A Step-by-Step Guide to Creating a Data Security Policy

Ofir Stein
March 27, 2024
Failure to secure data is not an option. The risk of significant financial losses, operational downtime, reputational damage, and regulatory fines grows every year, and protecting your organization’s assets is more important than ever.
The average data breach cost rose to a staggering $4.45 million in 2023 and peaked at $11 million and $5.9 million in the healthcare and financial industries, respectively. Just one data breach can cause a major headache for your company, which is why it’s time to prioritize your data security policy.
What is a Data Security Policy?
A data security policy covers the administration of data within an organization, aiming to safeguard all data your company utilizes, manages, and retains. While a data security policy is not required by law, it helps your organization adhere to data protection regulations such as GDPR. These policies should cover all data (at rest and in transit), including on-premises storage devices, off-site locations, cloud services, and endpoints such as laptops or mobile devices.
Why Do You Need a Data Security Policy?
A data security policy benefits your business in many ways:
- Meet compliance requirements and comply with global standards like GDPR and ISO 27001.
- Build a culture of security awareness by clearly outlining best practices for managing data and helping all employees understand their level of responsibility.
- Prevent data breaches and avoid the loss of data and customer trust caused by security incidents, as well as legal and financial penalties.
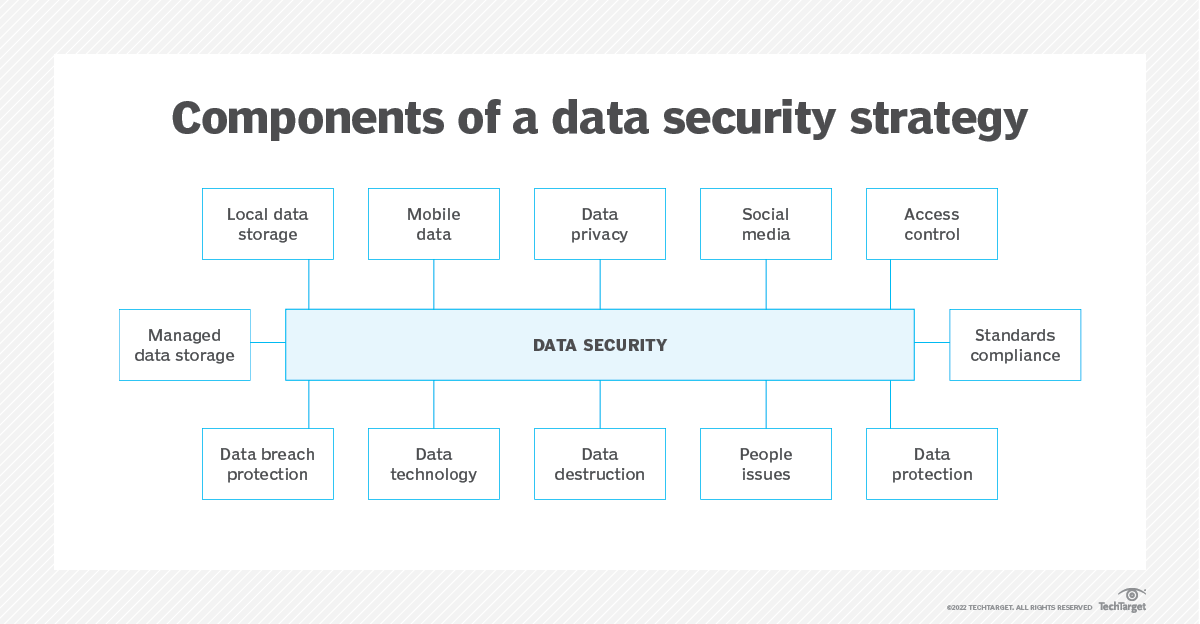
6 Essential Elements of a Data Security Policy
- Security tools: Any third-party tools you need to support policy implementation.
- Scope: The scope of the policy, who it affects, and how it integrates with other frameworks like identity governance.
- Inventory: Inventory of your organization’s data and who manages or maintains it
- Stakeholders: The stakeholders involved in the policy creation and who enforce it.
- Implementation roadmap: A rollout timeline, plus a timeline for regular policy reviews
- Clear policy objectives: Why is the policy needed, and what is the goal of implementing it?
A Step-by-Step Guide to Creating a Data Security Policy
Creating a data security policy involves several steps, including the following:
- Assessment and Analysis
Before developing a policy, you must assess your organization’s security needs. This step involves evaluating:
- The types of data you handle.
