ensure all tokens and permissions are short-lived, scoped, and auto-expiring. That way, even if an attacker captures a valid token, it becomes useless almost immediately.
- Use device-bound tokens or certificate-based device auth.
- Detect impossible travel/concurrent sessions and trigger immediate token revocation.
- A cloud-native access management platform (like Apono) ensures all permissions are short-lived, scoped, and auto-expiring. A stolen token from an intercepted session becomes useless within minutes.
6. Agent-to-Target Hijacks (Compromised Agents & Telemetry)
An attacker with network access (or who exploits a vulnerability in an agent) can intercept or impersonate the agent to server telemetry and commands, hijacking workflows and observability channels.
Example: The Okta Support System Breach in 2023 saw attackers exploit a compromised NHI (a service account) to steal support artifacts containing customer credentials. Additionally, CVE-2025-1146 (CrowdStrike Falcon Linux component) illustrates how TLS validation bugs can enable MitM of agent to cloud traffic.
A potential MiTM attack exploiting this flaw could trick the vulnerable CrowdStrike sensor into accepting a malicious, non-legitimate server certificate. This attack would allow the attacker to intercept, decrypt, and manipulate the secure communication between the sensor and the CrowdStrike cloud, potentially compromising system confidentiality and integrity.
Security best practices:
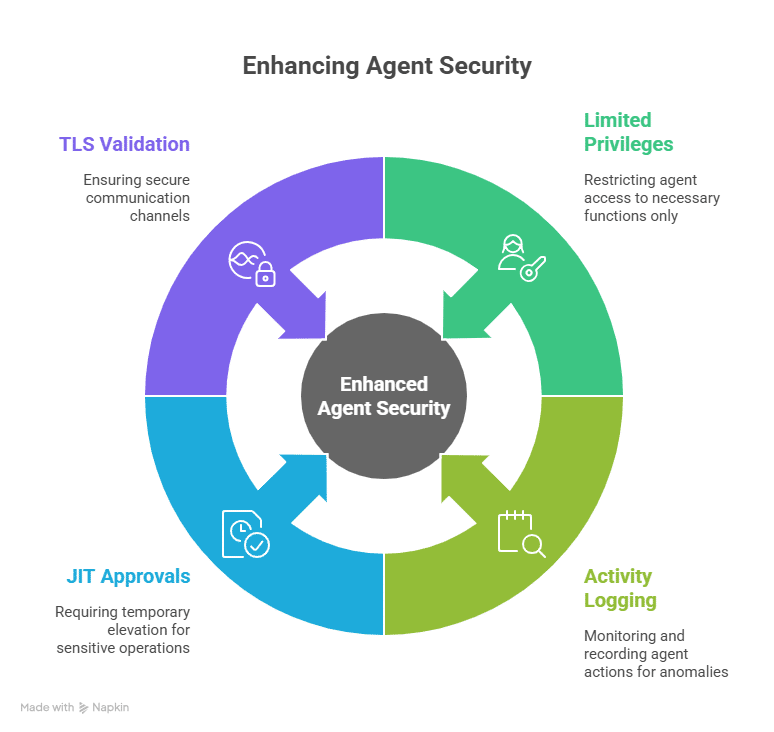
- Enforce strict TLS validation and mTLS for agent-to-cloud links.
- Limit agent privileges; require JIT elevation for sensitive operations.
- Log agent activity and alert on anomalous command sequences.
- Apono enforces JIT approvals on sensitive agent actions, so even a compromised agent account cannot escalate beyond its narrowly scoped, temporary role.
7. Naive Agent-to-Agent Protocols (Weak Inter-Agent Auth)
Simpler or unrecorded agent-to-agent protocols without mutual authentication or request signing enable MitM between agents and services in distributed systems. Such attacks may include context poisoning, agent impersonation, or exploiting an AI agent’s logic.
Example: Microsoft’s Taxonomy of Failure Modes in Agentic AI Systems warns how impostor agents could intercept agent communications. The research shows that an attacker could introduce an impostor AI agent, such as an impostor “email assistant,” into a network of cooperating agents. This malicious actor would then have the capability to intercept and alter legitimate communication between other actors, such that the attacker can inject new instructions and pilfer sensitive data without intervening directly by any human user.
Security best practices:
- Mandate mutual TLS and cryptographic signing for agent-to-agent calls; mandate strict key rotation.
- Adopt centralized identity for services (machine identities), per-call authorization, and least-privilege policies.
- Validate request provenance and use replay protection (nonces/timestamps) in protocols.
- Machine identity management should be centralized. JIT per-call permissions prevent overprivileged service accounts from being an ongoing MitM target.
- A cloud-native access management platform like Apono manages machine identities and issues per-call JIT access, ensuring overprivileged service accounts aren’t a standing MitM target.
Where legacy PAM relies on static roles and vault proxies, leaving windows of opportunity open for MitM actors, Apono operationalizes Zero Standing Privilege. That means every credential, token, or role is short-lived, scoped, and continuously verified—dramatically reducing the blast radius of a single interception.
Short-Lived Access, Long-Lasting Security With Apono
Man-in-the-middle attacks typically succeed when stolen credentials or tokens remain useful. The fastest prevention isn’t perfect encryption; it’s limiting how much data of value an attacker has. Make sessions transient, bind tokens to device and context, and identify proxying traffic so stolen credentials will decay or be revoked right away.
Operationally, focus on three levers: mandate phishing-immune MFA and device-bound authentication; use short-lived, auto-rotating tokens with per-call authorization and mTLS for traffic to services; and put high-risk activities behind human approvals and quick revocation playbooks. These steps keep attackers from turning a fleeting interception into a sustained breach.
Stolen tokens expire within minutes with Apono, preventing attackers from turning an interception into sustained access. Permissions expire automatically, machine identities are scoped per-call, and sensitive actions require approvals. Apono is built specifically for this approach: JIT access, automatically decaying permissions, scoped control over agents, and full audit trails reduce the blast radius in case of interceptions. See how temporary access turns the tables. Apono operationalizes zero trust by eliminating standing privileges across human and machine identities.
Book a demo and start making stolen credentials useless before they can be weaponized.