Task-Based Access Control (TBAC)
Task-based access control (TBAC) is a security model that focuses on granting access rights based on specific tasks or activities rather than providing broad, long-term access privileges. In the context of Just-In-Time (JIT) access, TBAC plays a significant role in enhancing security and reducing the attack surface.
With TBAC, access is granted to users only when they require it to perform a specific task or activity. This approach aligns well with JIT access, where temporary access is provided on-demand for a limited time frame. Instead of granting continuous access to resources, users are given access rights based on their immediate needs.
The key characteristics of TBAC in JIT access include:
- Granular Access Control: TBAC ensures that access permissions are assigned at a fine-grained level, focusing on the specific tasks or activities that users need to perform. This reduces the risk of granting excessive privileges or access beyond what is necessary.
- Time-Limited Access: TBAC in JIT access involves providing access rights for a predefined period based on the duration required to complete the task. Once the task is completed or the time limit expires, access is automatically revoked, minimizing the window of opportunity for potential security breaches.
- Just-In-Time Provisioning: TBAC and JIT access work together to enable the provisioning of access rights in real-time as users request them. This eliminates the need for users to have long-term access privileges and ensures that access is granted only when it is actually needed.
- Access Revocation: Once the task or activity is completed or the designated time period ends, access rights are automatically revoked. This ensures that access is no longer available beyond what is required, reducing the risk of unauthorized or prolonged access.
By combining TBAC with JIT access, organizations can achieve a more secure and efficient access management process. Users have access to the resources they need precisely when they need them, and access privileges are automatically revoked when no longer required. This approach minimizes the attack surface, reduces the potential for unauthorized access, and enhances overall security posture.
Apono, as a leading provider of Cloud PAM solutions, recognizes the importance of task-based access control (TBAC) within the context of Just-In-Time (JIT) access. Apono’s innovative API-based approach allows organizations to deploy their Cloud PAM solution rapidly, granting full access visibility to all privileged resources without acting as a proxy for data. By offering a non-disruptive implementation, Apono ensures that end users can continue working seamlessly with their privileged resources while benefiting from enhanced security and compliance. With Apono, organizations can leverage the power of TBAC and JIT access to effectively manage and secure privileged access, reduce attack surfaces, and mitigate the risks associated with excessive or prolonged access privileges.
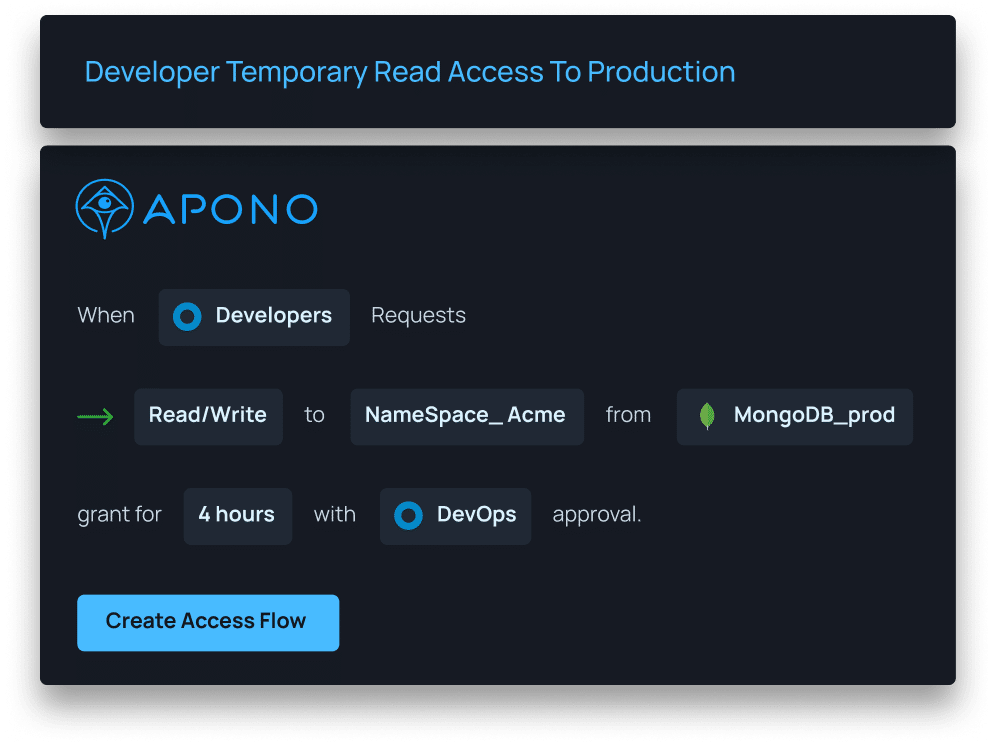
Here is an example of an Task Based Access Workflow in Apono:
FAQs
-
What is Task-based access control?
Task-based access control (TBAC) is an access control model that focuses on granting permissions to users based on the specific tasks or operations they need to perform within a system or application. In TBAC, access decisions are made based on the tasks or functions that users are authorized to perform, rather than the traditional approach of granting permissions based on roles or user attributes.
In TBAC, each task or operation within a system is associated with a set of permissions or privileges. Users are assigned specific tasks or sets of tasks, and their access is restricted to only those tasks for which they have been authorized. This approach allows for more fine-grained access control, as users are granted access only to the specific functions they need, rather than having broader access based on their roles.
TBAC can be particularly useful in scenarios where there is a need for flexible access control, especially in complex systems with a large number of tasks or operations. It enables administrators to define and manage access permissions at a granular level, ensuring that users have the necessary access rights to perform their assigned tasks while preventing unauthorized access to other functions.
By implementing TBAC, organizations can enhance security, reduce the risk of data breaches, and enforce the principle of least privilege. It provides a more tailored and dynamic approach to access control, allowing for efficient management of user permissions based on the tasks they need to accomplish within a system or application.
-
Which type of access controls can be role based or task-based?
Only non-discretionary controls. Role-based access control and task-based access control are examples of non-discretionary controls (or Mandatory Access Controls) since they assign information to roles or tasks instead of individual users.
-
What are the types of Task-based access control?
The following are the types of TBAC:
- Discretionary Access Control
- Rule-Based Access Control
- Mandatory Access Control
- Role-Based Access Control