Top 10 NHI Management Tools in an AI World

The Apono Team
November 25, 2025
In today’s AI-driven world, machine identities are multiplying faster than humans can manage them. Every API key and automation script is a digital identity, often with standing access privileges that attackers can exploit through leaked credentials or misconfigured policies.
Recent research shows that non-human identities (NHIs) now outnumber human users by more than 80:1 across enterprise cloud environments. Yet, traditional IAM platforms focus on humans, not the millions of agents and service accounts powering modern software delivery.
NHI management tools are changing the landscape, bringing lifecycle automation, Zero Trust, and least privilege enforcement to the table.
What are NHI management tools?
Non-human identity (NHI) management tools discover and monitor machine identities: the bots, APIs, service accounts, microservices, and Agent2Agent processes interacting with your systems. Like human users, they often rely on service principles and certificates to authenticate workloads and CI/CD pipelines. But unlike humans, they often operate autonomously and at a massive scale, making governing them an equally huge challenge.
NHI management tools integrate with cloud IAM systems and CI/CD platforms to dynamically adjust access scopes and programmatically rotate credentials. By managing permissions dynamically and in real time, NHI management tools eliminate standing access and ensure every agent and API operates under the principle of Zero Trust.
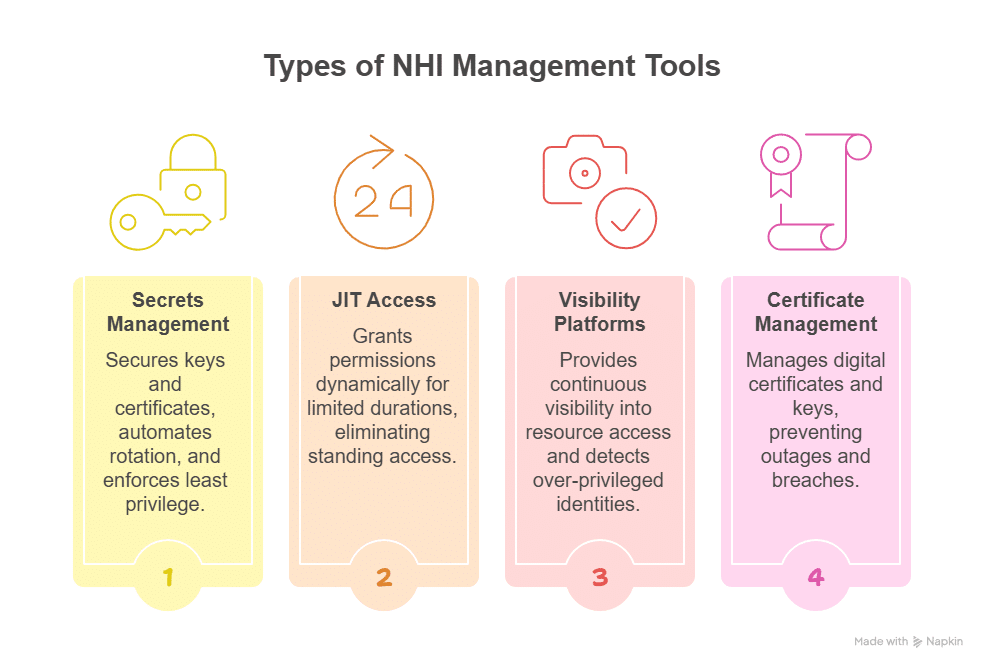
Types of NHI Management Tools
The NHI management landscape is broad, with different tools solving different layers of the identity problem. The best platforms combine features from multiple categories to unify discovery, access, automation, and auditability. Different types include:
Secrets and Credential Management Tools
These solutions secure the keys, tokens, and certificates that machine identities use to authenticate. They automate credential rotation and detect hardcoded secrets in source control (e.g., GitHub and GitLab).
Just-In-Time (JIT) and Access Governance Tools
JIT access management tools grant permissions dynamically: only when needed and for a limited duration. These solutions eliminate standing access and integrate with human-in-the-loop workflows or policy automation. Leaders in this category bring JIT and Just-Enough Privilege (JEP) to both human and non-human identities across cloud-native environments.
Visibility and Risk Analytics Platforms
These platforms provide continuous visibility into who (or what) can access which resources. They map permission sprawl and detect over-privileged machine identities, flagging anomalous access behavior. Some emerging solutions also leverage AI pen testing to simulate attacks by autonomous agents, uncovering hidden privilege escalation.
