What is RBAC?
Role-Based Access Control (RBAC) is a method for managing and controlling access to computer systems and data within an organization. It is a widely used access control model that is designed to improve security and simplify the management of permissions and user access.
In Role-Based Access Control, access permissions are tied to roles, and users are assigned to one or more roles based on their job responsibilities or functions within the organization. Here’s how it works:
- Roles: Roles represent different job functions or responsibilities within an organization. For example, in a healthcare system, you might have roles like “Doctor,” “Nurse,” “Administrator,” and “Patient.”
- Permissions: Permissions are specific actions or operations that users can perform within a system or on specific resources. These permissions are associated with roles. For instance, a “Doctor” role might have permissions to view patient records and prescribe medications.
- Users: Users are individuals who are granted access to the system. Instead of assigning permissions directly to users, RBAC associates permissions with roles. Users are then assigned one or more roles, which determine their access rights.
- Role Assignment: The process of assigning roles to users is typically managed by administrators or system administrators. When a user is assigned a particular role, they inherit the permissions associated with that role.
- Access Control: Once roles are assigned to users, the system enforces access control based on those roles. Users can only perform actions for which they have been granted permissions through their assigned roles. This simplifies access management, as administrators can modify permissions at the role level rather than for individual users.
Challenges of Role Based Access Control
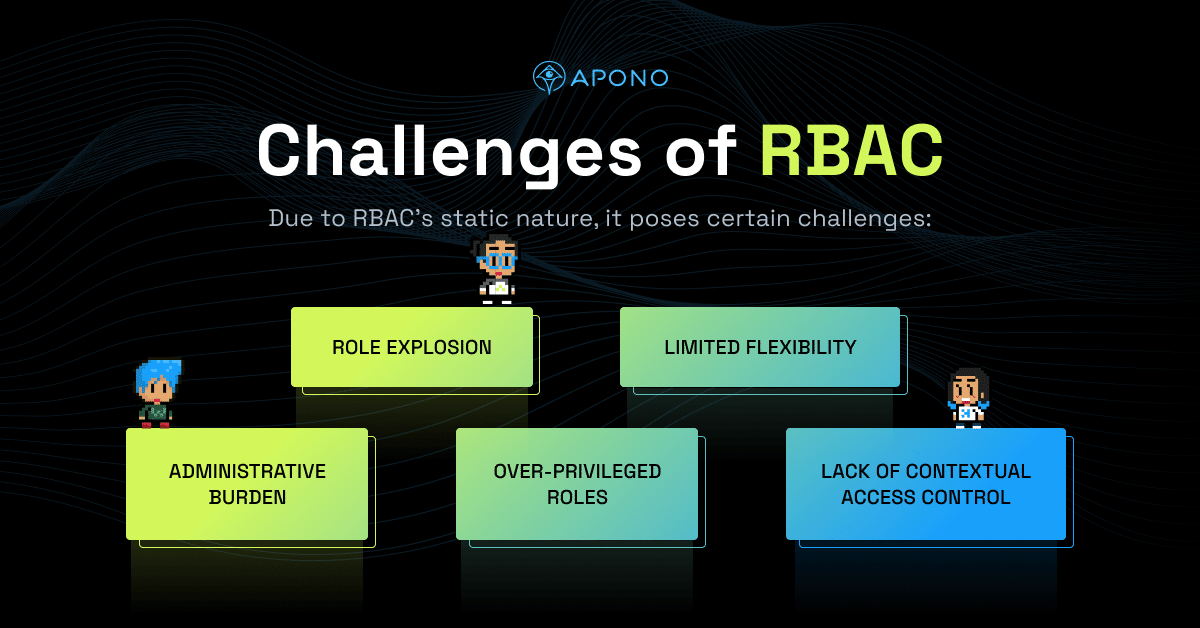
While Role-Based Access Control (RBAC) offers several advantages, it does come with certain challenges, particularly its static nature. The static nature of RBAC refers to the fact that role assignments and permissions are typically defined and assigned in advance, without considering dynamic factors or changing access requirements. This static approach can pose challenges in certain scenarios:
- Limited Flexibility: RBAC can struggle to accommodate dynamic access needs or ad hoc changes in user responsibilities. If a user requires temporary or one-time access to a specific resource outside their assigned role, it may be difficult to grant that access without modifying their role or assigning additional permissions.
- Over-Privileged Roles: To accommodate exceptional access requirements, roles may end up with broad permissions that exceed the needs of most users assigned to that role. This can lead to over-privileged roles, increasing the risk of potential misuse or unauthorized access if a user’s account is compromised.
- Role Explosion: In some cases, organizations may need to create numerous roles to accommodate the diverse access requirements of different users or groups. This can result in a large number of roles to manage, leading to increased complexity and administrative overhead.