- The sensitivity of that data.
- The potential impact of a security breach.
Data classification is a useful tool in this process, allowing you to categorize data based on its level of sensitivity and define security controls for each category.
- Legal and Regulatory Compliance
Understanding the legal and regulatory requirements that apply to your industry is crucial for ensuring compliance with relevant laws, regulations, and industry standards on data security, such as GDPR, HIPAA, or PCI DSS. Different industries and jurisdictions have specific data protection standards, and failing to keep up with compliance could incur costly penalties.
- Define Data Classification
A data classification system is a fundamental component of a data security policy. It helps you categorize data based on its sensitivity and importance to your organization. This classification will guide the level of protection and access controls applied to each type of data.
- Start by identifying the different types of data your organization handles, such as personal information, financial data, intellectual property, or trade secrets.
- Classify each type of data based on confidentiality, integrity, and availability requirements.
- Once you have established your data categories, define the security controls for each category, like encryption, access controls, data retention policies, or data backup procedures.
- Ensure that the classification system is well-documented and communicated to all employees.
- Access Controls and Permissions
Controlling access to sensitive data is vital in preventing unauthorized disclosure or modification. Access control strategies include:
RBAC
Start by implementing role-based access control (RBAC). RBAC involves defining roles and responsibilities for data access and implementing appropriate authentication mechanisms for each. You can assign specific roles and permissions to individuals based on their responsibilities, ensuring that employees only have access to the data necessary to perform their duties.
MFA
Additionally, consider implementing multi-factor authentication (MFA) for accessing sensitive systems or data. MFA enhances security by mandating that users supply multiple forms of identification. For example, they can include a password and a unique code dispatched to their mobile device.
Encryption
Encryption is another essential security measure to protect data in transit and at rest. Implement encryption protocols, such as Secure Sockets Layer (SSL) or Transport Layer Security (TLS), to safeguard data. Use encryption methods like full-disk or file-level encryption for data at rest.
- Data Handling Procedures
Data handling procedures are crucial for data confidentiality, integrity, and availability. They encompass all stages of data lifecycle management: collecting, storing, transmitting, and disposing of data securely. You can use encryption methods, backup procedures, and guidelines for remote access.
- Incident Response Plan
An incident response plan (IRP) defines how to handle security incidents and data breaches quickly. It outlines steps for detecting, reporting, and responding to security breaches. Best practices for developing a great incident response plan include:
- Defining responsibilities of key stakeholders.
- Communication protocols, such as who to notify and what information to share.
- Step-by-step procedures for handling incidents.
- Scheduling regular IRP reviews and updates.
- Criteria for isolating or shutting down affected systems.
- Employee Training and Awareness
Human error remains one of the primary causes of data breaches. So, educating employees on data best practices is essential for minimizing the risk of unauthorized access and building a culture of cybersecurity awareness.
Regular training sessions and awareness campaigns can reinforce good security practices. Training programs should cover topics such as password hygiene, recognizing phishing attempts, secure handling of sensitive information, and reporting security incidents.
You can tailor the training to employees’ roles and responsibilities and implement regular top-ups to make sure they remain vigilant.
- Regular Audits and Reviews
Regular security audits and assessments help you achieve ongoing compliance and identify security gaps. During security audits, you can introduce measures like scanning for security vulnerabilities, penetration testing, and reviewing access logs, plus implement procedures for auditing and reviewing the effectiveness of the data security policy. As technology, threats, and regulations evolve, it is essential to stay up to date and adapt your security measures accordingly.
- Documentation and Communication
Document the data security policy in a clear and easily accessible format. Ensure all employees are aware of the policy and provide channels for them to seek clarification or report concerns.
- Continuous Improvement
Data security is an ongoing process. You can continuously identify areas for improvements or updates and amend the policy based on feedback, the detection of emerging threats, and changes in data handling requirements.
You can also monitor security metrics, such as the number of security incidents or vulnerabilities detected, to assess the effectiveness of your security controls. Plus, it’s essential to implement a feedback loop for employees to report potential security gaps.
Managing Data Security Policies with Apono
Data security is a critical concern for businesses of all sizes and industries. With the growing number of cyber threats, you must take steps to protect information from unauthorized access, disclosure, alteration, or destruction.
Apono, The DevSecOps platform, allows you to enforce security policies from a single location across all databases, data warehouses, and data lakes.
Get started with Apono for free.