Machine Identity and Certificate Management Tools
Focused on the lifecycle of digital certificates and keys, these tools prevent outages and credential-related breaches by automating machine identity lifecycle management. The best solutions facilitate automated certificate enrollment via APIs or PKI integration.
Benefits of NHI Management Tools
- Enforced Least Privilege & JIT Access: Grant time-bound, context-aware permissions to eliminate standing access and minimize identity-based attack surfaces.
- Continuous Compliance: Simplify SOC 2, HIPAA, GDPR, and CCPA audits with automated logs, approval trails, and revocation workflows.
- Complete Visibility: Centralize identity data across clouds, pipelines, and AI environments to detect over-privileged or stale credentials.
- Stronger Security Posture: Prevent credential misuse, man-in-the-middle attacks, privilege escalation, and lateral movement through automated rotation and least-privilege policies.
- Faster Operations: Replace ticket-based access requests with self-service, policy-driven automation, reducing friction for DevOps and security teams.
- Automated Key Rotation & Revocation: Ensure short-lived credentials to reduce the risk of token misuse and standing access.
Key Features to Look For in an NHI Management Tool
Choosing the right NHI management platform means finding one that delivers
- Comprehensive Identity Discovery: Automatically detect and inventory all non-human identities, including bots, APIs, and service accounts created through AI code generation, across cloud and CI/CD environments.
- Secrets & Credential Lifecycle Management: Securely store, rotate, and revoke keys, tokens, and certificates to eliminate hardcoded or expired credentials.
- Just-In-Time (JIT) & Just-Enough Access (JEA): Grant permissions dynamically and revoke them automatically once tasks are complete, minimizing standing access.
- Policy-Based Access Governance: Define and enforce access policies based on role, context, and environment for consistent compliance and zero-trust enforcement.
- Continuous Monitoring & Auditing: Track access requests, approvals, and privilege escalations in real time with automated logs and audit-ready reporting.
- Integrations with DevOps & Cloud Stacks: Connect seamlessly with AWS, Azure, GCP, Kubernetes, GitHub, and automation workflows via API or ChatOps.
10 Top NHI Management Tools
1. AppViewX
AppViewX is an enterprise-grade machine identity and automation platform designed to secure and orchestrate digital certificates and IoT identities across multi-cloud infrastructures.
Main Features:
- Crypto-agnostic security, supporting PKI, HSM, and key vault integrations
- Integrates with CI/CD pipelines and ITSM tools for continuous compliance
- Automates issuance, renewal, and revocation of SSL/TLS certificates and SSH keys
Price: By inquiry.
Review: “The best things are [the ease] of onboarding servers [and] management of certificates.”
Best For: Enterprises managing large volumes of digital certificates and IoT identities.
2. Apono
Apono is a cloud-native access management solution built to secure both human and non-human identities (NHIs) through automated Just-In-Time (JIT) access and least-privilege enforcement. Designed for DevOps-driven organizations, Apono removes standing permissions across cloud, SaaS, and data resources without slowing developers.
Main Features:
- Automated Just-In-Time (JIT) Access Flows: Dynamically grant and revoke permissions for both human and machine identities based on contextual policies.
- Auto-Expiring Permissions: Eliminate risky standing access by ensuring every permission has a defined time-to-live.
- Break-Glass and On-Call Flows: Empower teams to resolve production issues quickly and securely with pre-approved emergency access.
- Granular Access for NHIs: Discover, classify, and govern non-human identities, such as service accounts and API tokens, across multi-cloud environments.
Price: Get in touch with the Apono team for tailored pricing.
Review: “As head of IT, it gives me peace of mind when I know that only the right users get proper access to the system’s DB at the right time; with Apono, I don’t need to worry about managing DB privileges since Apono makes sure that the key is automatically revoked upon duration completion.”
Best For: Cloud-native and DevOps-driven organizations that need to enforce JIT and least-privilege access across both human and non-human identities.