- Lack of Contextual Access Control: RBAC primarily relies on static role assignments without considering contextual factors such as time, location, or specific conditions. This can limit the ability to enforce access controls that adapt based on the changing context or specific circumstances.
- Administrative Burden: As organizations grow or change, the administrative effort required to maintain and update RBAC configurations can become substantial. Role assignments and permissions need to be regularly reviewed and updated, potentially leading to increased administrative complexity.
To address these challenges, organizations can consider incorporating more dynamic access control mechanisms alongside Role-Based Access Control. This could include implementing Just-In-Time (JIT) access, Attribute-Based Access Control (ABAC), or dynamic role assignment based on specific user attributes or conditions. These approaches provide more flexibility and adaptability in managing access while complementing the structure and benefits of RBAC.
By combining RBAC with dynamic access control mechanisms, organizations can strike a balance between providing necessary access and maintaining security, enabling a more agile and context-aware approach to access management.
About Apono
Apono is a leading provider of access management solutions that helps address the limitations of RBAC (Role-Based Access Control) and enhances access control with dynamic mechanisms. With Apono’s platform, organizations can leverage Just-In-Time (JIT) access and Attribute-Based Access Control (ABAC) functionalities to achieve a more flexible and adaptable access management approach.
Apono’s JIT access capability allows organizations to grant temporary access to specific resources based on immediate needs, overcoming the static nature of RBAC. By incorporating JIT access, organizations can improve security by reducing the attack surface and minimizing the risk of unauthorized access.
In addition, Apono integrates ABAC, enabling organizations to define access control policies based on attributes such as user attributes, context, or specific conditions. This granular and contextual access control enhances flexibility by considering factors like time, location, and data sensitivity. Apono’s ABAC functionality provides organizations with the flexibility to manage access permissions based on dynamic attributes and changing requirements.
By combining Role-Based Access Control with Apono’s dynamic access mechanisms, organizations can achieve a comprehensive and adaptable access management solution. Apono’s platform empowers organizations to provide timely and context-aware access to resources while ensuring security and compliance. Experience the benefits of Apono’s enhanced access control and improve your organization’s access management strategy.
FAQs
-
What is the purpose of Role Based Access Control (RBAC)?
RBAC restricts network access according to the users’ roles in an organization. This method ensures that employees only access information relevant to their job roles and prevents them from accessing unrelated or confidential information.
-
What is Role Based Access Control (RBAC)?
A primary method of secured access control is Role-based access control (RBAC) – a system that restricts network access solely based on a person’s role within the organization. Giving attribution between the role and the access required by the user.
-
What is the purpose of Role Based Access Control?
RBAC restricts network access according to the users’ roles in an organization. This method ensures that employees only access information relevant to their job roles and prevents them from accessing unrelated or confidential information.
-
What is the benefit of RBAC in Microsoft Azure?
Azure role-based access control (Azure RBAC) is a role-based authorization system specially operated on Azure resource manager, enabling fine-grained access management of Azure resources. The unique aspect of Azure RBAC is that it allows one to separate employees’ duties and enable access that’s sufficient to complete their tasks.
-
What are Azure RBAC roles?
Azure Role Based Access Control (RBAC) helps one manage and define the individuals’ access to Azure resources, their limits, and which resources they can use. The authorization system is built and operated on Azure resource manager, allowing users granular access management to Azure resources.
-
What are the three types of RBAC controls in Azure?
Azure RBAC allows administrators and security staff to manage roles effortlessly. Essentially, Azure has three different role levels: Reader, Contributor, and Owner.
-
How is RBAC implemented?
Here’s how you can implement RBAC:
– Create a coherent map aligning roles with resources so that users can have the required access to complete tasks.
– Form security groups representing each job role.
– Assign and add individuals to relevant roles and groups. -
What are two types of Role Based Access Control Lists?
Filesystem and Networking ACL are the two prominent types of ACL. Filesystem filters access to files and directories by instructing the operating system about the access level and privileges required for a user to execute a task. In contrast, networking ACL only filters access to a network.
-
What is an example of RBAC?
One common example of RBAC is related to a set of permissions, allowing users to either read, edit, or delete articles in writing software. The two roles, in this case, are Writer and Reader, and their permission levels are displayed in a truth table. You can also set the permission level of each individual using the truth table.
-
Which type of access controls can be role-based?
RBAC restricts network access according to the users’ roles in an organization. This method ensures that employees only access information relevant to their job roles and prevents them from accessing unrelated or confidential information.
-
Which type of access controls can be Role Based or task based?
Role-based access control and task-based access control are known as mandatory access or non-discretionary controls. These access controls match the information accessibility level based on roles or tasks instead of individual users.