3. Entro Security
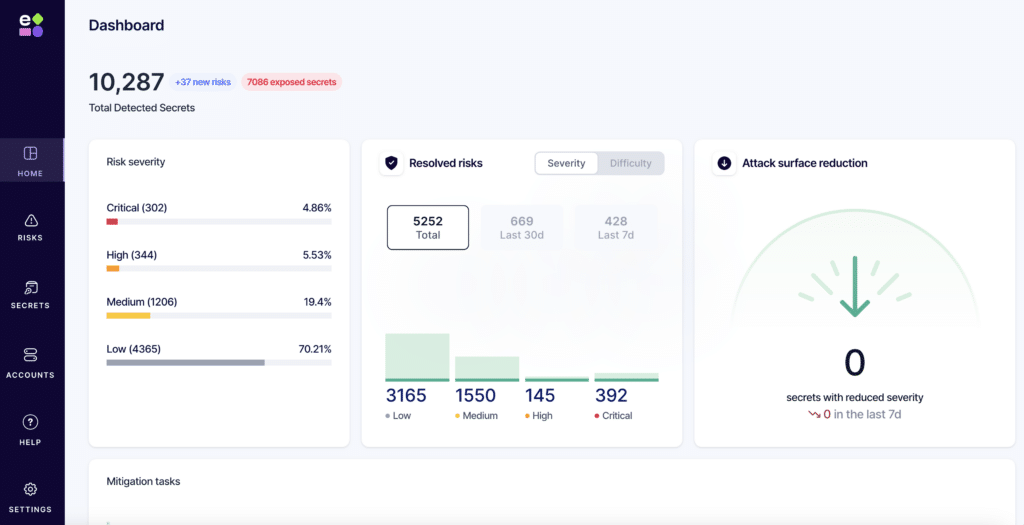
Entro is a secrets and machine identity security platform that provides full visibility into where secrets live across code and cloud environments. It continuously monitors them for misuse and privilege escalation.
Main Features:
- Uses contextual intelligence to detect suspicious secret usage or credential abuse
- Works with AWS Secrets Manager, Azure Key Vault, HashiCorp Vault, Kubernetes, and more
- Consolidates insights from vaults and cloud providers for unified visibility
Price: By inquiry.
Review: “Entro has helped us increase the visibility of secrets and take the appropriate actions.”
Best For: Security and DevOps teams that want comprehensive visibility into secrets sprawl.
4. CyberArk Machine Identity Security
CyberArk’s offering is an enterprise-grade platform providing centralized visibility and control over every machine identity, whether it’s a container, workload, service account, or CI/CD pipeline credential.
Main Features:
- Integrates with CyberArk Conjur and Secrets Manager for unified control over machine-to-machine authentication
- Enforces contextual, policy-based access for machine identities
- Identifies all active and orphaned machine identities across multi-cloud environments
Price: By inquiry.
Review: “We have automated the detection, sorting, and onboarding of new privileged accounts, freeing up man-hours.”
Best For: Large enterprises already using CyberArk’s PAM needing enterprise-grade control and auditing of machine identities.
5. Aembit
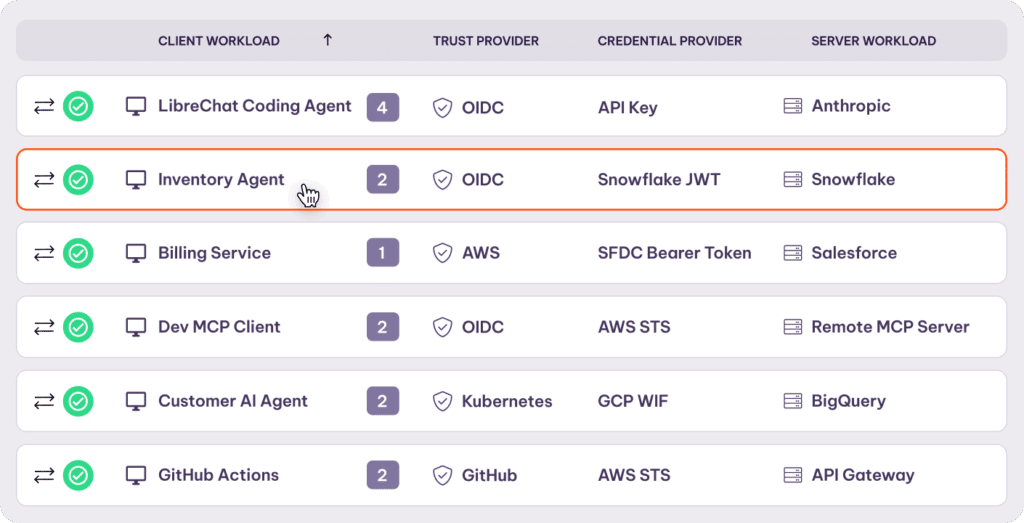
Next up is Aembit, a Workload Identity and Access Management (WIAM) platform that enables secure, policy-based authentication and authorization between applications and services.
Main Features:
- Replaces static secrets with cryptographic trust relationships
- Works natively with Kubernetes, AWS, Azure, GCP, Okta, and major CI/CD platforms
- Enforces least-privilege access policies for each workload, based on real-time context
Price: Free trial available. $20/client/month for teams and custom pricing for enterprises.
Review: None available.
Best For: Teams implementing WIAM to secure authentication and authorization.
6. Transmit Security

As an identity orchestration and authentication platform, Transmit extends beyond user access to include machine identity governance. While best known for passwordless and customer identity solutions, Transmit’s platform also helps enterprises secure and monitor NHIs.
Main Features:
- Eliminates password-based authentication for workloads and APIs using secure, identity-bound tokens
- Generates detailed logs and access reports to align with regulations like SOC 2
- Enforces least-privilege access based on risk level
Price: By inquiry.
Review: “[I like the] agility provided for making the changes in the process of authentication and authorization.”
Best For: Organizations looking to unify human and machine authentication through passwordless access.
7. Jit
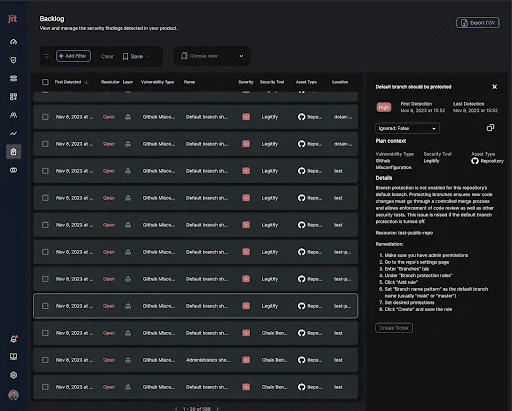
Jit is a developer-first security orchestration platform that delivers Minimum Viable Security (MVS) directly within the CI/CD pipeline. It acts as an automation layer across GitHub and AWS, embedding essential security practices like code scanning.
Main Features:
- Monitors AWS roles and permissions to maintain minimal required access across cloud environments
- Detects and remediates misconfigurations and exposed credentials
- Prioritizes ease of adoption by embedding security directly into existing DevOps workflows
Price: The Growth package is $50/developer/month, and custom pricing is available for enterprises..
Review: “Jit makes it very easy to integrate security into the development workflow without adding too much overhead.”
Best For: Developer-centric teams seeking to embed security automation directly into their CI/CD pipelines.
8. Entrust
As an established player in the digital identity and credential management space, Entrust unifies PKI (Public Key Infrastructure) and certificate lifecycle management. It is well-suited for organizations managing large numbers of NHIs across distributed cloud ecosystems.
Main Features:
- Supports advanced cryptography for device, workload, and application identity verification
- Works with AWS, Azure, GCP, and Kubernetes clusters to ensure consistent certificate policies
- Automates the issuance, renewal, and revocation of digital certificates
Price: By inquiry.
Review: “We use Entrust to serve our two-factor authentication needs, and it works perfectly.”
Best For: Enterprises requiring robust PKI and digital certificate lifecycle management.
9. HashiCorp Boundary
HashiCorp Boundary is an open-source secure access management tool designed to control privileged access to critical systems without exposing credentials or managing static network-based access lists.
Main Features:
- Authenticates users and applications through trusted identity providers (IdPs)
- Works with HashiCorp Vault to generate short-lived, just-in-time credentials
- Supports multi-cloud and hybrid setups with API-driven integration for DevOps workflows
Price: By inquiry. There are Pay-as-You-Go, Flex, and Enterprise Self-Managed options.
Review: None available.
Best For: Infrastructure and platform teams that want to replace VPN- or SSH-based access with JIT.
10. Securiti
Last but not least, Securiti is an AI-powered data and identity security platform that helps enterprises automate governance and access across hybrid and multi-cloud environments. While best known for its Data Command Center, Securiti also delivers strong capabilities in machine identity discovery.
Main Features:
- Uses artificial intelligence to detect anomalous access behavior
- Continuously monitors and enforces least-privilege access policies for both users and service identities
- Enables full visibility into identity-to-data relationships across clouds
Price: By inquiry.
Review: “I really appreciate how Securiti Data Command provides a holistic view of data posture and security management across the organization.”
Best For: Enterprises seeking AI-driven visibility and governance over how human and non-human identities access sensitive data.
Securing the Next Generation of Identities With Apono
The ratio of machine identities to human users is rapidly growing, transforming identity security into a scalability problem. Every unmanaged credential or bot token increases the risk of breach and compliance failure.
Legacy PAM and IAM tools weren’t designed for this level of automation. Apono’s cloud-native, API-first approach brings identity governance into the AI era. Apono automates JIT and JEP access flows to minimize privilege exposure without slowing down development pipelines.
Start with a free NHI Cloud Access Assessment to identify privilege risks across your cloud stack and learn how to automate them with Apono.





